Background
Ahmed Eltantawy is a former Egyptian Member of Parliament who previously served as the chairman of Egypt’s al-Karama political party. He announced his intention to run in the upcoming Egyptian presidential election, stating that he planned to offer a “democratic” alternative to the current president in March 2023. Following this announcement Eltantawy, his family members, and supporters have been subjected to harassment, including reported arrests of 12 family members.
Egypt’s current president Abdel Fattah el-Sisi has been in power since 2014, when he led the military overthrow of President Mohammed Morsi. Sisi has been widely described as an autocrat. Human rights groups, including Amnesty International and Human Rights Watch, have documented widespread human rights abuses under el-Sisi’s regime, including repression against civil society groups, activists, and political opposition.
Eltantawy became suspicious about the safety of his phone and reached out to the Citizen Lab. Citizen Labs performed a forensic analysis on his device. The arising forensic analysis showed numerous attempts to target Eltantawy with Cytrox’s Predator spyware.
Zero-Day iOS Exploit Chain
An exploit chain is where multiple exploits are "chained" together to create a devastating exploit.
While working with Eltantawy, the Citizen Lab and Google’s Threats Analysis Group (TAG) obtained an iOS exploit chain that had been targeted at him. Citizen Labs initiated a responsible disclosure process with Apple, which assigned the following CVEs to vulnerabilities associated with the chain:
CVE-2023-41991 (Security): A malicious app may be able to bypass signature validation.
CVE-2023-41992 (Kernel): A local attacker may be able to elevate their privileges.
CVE-2023-41993 (WebKit): Processing web content may lead to arbitrary code execution.
On September 21, 2023, Apple released updates to multiple Apple products, which patches the vulnerabilities used by the exploit chain.
Exploit explained
Exploit delivery via man-in-the-middle (MITM)
The Intellexa exploit chain was delivered via a “man-in-the-middle” (MITM) attack, where an attacker is in between the target and the website they’re trying to reach. If the target is going to a website using ‘http’, then the attacker can intercept the traffic and send fake data back to the target to force them to a different website. Visiting a website using ‘https’ means that the traffic is encrypted, and it is easily verifiable that the received data came from the intended website using their certificate.
Some sites deploy HSTS, makes it even more difficult to spoof. That is not the case when using ‘http’.
In the case of this campaign, if the target went to any ‘http’ site, the attackers injected traffic to silently redirect them to an Intellexa site, c.betly[.]me. If the user was the expected targeted user, the site would then redirect the target to the exploit server, sec-flare[.]com. While there’s a spotlight on “0-click” vulnerabilities (bugs that don’t require user interaction) this MITM delivery also didn’t require the user to open any documents, click a specific link, or answer any phone calls.
iOS Exploit Chain
As soon as the attacker redirected the target to their exploit server, the exploit chain began to execute. For iOS, this chain included three vulnerabilities as mentioned above.
The chain then ran a small binary to decide whether or not to install the full Predator implant. However, Google TAG was unable to capture the full Predator implant.
Android Exploit Chain
The attacker also had an exploit chain to install Predator on Android devices in Egypt. Google TAG observed these exploits delivered in two different ways: the MITM injection and via one-time links sent directly to the target. We were only able to obtain the initial renderer remote code execution vulnerability for Chrome, which was exploiting CVE-2023-4762.
This bug had already been separately reported to the Chrome Vulnerability Rewards Program by a security researcher and was patched on September 5th.
Fingerprinting and Scanning
The zero-day chain was hosted on sec-flare[.]com, and also contacted verifyurl[.]me. We fingerprinted these two websites (fingerprint F1 for sec-flare[.]com and F2 for verifyurl[.]me). We have identified a large number of IPs that matched Citizen Lab's fingerprints, using Internet scanning. Citizen Labs consider all of these IPs (and the domain names returned in TLS certificates when they matched fingerprints) to be linked to Cytrox’s Predator spyware. While Citizen Labs investigate further, they are not releasing the domain names or IP addresses at this time.
Some of the domains that was identified had names suggestive of tailoring towards specific countries or regions of focus include the Arabian Gulf, Southeast Asia, Angola, the Democratic Republic of the Congo, Egypt, Greece, Indonesia, Kazakhstan, Madagascar, Mongolia, the United Arab Emirates, and Sudan, which is a reported Cytrox customer. Citizen Labs cannot necessarily conclude that all of these governments are customers.
Network Injection
In August and September 2023, when Eltantawy visited certain websites without HTTPS from his phone, using his Vodafone Egypt mobile data connection, he was silently redirected to a website (c.betly[.]me) via network injection. The domain betly[.]me matches Citizen Lab's fingerprint F1 for Cytrox’s Predator spyware.
The injection was triggered based on the website specified in the HTTP Host header, as well as the value of the User-Agent header. The following reply was injected by an on-path middlebox, and the legitimate reply from the server was suppressed:
HTTP/1.1 307 Temporary Redirect
Via: 1.0 middlebox
Location: https://c.betly[.]me/[REDACTED]
Connection: close
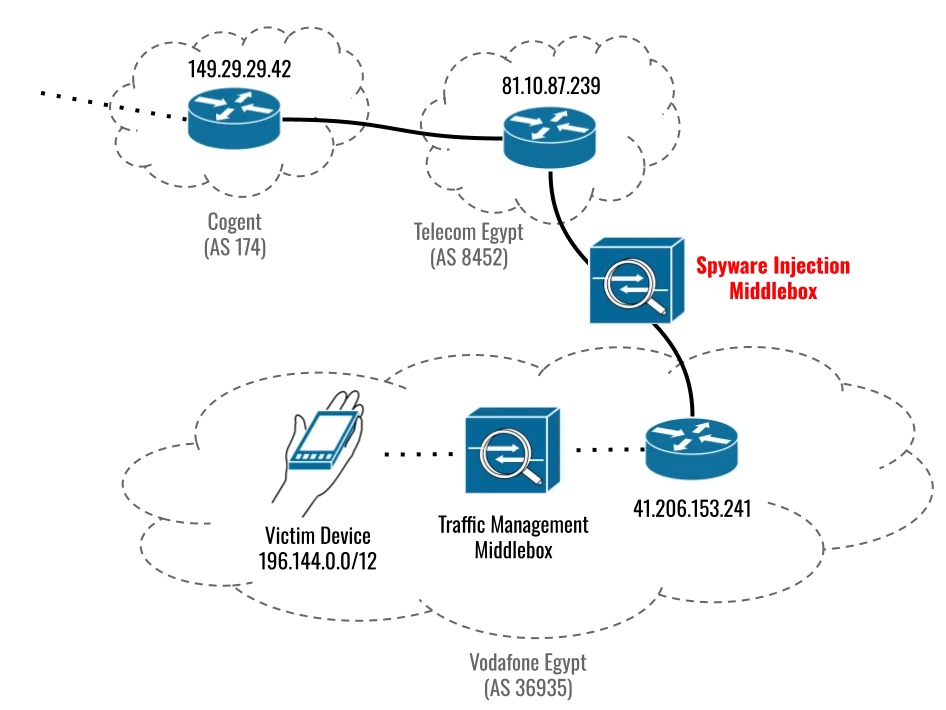
Spyware Injection Localized to Egypt
We conducted a test to understand where in the network the injection happened. Ultimately, Citizen Labs were able to localize the injection to a link between Telecom Egypt and Vodafone Egypt. Citizen Labs cannot conclude from technical data alone whether the middlebox sits on the Telecom Egypt side or the Vodafone Egypt side of the link. Citizen Labs suspect that it is within Vodafone Egypt’s network, because precisely targeting injection at an individual Vodafone subscriber would require integration with Vodafone’s subscriber database.
Also, given that the injection is operating inside Egypt, the spyware is sold to government agencies, and Egypt is a known Predator customer, it is highly unlikely that this targeting occurred and that this setup was established outside of the purview of Egyptian authorities.
Traditional Localization Technique Not Applicable
This technique was not applicable to Eltantawy’s case because Vodafone Egypt’s network appears to have a separate middlebox close to subscribers that manages all TCP connections. This middlebox, which we suspect is used for benign traffic management, is located at approximately IP TTL = 4 from Eltantawy. Since the traffic management middlebox rewrites packets with fixed TTL values, we cannot control the TTL value beyond the traffic management middlebox. We were however able to determine that the spyware injection was not located anywhere up to TTL = 4 from Eltantawy.
Injector Design Choices Enable Alternate Localization Technique
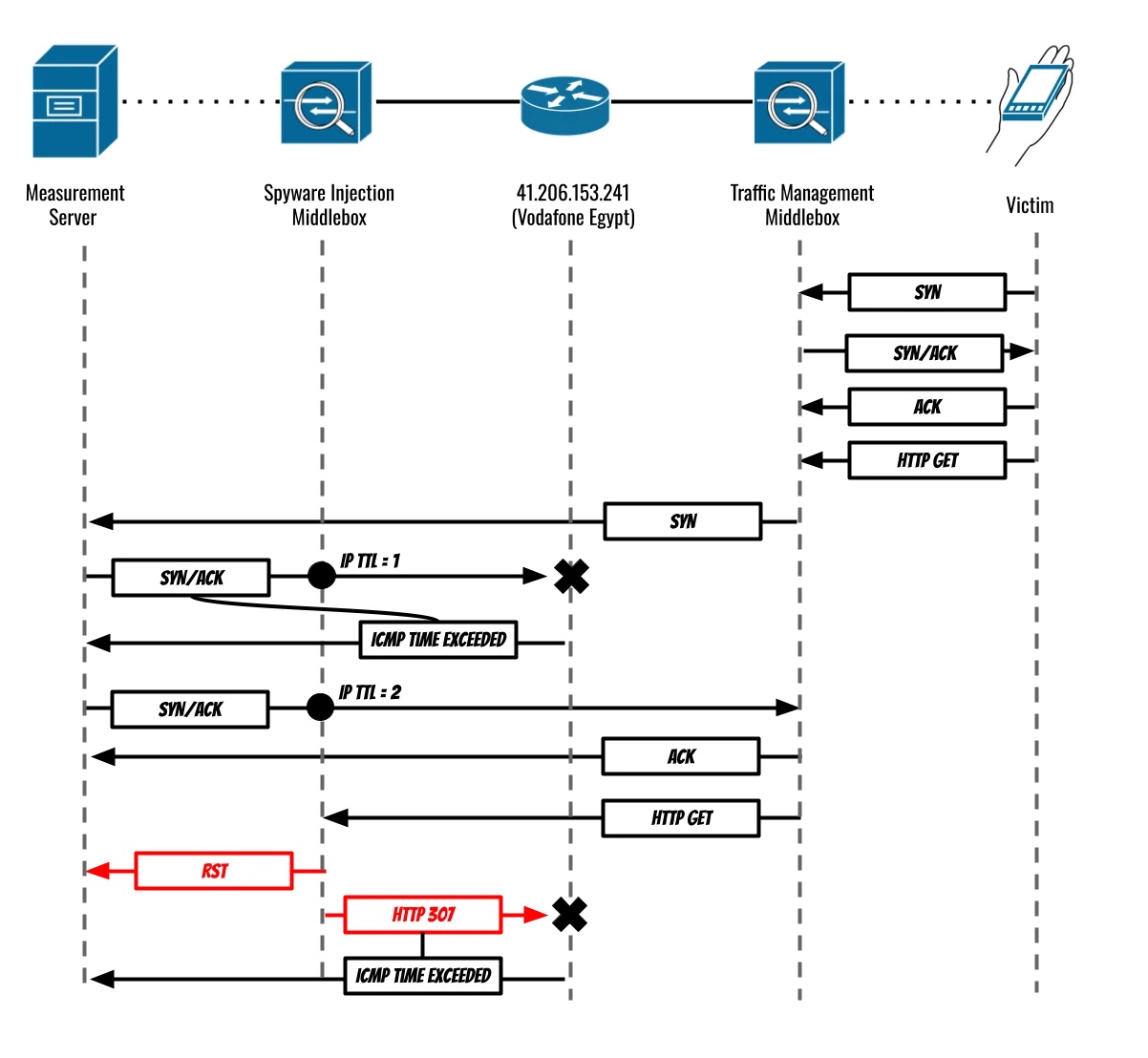
Citizen Labs identified two design choices in the injector, which, together, enabled us to localize the injection “in reverse”, from a measurement server we controlled. First, the injector attempts to mask its presence by copying IP TTL values it receives into packets it injects. Second, when injecting a response to a client “from” a server, the injector takes the server’s TTL to be the TTL from the first SYN/ACK it sees for a TCP connection, while ignoring TTL values in subsequent SYN/ACKs.
Together, these two design choices allow us to use our measurement server to “prime” the injector to inject a TTL = 1 packet to the client. To do this, our measurement server responds to a SYN by sending a SYN/ACK that reaches the injector with TTL = 1, and then sending a follow-up SYN/ACK with somewhat higher TTL such that it reaches the traffic management middlebox, completes the connection, and causes the traffic management middlebox to send the HTTP GET request that triggers the injection.
When the HTTP GET request reaches the injector, the injector sends a packet back to the client with TTL = 1. Because the injector is not directly adjacent to the client, the router immediately downstream from the injector will determine the packet is expired, and notify the sender of the injected packet. Because the injector spoofs the packet to come from our measurement server, the router identifies itself to us, notifying our measurement server of the packet’s expiry.
Attributing the Injector
Citizen Labs attribute the spyware injection in Egypt to Sandvine’s PacketLogic product with high confidence. The attribution below has three parts.
First, Citizen Labs characterize the behavior of the spyware injection in Egypt. Citizen Labs notices that the spyware injector in Egypt behaves entirely consistently with an injector used by Turk Telekom to implement a national sinkhole in Turkey. In a 2020 test, Citizen Labs noticed that the Turk Telekom injector matched their 2018 fingerprint for Sandvine PacketLogic devices. Finally, Citizen Labs observe that, while the Turk Telekom injector no longer matches our 2018 Sandvine PacketLogic fingerprint as of September 2023, it still contains a distinctive bug that was previously measured when it did match 2018 Sandvine PacketLogic fingerprint.
Targeting via SMS
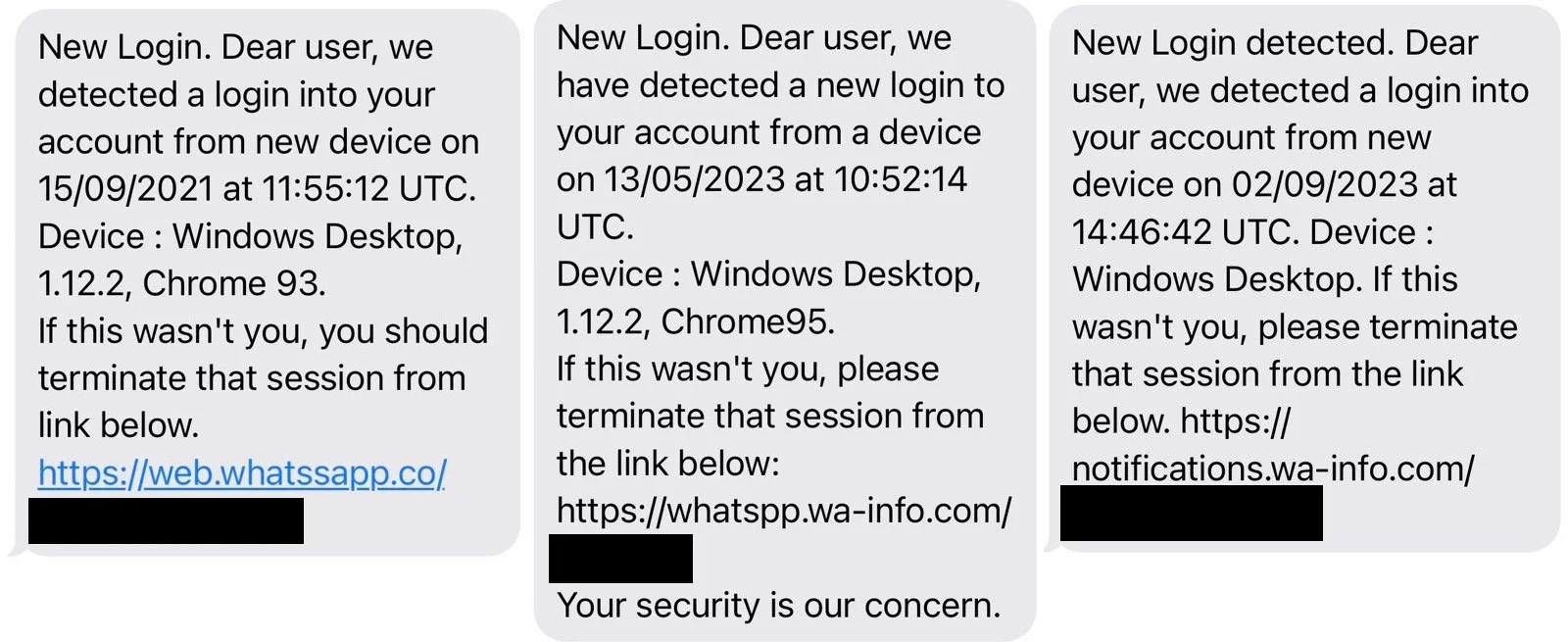
Eltantawy additionally received several SMS messages in September 2021, May 2023, and September 2023 that posed as messages originating from WhatsApp.
The fraudulent messages invited Eltantawy to visit an included link to “terminate” what the messages said was a new login to Eltantawy’s WhatsApp account. In reality, clicking the links would likely have infected Eltantawy’s phone with Cytrox’s Predator spyware.
WhatsApp Targeting
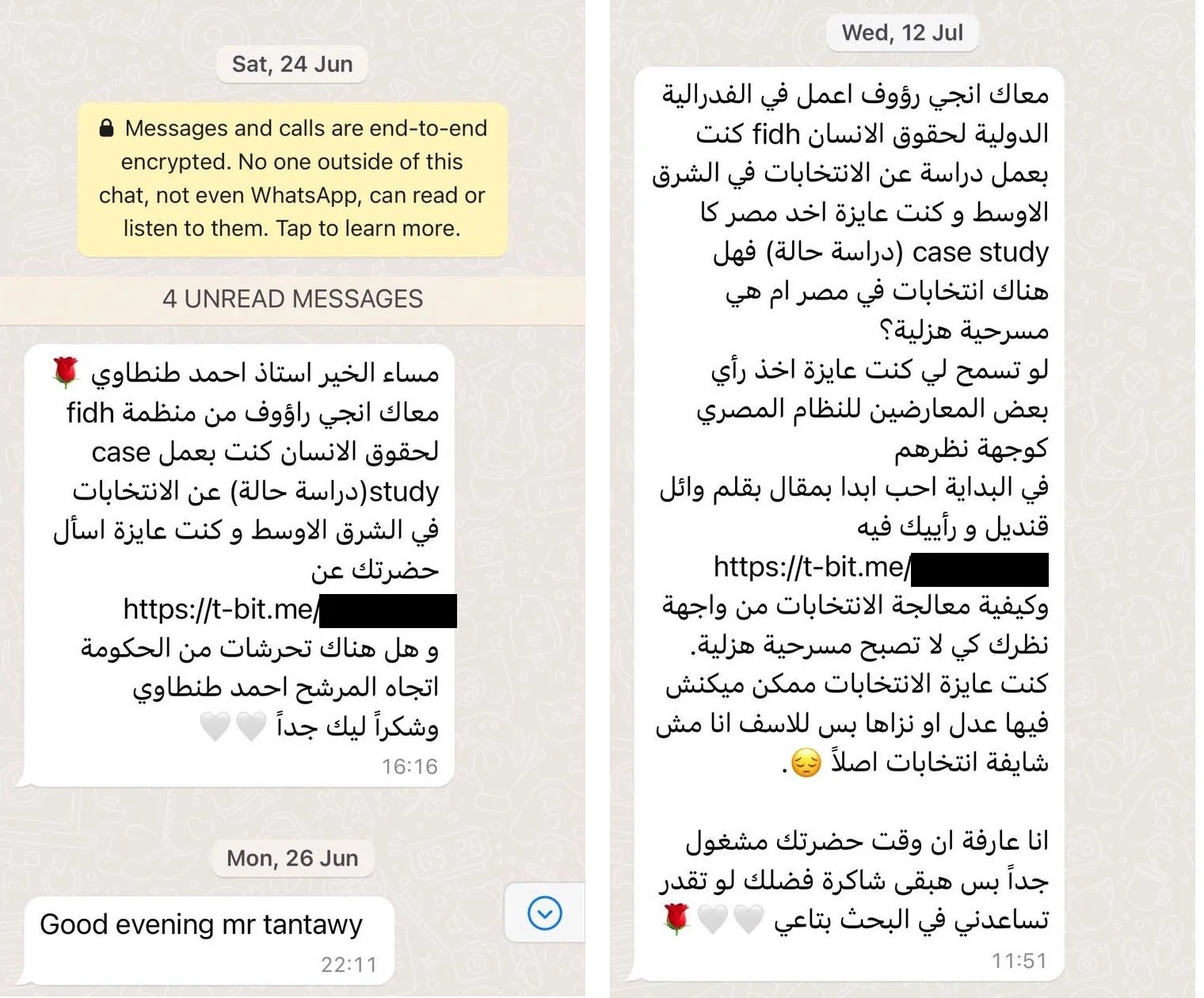
An individual purporting to be an “Angie Raouf” at the International Federation for Human Rights (FIDH) reached out to Eltantawy on WhatsApp, and sent him two Predator infection links to t-bit[.]me (matching fingerprint F1) on 24 June 2023 and 12 July 2023. The entire conversation was unread in Eltantawy’s WhatsApp, indicating that he did not engage with these links.
Conclusion
The use of mercenary spyware to target a senior member of a country’s democratic opposition after they had announced their intention to run for president is a clear interference in free and fair elections and violates the rights to freedom of expression, assembly, and privacy. It also directly contradicts how mercenary spyware firms publicly justify their sales.
President el-Sisi has been widely condemned for his autocratic rule, and Egypt’s human rights abuses have been extensively documented. For any responsible company whose technology could be abused, the warning signs are clear. Yet, as evident in Citizen Labs report, insufficient due diligence was done to prevent these types of abuses by Cytrox or the other firms we have identified whose technology was employed to target and hack the device of Eltantawy.
This latest abuse case adds to the disturbing record of abuses connected to Cytrox and its Predator spyware. In addition to the other Egyptians whose devices were hacked with Predator spyware, Citizen Labs have also documented the hacking of Greek journalist Thanasis Koukasis with Predator spyware, and former Meta employee and dual Greek-American citizen, Artemis Seaford. Other investigations showed Predator spyware was used to hack the devices of a sitting member of the European Parliament, Nikos Androulakis, and was sold to notorious human rights abusers worldwide, including the genocidal militia in Sudan. For good reason, therefore, in July 2023 the US Commerce Department added Cytrox to the list of mercenary spyware firms on its designated entity list.
This case also raises questions regarding a lack of sufficient controls around the export of technologies that can be used to violate human rights. This is not the first time that technology companies with Canadian headquarters are implicated in the export of technologies used in violation of international human rights law. While Canada has signed a recent Statement of Principles pledging to create and uphold domestic and international controls on commercial spyware technology, the Canadian government has not taken any concrete action around human rights and export controls with respect to dual-use technology.
In particular, Citizen Labs have recommended that the Canadian government ensure through law and meaningful sanctions that Canadian companies are prevented from exporting technologies to jurisdictions where there is a likelihood of human rights abuse. Significant steps must also be taken to ensure transparency into Canadian dual-use exports: there is no opportunity for public accountability without, at minimum, regular publication of detailed information regarding the type of dual-use items being exported, the name of the exporting company, and the identity of the end-user. Further, Canadian companies should also be subject to human rights due diligence obligations that are enforced through law and appropriate penalties.
Update Apple Devices Now & Enable Lockdown Mode
Citizen Labs urge everyone to immediately update their devices.
Patched versions are: macOS Ventura 13.6, macOS Monterey 12.7, watchOS 9.6.3, watchOS 10.0.1, iOS 16.7 and iPadOS 16.7, iOS 17.0.1 and iPadOS 17.0.1.
As with the BLASTPASS zero-click exploit Citizen Labs recently disclosed, they believe, and Apple’s Security Engineering and Architecture team has confirmed to us, that Lockdown Mode blocks this particular attack.
These two recent high profile cases underline the serious value that this security mode provides.
Citizen Labs encourage all Mac, iPhone, and iPad users who may face increased risk because of who they are or what they do to enable Lockdown Mode.
Reference
[1] Marczak, B., Scott-Railton, J., Roethlisberger, D., Razzak, B. A., Anstis, S., & Deibert, R. (2023). PREDATOR IN THE WIRES: Ahmed Eltantawy Targeted with Predator Spyware After Announcing Presidential Ambitions. Retrieved from https://citizenlab.ca/2023/09/predator-in-the-wires-ahmed-eltantawy-targeted-with-predator-spyware-after-announcing-presidential-ambitions/
[2] Stone, M. (2023). 0-days exploited by commercial surveillance vendor in Egypt. Retrieved from https://blog.google/threat-analysis-group/0-days-exploited-by-commercial-surveillance-vendor-in-egypt/