Spectrum of Breach
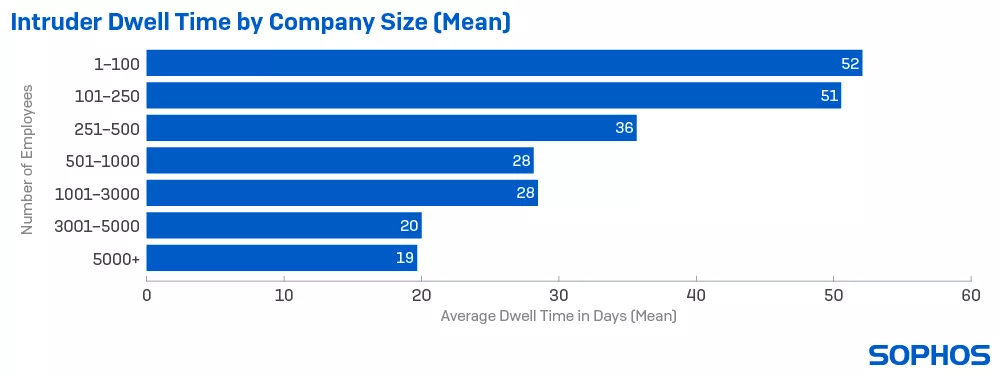
It's not whether you'd be breached, but a matter of when. Famous saying echoing through the chambers of corporate world with cyber security taking center stage. Today's reality is about knowing the state of your network. based on research by Sophos[1], average attacker dwell time in a compromised network is around 19 - 51 days. It is not uncommon for attackers to dwell longer than the reported time, perhaps due to amount of data to be exfiltrated or the attackers merely looking for more juicy target within the organization.
Introducing Spectrum of Breach
I came up with the spectrum of breach to illustrate the idea that breach isn't just a point of event, but a series of events that may lead to a breach, and the subsequent activities of post breach. In the Spectrum of Breach, I divide the timeline into 3 parts. First, being the time before a breach occurs, the exact time when the breach actually happens, and the time after the breach takes place, where the attackers linger and wander around the network.

Lockheed Martin Cyber Kill Chain
A famous framework that tends to be used extensively in the threat landscape is the Lockheed Martin Cyber Kill Chain[4] framework. This framework espouses the breach process into more granular stages within the breach process. Let's look at each phase of the cyber kill chain.
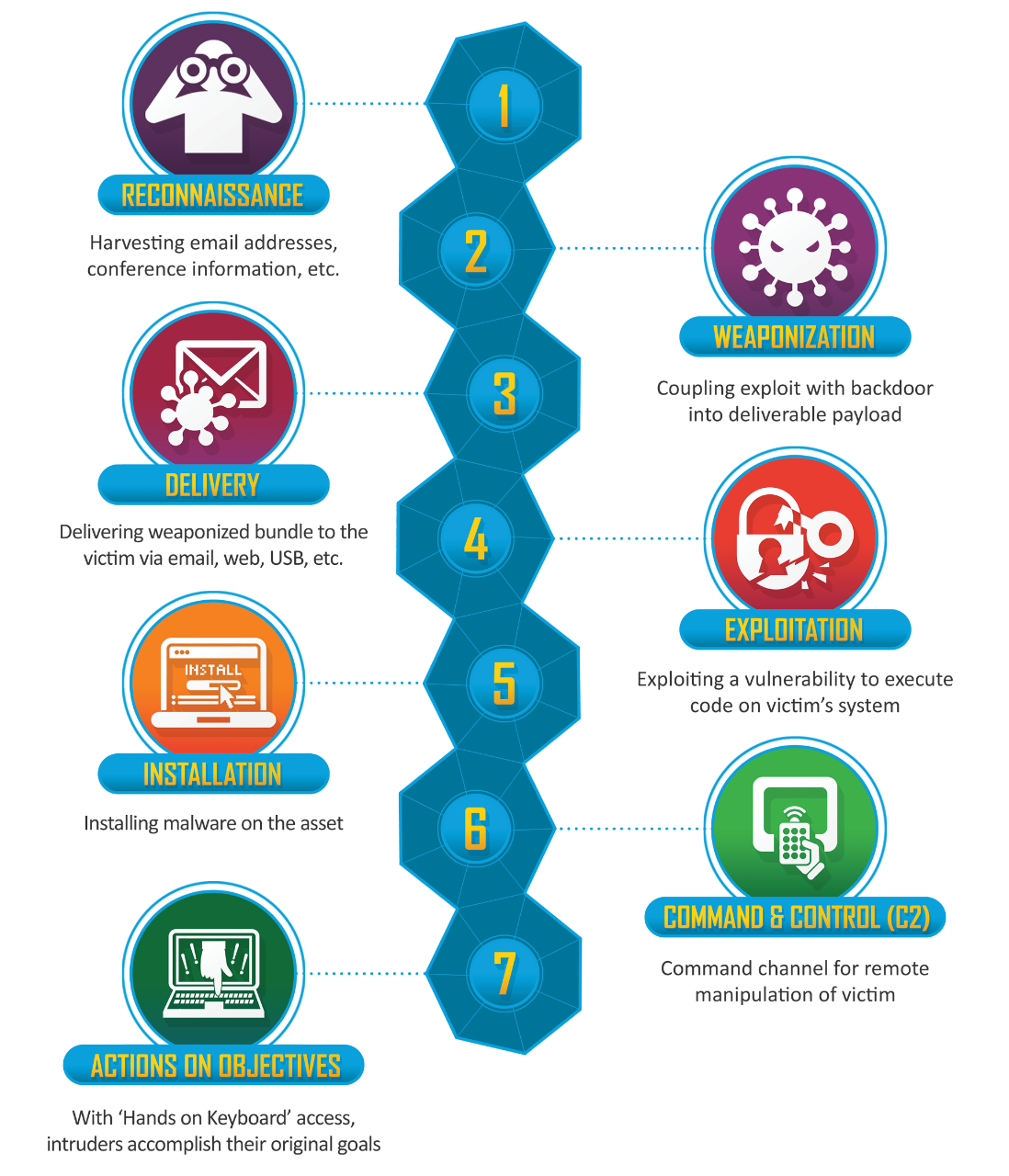
Phase 1: Reconnaissance
The first phase in the cyber kill chain is reconnaissance, where attackers gather information about their target organization. This can include researching public-facing websites, social media accounts, and online databases to identify potential vulnerabilities and targets[4]. During this phase, attackers may also use scanning tools to discover network resources and open ports. Organizations can protect themselves by limiting public access to sensitive information, regularly updating their software, and monitoring their networks for unusual activity.
Phase 2: Weaponization
After gathering intelligence about their target, attackers move to the weaponization phase, where they create a malicious payload or exploit[5]. This can take the form of a malware-infected email attachment, a compromised website, or a specially crafted document designed to exploit a vulnerability in a target's software. To counter this phase, organizations can implement strong email filtering and content scanning solutions to block malicious payloads from entering their networks.
Phase 3: Delivery
In the delivery phase, attackers attempt to deliver their weaponized payload to the target's network[6]. This can be achieved through various methods, such as spear-phishing emails, drive-by downloads, or social engineering. Organizations can strengthen their defenses by providing regular security training to employees, raising awareness about common attack vectors, and implementing robust email and web filtering solutions.
Phase 4: Exploitation
Once the malicious payload has been delivered, attackers exploit vulnerabilities in the target's systems to gain unauthorized access[7]. This can involve exploiting software vulnerabilities, misconfigurations, or weak passwords. Organizations can mitigate the risk of exploitation by keeping their software up to date, implementing strong password policies, and continuously monitoring their networks for signs of intrusion.
Phase 5: Installation
After gaining access to the target's network, attackers install their malware or tools to maintain persistence and control[8]. This can include installing backdoors, keyloggers, or other malicious software. To counter this phase, organizations should implement strong endpoint protection solutions, including antivirus and anti-malware software, to detect and remove malicious software.
Phase 6: Command and Control (C2)
Once their malware is installed, attackers establish a command and control (C2) channel to remotely manage their compromised systems[9]. This allows them to issue commands, exfiltrate data, and maintain control over the target's network. Organizations can disrupt C2 channels by monitoring their network traffic for unusual patterns, implementing network segmentation, and blocking known malicious IP addresses and domains.
Phase 7: Actions on Objectives
In the final phase of the cyber kill chain, attackers take action to achieve their objectives, which can range from stealing sensitive data to disrupting critical services[10]. Organizations can detect and respond to these activities by implementing robust monitoring and incident response capabilities, ensuring they can quickly identify and remediate any security breaches.
Spectrum of Breach and Cyber Kill Chain
In the next diagram, you will see how the Cyber Kill Chain lines up to the Spectrum of Breach.
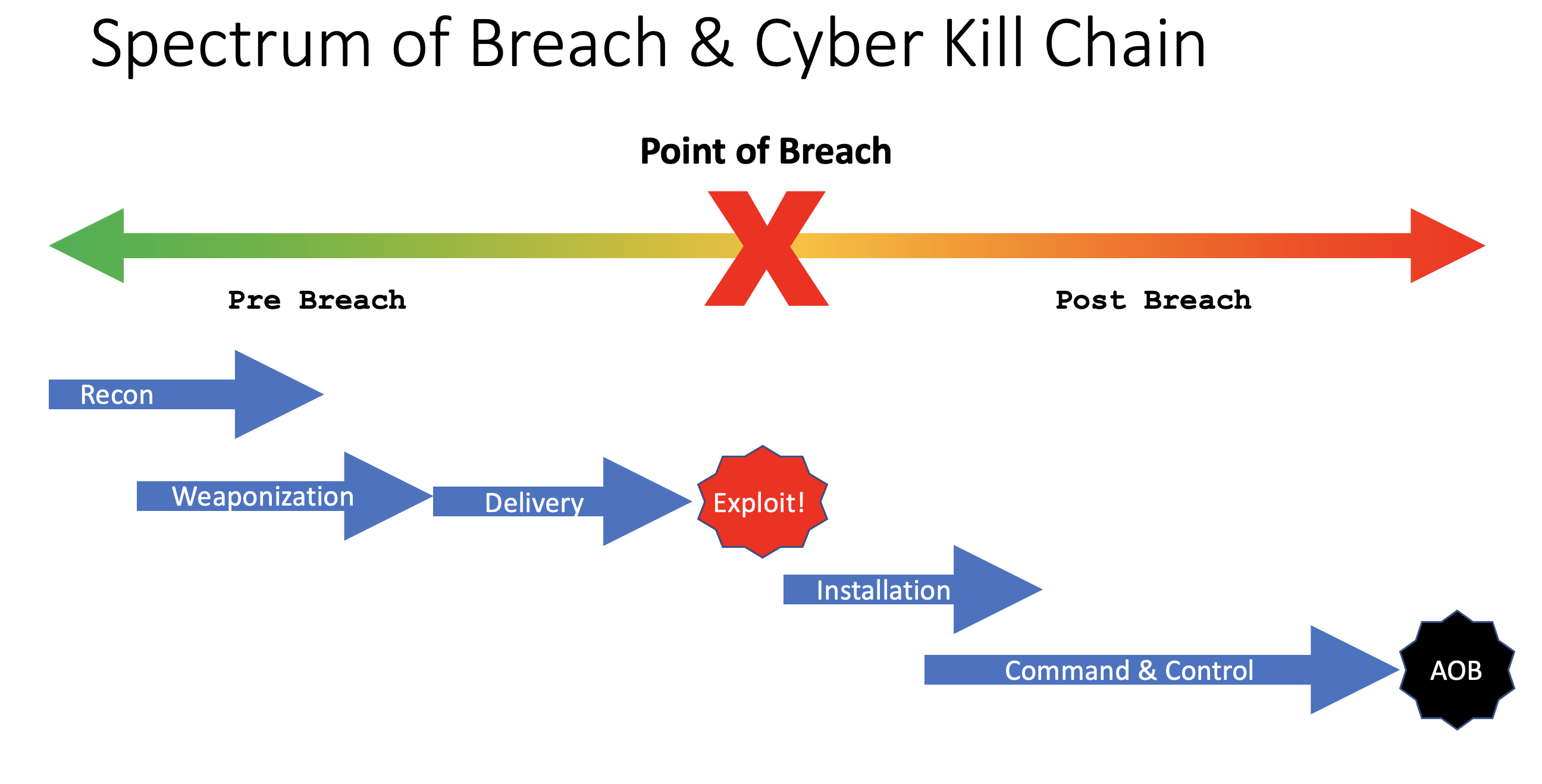
Phase 1 to Phase 3 is defined as pre-breach stage. Stage 4 is the actual breach and the subsequent stages are post breach.
Conclusion
At this point, this article aims to introduce the concept Spectrum of Breach. The article also highlights the synergy between Spectrum of Breach and other frameworks, namely Cyber Kill Chain. In the subsequent articles we will exploure why this concept is important and how it plays out in cyber defense.
References
[1] https://www.sophos.com/en-us/press/press-releases/2022/06/attacker-dwell-time-increased-by-36-percent-sophos-active-adversary-playbook-2022-reveals
[2] https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
[3] Hutchins, E., Cloppert, M., & Amin, R. (2011). Intelligence-driven computer network defense informed by analysis of adversary campaigns and intrusion kill chains. Lockheed Martin Corporation. Retrieved from https://www.lockheedmartin.com/content/dam/lockheed-martin/rms/documents/cyber/Gaining_the_Advantage_Cyber_Kill_Chain.pdf
[4] Pierluigi, P. (2016). A deep dive into the cyber kill chain: Reconnaissance. Security Affairs. Retrieved from https://securityaffairs.co/wordpress/51652/cyber-crime/cyber-kill-chain-reconnaissance.html
[5] Hulme, D. (2015). The cyber kill chain: Understand the steps of a cyber attack. IT Governance Blog. Retrieved from https://www.itgovernance.co.uk/blog/the-cyber-kill-chain-understand-the-steps-of-a-cyber-attack
[6] Gordon, S., & Ford, R. (2015). Cybersecurity's next phase: Cyber-deterrence. Computer, 48(12), 58-61. DOI: 10.1109/MC.2015.374
[7] Cisco. (2020). The Cyber Kill Chain: A Foundation for your Cybersecurity Strategy. Retrieved from https://www.cisco.com/c/en/us/products/security/cyber-kill-chain-infographic.html
[8] Sanders, J. (2019). Exploitation and installation: A breakdown of the cyber kill chain. Hashed Out. Retrieved from https://www.thesslstore.com/blog/exploitation-and-installation-a-breakdown-of-the-cyber-kill-chain/
[9] Carbon Black. (2019). Understanding the Cyber Kill Chain. Retrieved from https://www.carbonblack.com/2019/02/05/understanding-the-cyber-kill-chain/
[10] CSO. (2021). Cyber Kill Chain: What it is and how to use it. CSO Online. Retrieved from https://www.csoonline.com/article/2134037/cyber-kill-chain-what-it-is-and-how-to-use-it.html