Google introduced Passkey as means of ending the reliance of passwords today. One year[1] in the making, Google, together with giants like Apple, Microsoft and FIDO Alliance announced that they will support passkeys on their respective platforms in order to provide an easier and more secure alternative to password, seemingly ahead of the World Password Day.
This new authentication scheme provides support for Android & Chrome. Apple and Microsoft will respective announce it for their platforms.
The key idea is to simplify sign-in's across devices, websites and applications irrespective of the platform; without the need for a single password. It starts will Google today and will be available across within this coming year.
What are Passkeys
This is the TL;DR version.
Usually when you sign-in to a website, you use your username/password. If it is correct, the site gives you access. That's legacy.
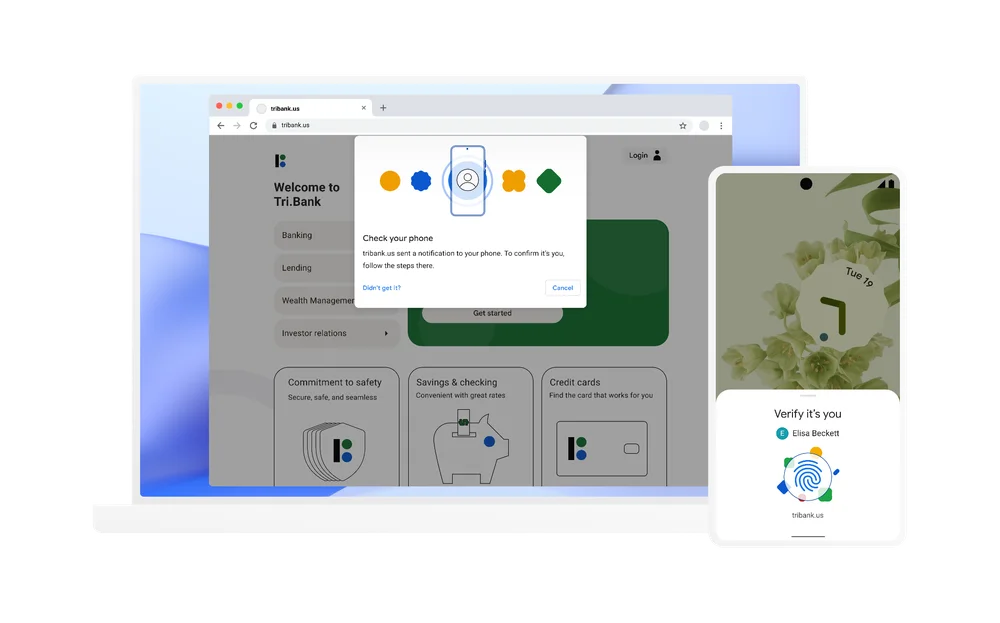
With passkey, signing in to the website or service will just be as simple as unlocking your phone. No passwords required. The phone will give you a prompt to confirm if you want to login to the service. Select YES and you are good to go. We've seen this with Google before, when you try to sign in with a new device for your Google accounts.
The actual implementation
The underlying technology to enable this is public key cryptography. A key pair is generated on the device, a private and a public keypair. The public keypair is sent to Google.
When sign-in is initiated, Google sends a unique challenge to your device. Your device signs it with the stored private key (upon your approval by unlocking the device). This signature is then verified by Google using the public key that you had previously provided to Google.
Your device ensures that the signature can only be shared with Google, preventing spillover to any phishing sites. Signature confirms that the device is yours and it contains the private key. It does not your any of your biometric information.
Each keypair generated can only be used for one single service. This means that if you have Google account and an Apple account, using passkeys means that you will have separate passkeys for each account.
WHat about using passkey to sign in on another device? Firstly, you need to scan the QR code displayed on that device. The device then verifies your phone is in close proximity through a small anonymous Bluetooth message which sets up an end-to-end encryption channel to the phone through the internet. The phone uses this connection to deliver the one-time passkey signature which requires your approval and biometric/screen-lock authentication on your phone. The biometric/screen-lock is only meant to authorise, and that sensitive information is never transmitted. The bluetooth proximity check ensures that remote attackers cannot pull off such an attack.
What if I lose my device?
There are 2 methods in handling this. First, your devices are synched to the cloud which is protected by your device level authentication. Second, you simply create a new passkey and provision it to your Google account. You always have the option to remove old passkeys for unused devices.
I recommend to use unique passkeys tied to each device, rather then using a common one. That way, revoking a passkey still allows other device to access the account.
Is this the most secure way?
Google maintains that having a physical key, such as FIDO U2F such as Yubikey is still the most secure method. Passkeys are second best for now.
Does this mean that I can't use my passwords?
Passwords will still be available as a means of authentication. So will U2F keys and other means currently supported.
Does my password manager support passkey?
You'd have to check with them Right now, Google confirms that their password manager supports passkeys.
Reference
[1] One step closer to a passwordless future
One step closer to a passwordless future. (2022). Retrieved 4 May 2023, from https://blog.google/technology/safety-security/one-step-closer-to-a-passwordless-future/
[2] So long passwords, thanks for all the phish
So long passwords, thanks for all the phish. (2023). Retrieved 4 May 2023, from https://security.googleblog.com/2023/05/so-long-passwords-thanks-for-all-phish.html