There were much news about data leakage/breach affecting the Malaysian contact tracing and vaccination app, MySejahtera. However, actual data was not available. The recent AG's audit report has highlighted details about this data breach. Let's dive in.
The Application
The application has a tiered approach for it's implementation. The report gives us an idea as to how the application is architected.
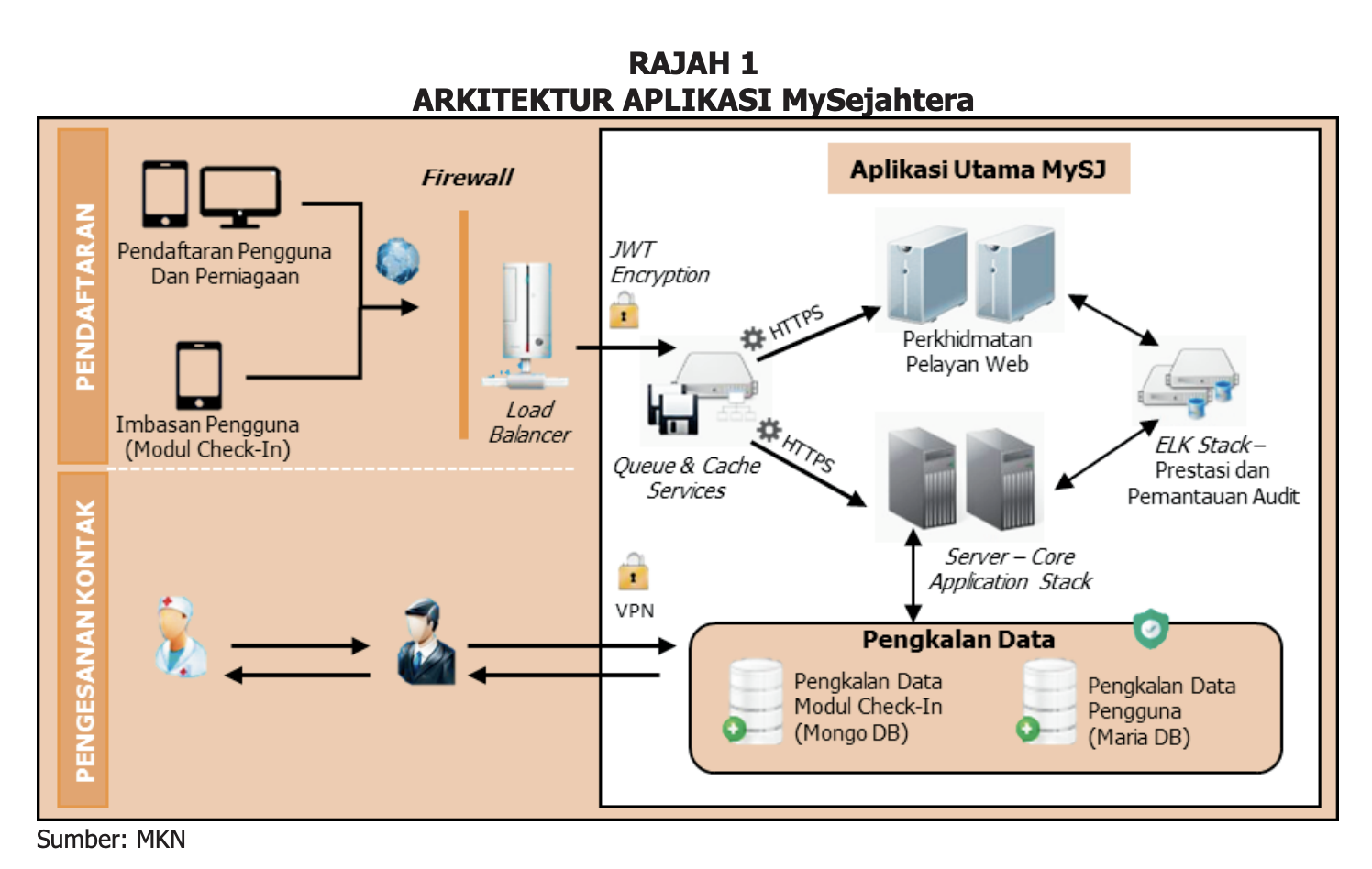
It is important to keep in mind that MySejahtera was never a complete solution. It was noted that the application was built as and during the pandemic. Meaning, Malaysia took a beta version of app under the guise of CSR and extended the use after this. The procurement issue of this app was discussed in the Malaysian Parliament.
Data Accuracy
I note an interesting finding by the auditors. Account that has yet to be verified and not deleted because no application from the user remains permanently in the system and counted as active (???).
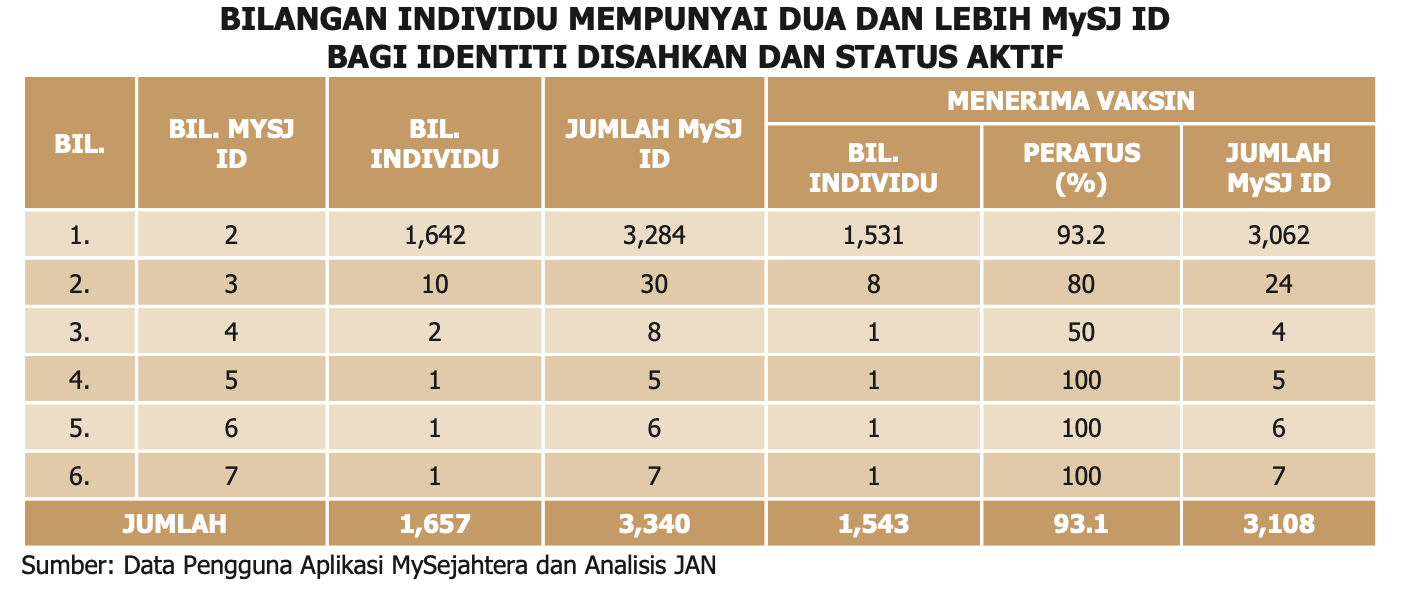
Verification is done by the user pressing the verify button, visually confirming name and NRIC/Passport. Second would be through the vaccination program. If both methods do not work, the the users remain in the system as "TIDAK DISAHKAN".
Administrative management
As per KKM's procedures, Privilege Access right must be controlled and limited. Am access matrix was created to ensure that the app and the capabilites are rightfully managed.
The audit shows that all application for the IDs are managed and done via email. 826 user access and 56 MyVAS account was registered. 364 unique user account was created without using govt official email. The following table explains.
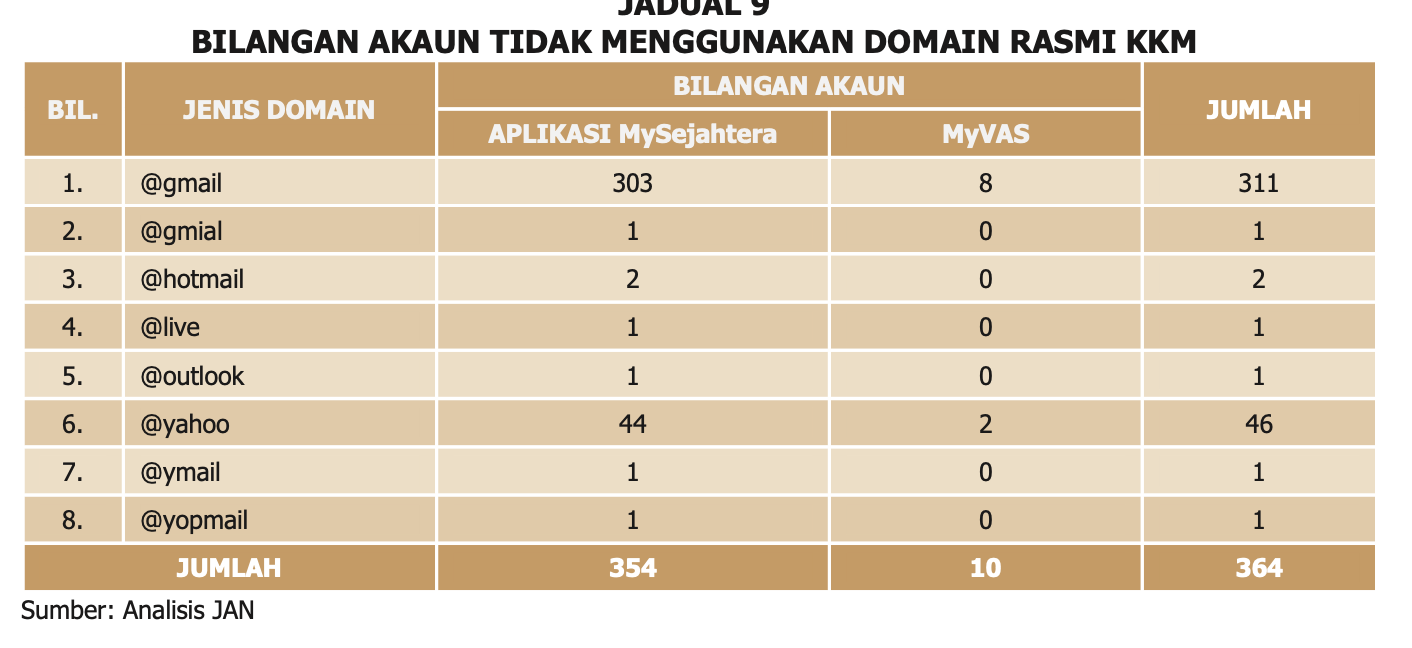
This should be the first red flag, and while yes, pandemic is going on, I see no reason why the govt email was used to create IDs.
The reason given is that the issues related to official govt email - MyGOVUC is often down. The domain "@yopmail" was a test account used by service provider"
Am I the only one doing head palm at this point?
I found another interesting data point.
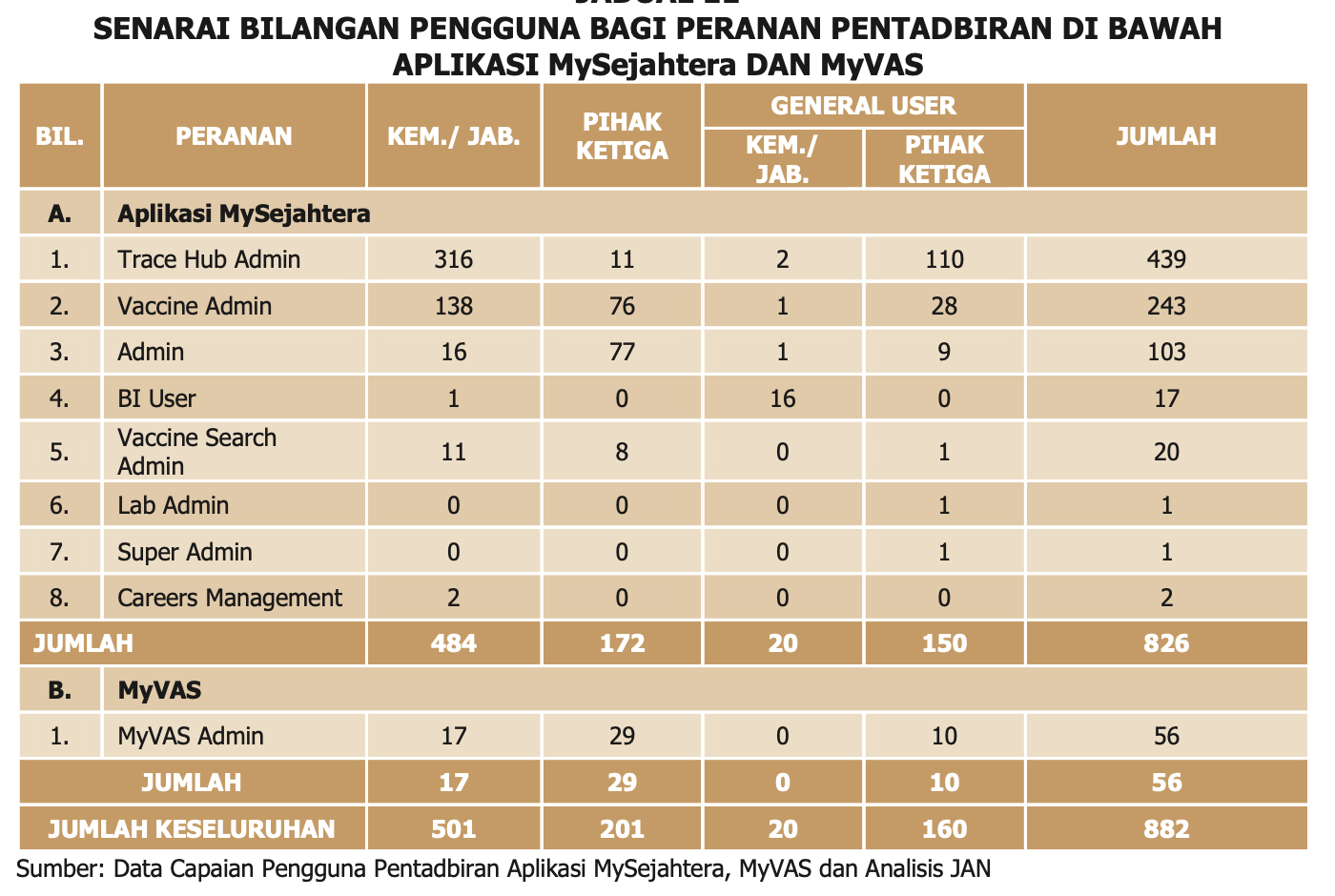
For MySejahtera, there is only one Super Admin access, which is held by third party. We're talking about production app, and its a industry practice that third party only gets account provisioned if and when required, and not holding a permanent production access.
Who has Admin access? It was discovered that 103 users where given Admin access, out of which only 17 were from Ministry. 77 third party admin. Another red flag.
Is it secured?
The were attempts to break into the app, by the IP 167.X.X.122 since 27 October 2021. As a result, a web application firewall was deployed in cloud on 1 November 2021.

Interesting to note that these seems like fixed IP and I wonder why AG report masked the IP. If you know, you know. And if the IPs were made available, there can be some triage done and identify the attackers.
These activities occured between 28 October 2021 to 31 October 2021. Activities observed include bulk upload using Excel for vaccination appointments and vaccination records check.
Remediation action taken by KKM are
- Cancelling the affected accounts
- adding anomaly detection with blocking for repeated high occurance from the same source IP
- Inform NACSA on the blocking
- Installing and commissioning WAF
- Police report made
Throughout the report the Ministry emphasizes that there is a formal process and approval for user ID and accounts.
My assessment
I started this article by highlighting the procurement process of the app. It seems that the irregular nature of the application procurement that had involved accepting the user because it was done out of CSR limits the ability of the app being developed in totality or having complete functionality. If the app functionality isn't complete, what more would be the situation of the security controls?
The incident involves around the user of an Admin account which was used to bulk download information from the application.
This is the part where I ask questions related to this breach
- From the report, it seems that there is no mention of 2FA or MFA. And it seems that password is the key authentication factor for such a critical application. Is that so?
- Users not having gov.my email address is a huge problem. Why wasn't this addresed? and why was MyGOVUC allowed to operate with so much issues? (I believe MAMPU should be the party managing this). Or was this the case of increased number of request due to pandemic, which then lead to govt system not being sized for growth and often goes down when there are additional load. Is that so?
- Why are the IP's hidden? Visibily the first octet seems to indicate possible Malaysian IP but one cannot confirm unless having the IP fully available.
- Why was the incident kept hush? Why didn't the Minister (then) come clean? There were some blurts but no actual information.
- Installation of WAF seems to be hindsight rather than proactive security measure. Was security ever prioritised?
- Multiple IPs were used to download the data. Okay. Was the password compromised? How was the password compromised? Is there 2FA/MFA and was that compromised too? Was there an assessment done on other accounts? Was there a phishing incident that lead to the account compromise? Was one of the non gov.my account the cause?
- The depth of the report (to me) is still surface. Understood that this is the annual audit on the operations, but a more technical deep dive on the matter should be done. When will that happen?
Recommendation to this predicament
- Lack of sharing on the incident is evident. It is pointless for Minister to speak about Cyber Threat Intelligence and information sharing when such incidents affecting government agencies are kept hush. If govt is serious about cyber, walk the talk. Govt should start sharing threat intelligence on what it sees, rather than preaching for industry to spearhead.
- Security in this case is a clear after thought. Lack of proper procurement without having security as a primary consideration is a key issue, which needs to be tackled. The incident happened in 2021 and it's 2 years after is when we know about it.
- Critical applications must at minimum have multi factor authentication. This prevents further compromise of the account.
- Account monitoring only came into the picture with anomaly detection after the incident. This is critical and should have been made default, goes back to my argument on point 2.
- In some sectors, a signoff is required to ensure that some activities are checked before its allowed. The 4 eyes principle or maker/checker. Its evident this system is missing those validation points.
Honestly I find it highly unusual that there were no reports of attacks before 27 October 2021. Remember that MySejahtera was launched on 16 April 2020. So, you're saying that there is no report of potential attack, at all?
Please wait while I watch flying cows pass by.

Any device out on the public domain gets scanned every second, and to say there is only one set of IP is rather misleading. I'm not sure that the attack stopped here, I am sure there were attacks before which was not discussed on this audit report. Using Google or any third party systems like Censys would give the information about KKM's server that was used which was publicly available.
While the 1.12 million attempts were logged in the report and highlighted in the news, honestly running a few scripts would rake that number. My home router gets more than that on average depending on time of the year. My VPS gets more that on a week!
Reference
[1] https://www.mampu.gov.my/wp-content/uploads/2022/10/4-Oct-Malaysia-Gazette-Pelantikan-pembangun-aplikasi-MySejahtera-tak-ikut-prosedur-%E2%80%93-PAC.pdf
[2]https://lkan.audit.gov.my/laporan/manage/1474