This article is courtesy of the the following, but not limited to Germán Fernández, Mandiant, LitMoose, Chris Duggan, Dray Agga, Florian Roth
Introduction
MOVEit Transfer is a managed file transfer (MFT) solution developed by Ipswitch. Ipswitch is a subsidiary of Progress Software Corporation.
MFT allows enterprise to securely transfer files between organizations and/or customers using SFTP, ACP and HTTP baed uploads. This software can be deployed as an on-prem solution or a cloud SaaS platform managed by the developer.
Zero Day
First reports I knew about this was when it as reported by BleepingComputer. A number of organization has been breached and as of writing this article, no ransom has been demanded yet.
Ipswitch has discovered a vulnerability in MOVEit Transfer which leads to escalated privilege and potential unauthorised access to systems.
The current solution, while patching is being done is to block port 80/443. But of course, blocking these ports will render the software useless. That said, SFTP and FTP/S can continue to be used (which runs on different ports).
In pone report, there were 2500 identified MOVEit Transfer servers, majority is located in the US and some scattered all over the world.
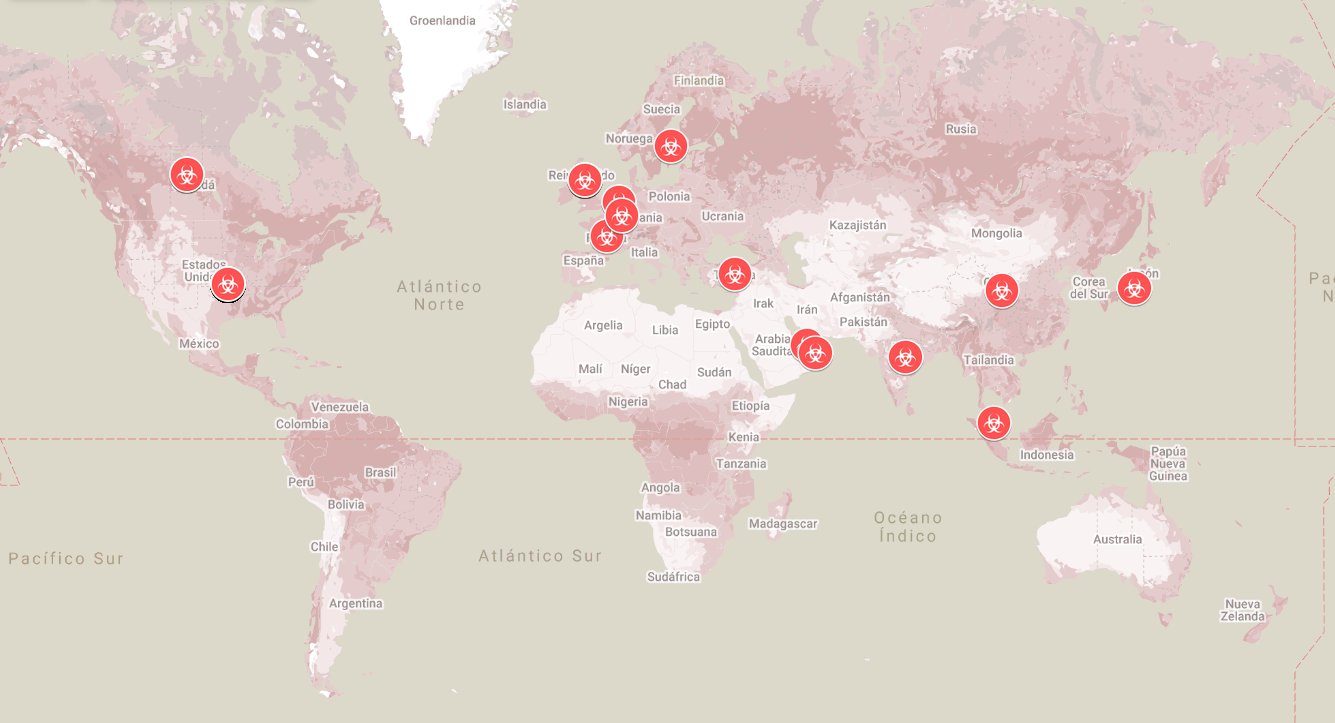
The software maker has just released patches for the security hole. There's now MOVEit Transfer 2023.0.1, 2022.1.5, 2022.0.4, 2021.1.4, and 2021.0.6 available to fix the insecure code.
Exploitation & Detection
According to the MOVEit notification, a SQL injection (SQLi) vulnerability within the application could allow escalated privileges and unauthorized access to the environment. Based on TrustedSec’s analysis of the backdoor seen, a successful attack could allow unauthenticated remote access to any folder or file within a MOVEit system.
There has been reported numerous exploitation seen in the wild. One clear evidence is the existence of the file "human2.aspx". But do remember that attackers may change the file name and that this name isn't cast in stone.
The webshell code would first determine if the inbound request contained a header named X-siLock-Comment, and would return a 404 "Not Found" error if the header was not populated with a specific password-like value.
Here's some method to check for validation (own research)
- Verify that the host corresponds to a MOVEit Transfer instance (source code).
- Connect to a non-existent URL (for example suresh.aspx and save the response)
- Connect to the path of the backdoor "/human2.aspx" and save the response
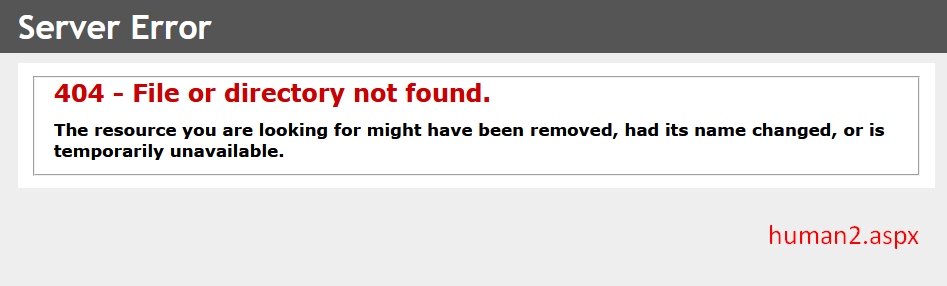
If the last response is different from the first one AND the server returns 404 AND response type is "text/html" AND content-size is 1245 AND page title is "404 - File or directory not found" = Potentially face a compromised instance.
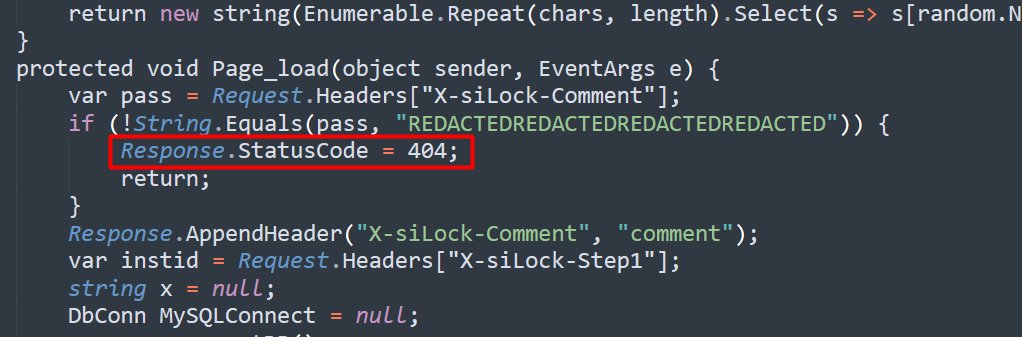
Also look inside "C:\MOVEit\Transfer\wwwroot\"
Andy has written a python script webshell checker which you can use - https://github.com/ZephrFish/MoveIT-WebShellCheck
If you deploy Yara rule, you may get sample rules to deploy nere - https://github.com/Neo23x0/signature-base/blob/master/yara/vuln_moveit_0day_jun23.yar#L2
Mandiant has named the backdoor LEMURLOOT. LEMURLOOT is a web shell written in C# tailored to interact with the MOVEit Transfer platform. The malware authenticates incoming connections via a hard-coded password and can run commands that will download files from the MOVEit Transfer system, extract its Azure system settings, retrieve detailed record information, create and insert a particular user, or delete this same user. Data returned to the system interacting with LEMURLOOT is gzip compressed.
IOC
These are some Clop C2 IP observed on the compromised boxes.
- 5.252.23.116
- 5.252.25.88
- 84.234.96.104
- 89.39.105.108
- 138.197.152.201
- 148.113.152.144
- 198.12.76.214
- 209.97.137.33
- 209.222.103.170
- 104.194.222.107
- 146.0.77.141
- 146.0.77.155
- 146.0.77.183
- 162.244.34.26
- 162.244.35.6
- 179.60.150.143
- 185.104.194.156
- 185.104.194.24
- 185.104.194.40
- 185.117.88.17
- 185.162.128.75
- 185.174.100.215
- 185.174.100.250
- 185.181.229.240
- 185.181.229.73
- 185.183.32.122
- 185.185.50.172
- 188.241.58.244
- 193.169.245.79
- 194.33.40.103
- 194.33.40.104
- 194.33.40.164
- 198.27.75.110
- 206.221.182.106
- 209.127.116.122
- 209.127.4.22
- 45.227.253.133
- 45.227.253.147
- 45.227.253.50
- 45.227.253.6
- 45.227.253.82
- 45.56.165.248
- 5.149.248.68
- 5.149.250.74
- 5.149.250.92
- 5.188.86.114
- 5.188.86.250
- 5.188.87.194
- 5.188.87.226
- 5.188.87.27
- 5.34.180.205
- 62.112.11.57
- 62.182.82.19
- 62.182.85.234
- 66.85.26.215
- 66.85.26.234
- 66.85.26.248
- 79.141.160.78
- 79.141.160.83
- 84.234.96.31
- 89.39.104.118
- 91.202.4.76
- 91.222.174.95
- 91.229.76.187
- 93.190.142.131
- 188.241.58.0/24
- 5.252.189.0/24
- 5.252.190.0/24
- 5.252.191.0/24
These are some of the other types of artefacts observed.
- File - C:\Windows\TEMP[random][random].cmdline
- File - C:\Windows\Microsoft.NET\Framework64\v4.0.30319\Temporary ASP.NET Files\root[random][random]\App_Web_[random].dll
- File - human2.aspx
- File - human2.aspx.lnk
- HTTP - POST /moveitisapi/moveitisapi.dll
- HTTP - POST /guestaccess.aspx
- HTTP - POST /api/v1/folders/[random]/files
- HTTP - GET /human2.aspx
- User Account - Health Check Service
- User Agent - Mozilla/5.0+(Windows+NT+10.0;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/105.0.5195.102+Safari/537.36
- Domain - dojustit[.]mooo[.]com
SHA256 Hash
- 0b3220b11698b1436d1d866ac07cc90018e59884e91a8cb71ef8924309f1e0e9
- 110e301d3b5019177728010202c8096824829c0b11bb0dc0bff55547ead18286
- 1826268249e1ea58275328102a5a8d158d36b4fd312009e4a2526f0bfbc30de2
- 2ccf7e42afd3f6bf845865c74b2e01e2046e541bb633d037b05bd1cdb296fa59
- 58ccfb603cdc4d305fddd52b84ad3f58ff554f1af4d7ef164007cb8438976166
- 98a30c7251cf622bd4abce92ab527c3f233b817a57519c2dd2bf8e3d3ccb7db8
- a8f6c1ccba662a908ef7b0cb3cc59c2d1c9e2cbbe1866937da81c4c616e68986
- b5ef11d04604c9145e4fe1bedaeb52f2c2345703d52115a5bf11ea56d7fb6b03
- cec425b3383890b63f5022054c396f6d510fae436041add935cd6ce42033f621
- ed0c3e75b7ac2587a5892ca951707b4e0dd9c8b18aaf8590c24720d73aa6b90c
- 0b3220b11698b1436d1d866ac07cc90018e59884e91a8cb71ef8924309f1e0e9
- 110e301d3b5019177728010202c8096824829c0b11bb0dc0bff55547ead18286
- 1826268249e1ea58275328102a5a8d158d36b4fd312009e4a2526f0bfbc30de2
- 2ccf7e42afd3f6bf845865c74b2e01e2046e541bb633d037b05bd1cdb296fa59
- 58ccfb603cdc4d305fddd52b84ad3f58ff554f1af4d7ef164007cb8438976166
- 98a30c7251cf622bd4abce92ab527c3f233b817a57519c2dd2bf8e3d3ccb7db8
- a8f6c1ccba662a908ef7b0cb3cc59c2d1c9e2cbbe1866937da81c4c616e68986
- b5ef11d04604c9145e4fe1bedaeb52f2c2345703d52115a5bf11ea56d7fb6b03
- cec425b3383890b63f5022054c396f6d510fae436041add935cd6ce42033f621
- ed0c3e75b7ac2587a5892ca951707b4e0dd9c8b18aaf8590c24720d73aa6b90c
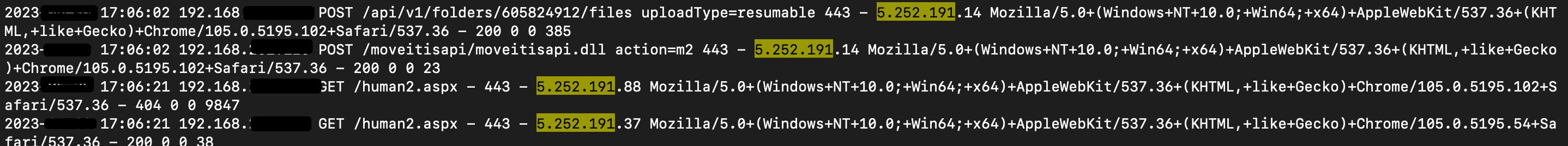
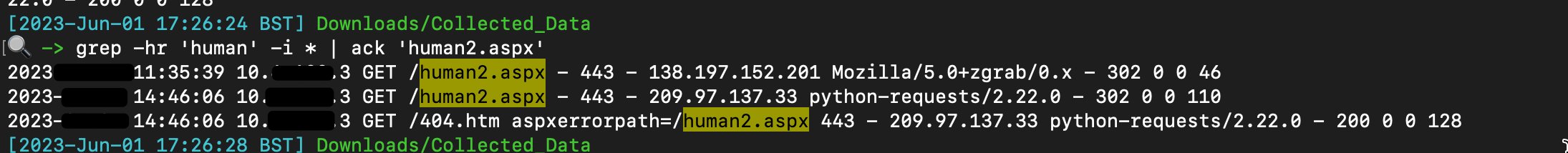
The following webshells with "human2.aspx" was found in VT
- bf7c1dd613101c0a95027249a5fcb759
- e9a5f0c7656329ced63d4c8742da51b4
- af136505d384c9a89635b365e55b7fa3
Reference
[1] Abrams, L. (2023). New MOVEit Transfer zero-day mass-exploited in data theft attacks. Retrieved 3 June 2023, from https://www.bleepingcomputer.com/news/security/new-moveit-transfer-zero-day-mass-exploited-in-data-theft-attacks/
[2] MOVEit Transfer under active mass exploitation, patch now. (2023). Retrieved 3 June 2023, from https://www.theregister.com/2023/06/01/moveit_transfer_zero_day/
[3] Noll, N. (2023). Critical Vulnerability in Progress MOVEit Transfer: Technical Analysis and Recommendations - TrustedSec. Retrieved 3 June 2023, from https://www.trustedsec.com/blog/critical-vulnerability-in-progress-moveit-transfer-technical-analysis-and-recommendations/
[4] Zero-Day Vulnerability in MOVEit Transfer Exploited for Data Theft | Mandiant. (2023). Retrieved 3 June 2023, from https://www.mandiant.com/resources/blog/zero-day-moveit-data-theft
[5] https://www.rapid7.com/blog/post/2023/06/01/rapid7-observed-exploitation-of-critical-moveit-transfer-vulnerability/