A joint CyberSecurity advisory was issued against a nation-state threat actor (NSTA) called Volt Typhoon. This nation-state actor is attributed to People's Republic of China. The NSTA has been identified being actively involved in activities affecting networks across US critical infrastructure and may have also spilled over to other countries and industries.
The advisory is issued by the US, AU, NZ, CA and UK. In short, 5-eyes.
Who is Volt Typhoon?
This threat actor is rather stealth in their approach, utilising a method called LOL or Living off the land.
Simply put, LOL refers to the use of existing system tools that is already available on the computer without introducing bespoke or custom tools. The Operating Systems comes with plethoria of tools, some with very useful capabilities. A highly knowledged TA would be inclined to use LOL as it reduces ability for attribution and make it difficult for blue team as these are legitimate tools and there are many ways to hide its activities as system noise.
A list of tools used by this TA - wmic, ntdsutil, netsh and PowerShell.
Its particularly difficult to detect malicious use of LOL/LOLbins as these are legitimate system utilities. The system, in the course of it's operations will invoke these tools from time to time, making it very difficult for even modern tools such as EDR or *DR to detect such activities.
Volt Typhoon has been active since mid-2021 (around pandemic, which makes it ideal for clandestine operations with the world reeling on COVID-19).
With many other NSTA, the modus operandi seems to be to maintain long term access once compromised. Besides LOL, the NSTA also does hands-on keyboard activities.
The NSTA issues commands to 1. Collect data, credentials from local/network 2. Archive data and stage it for exfiltration 3. Use stolen credentials to maintain persistence 4. Blend into normal traffic by routing it through compromised SOHO network equipments (routers, firewalls, VPN).
The NSTA also exhibits the use of open source tools to establish C2 (Command and Control) channels over proxy to mask activity.
Initial Access
The NSTA uses vulnerabilities affecting Fortinet FortiGuard as first access. Using the Fortinet device, the NSTA extracts credentials from the Active Directory and uses these privileges to authenticate with other network devices.
Microsoft confirmed that Volt Typhoon proxies all its traffic through routers from Asus, Cisco, D-Link, Netgear and Zyxel. This happens because the routers named above (some) has their management interface exposed out to the internet. So, for SOHO users, check to make sure that your management interfaces isn't visible from the internet. Some do, for the convenience of managing their network remotely (there are more secure ways of doing this, even if your IP is dynamic).
Post Compromise
The initial compromise above seems automated, but once the NSTA gets access to the network, thats where the keyboard activities start. This is identified by the nature of the commands executed, often exploratory or experimental as the commands are executed multiple times while being tweaked.
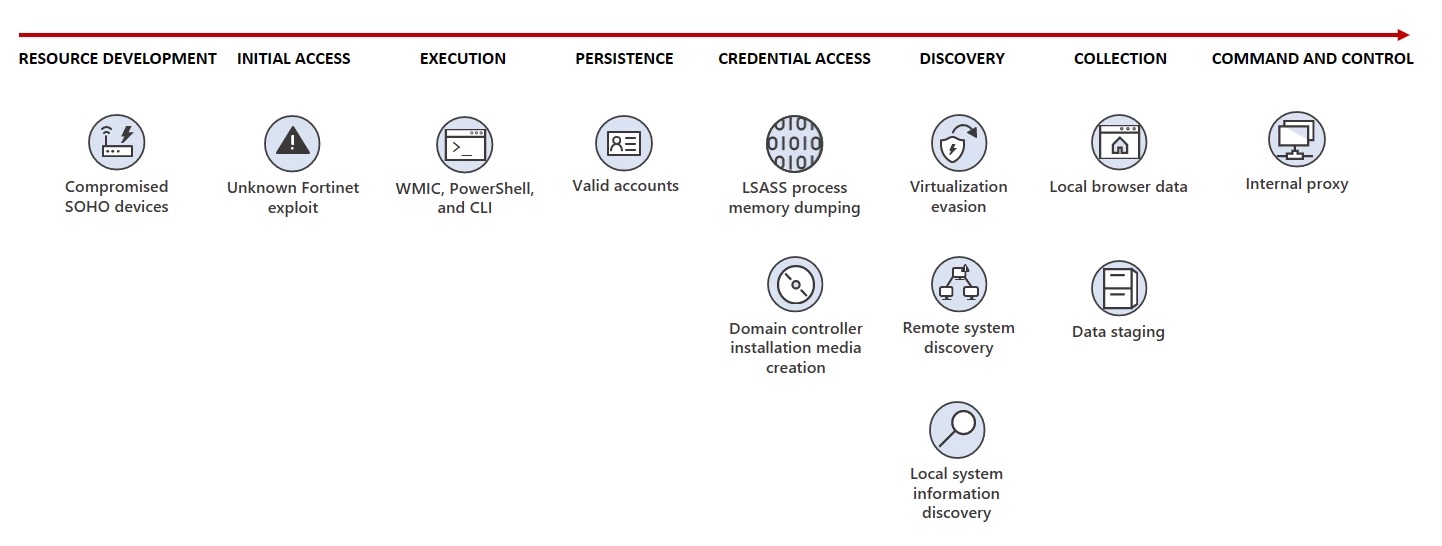
Without any custom malware, the NSTA relies on LOL commands to discover and exfil data.
Volt Typhoon attempts to dump credentials through the Local Security Authority Subsystem Service (LSASS), which contains the memory space for current user's OS credentials.
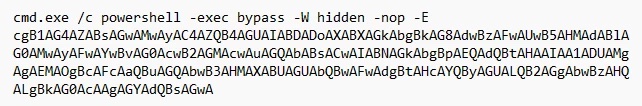 Command used to dump LSASS process memory encoded in Base64
Command used to dump LSASS process memory encoded in Base64
Volt Typhoon also frequently attempts to use ntdsutil.exe to create installation media from the domain controllers, either remote/locally. These medias contain installation files as well as username/passwords which can be used to crack offline. This gives the NSTA the credentials to elevate privilege or regain access whenever necessary.
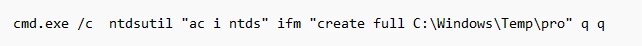 Command used to create domain controller installation media
Command used to create domain controller installation media
Command and control
Volt Typhoon accesses compromised systems by logging in with valid credentials, just like how a normal user would. In some instances, Volt Typhoon creates a local proxy for access.
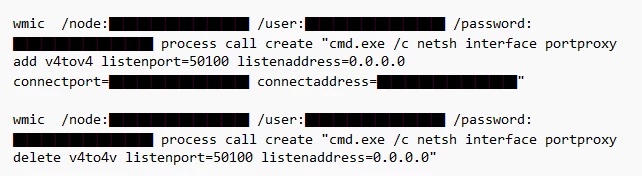 Command used to create/delete port proxy on a compromised system
Command used to create/delete port proxy on a compromised system
Compromised organizations will note that unusual IP address will be used to login into the system.
Defending against Volt Typhoon
These are the measures that can be used to mitigate against Volt Typhoon
- Enforce 2 factor authentication or multi factor authentication using hardware keys, or TOTP. Passwordless sign0-in, deactivating unused accounts also helps to reduce the risk
- Block credential stealing from LSASS by blocking process creation originating from PSExec and WMI (doing this may cause compatibility issue, so test first before deploying!)
- Block execution of potentially obfuscated scripts
- Harden the LSASS by enabling Protective Process Light for LSASS on Windows 11 (that means you need to upgrade your environment to Win11). Windows Defender Credential Guard is another option.
- Run EDR or *DR at host level.
Indicator of compromise
Volt Typhoon also uses FRP in some instances. The following is the IOC for these custom executable in SHA-256. IOC provided by Microsoft.
- baeffeb5fdef2f42a752c65c2d2a52e84fb57efc906d981f89dd518c314e231c
- b4f7c5e3f14fb57be8b5f020377b993618b6e3532a4e1eb1eae9976d4130cc74
- 4b0c4170601d6e922cf23b1caf096bba2fade3dfcf92f0ab895a5f0b9a310349
- c0fc29a52ec3202f71f6378d9f7f9a8a3a10eb19acb8765152d758aded98c76d
- d6ab36cb58c6c8c3527e788fc9239d8dcc97468b6999cf9ccd8a815c8b4a80af
- 9dd101caee49c692e5df193b236f8d52a07a2030eed9bd858ed3aaccb406401a
- 450437d49a7e5530c6fb04df2e56c3ab1553ada3712fab02bd1eeb1f1adbc267
- 93ce3b6d2a18829c0212542751b309dacbdc8c1d950611efe2319aa715f3a066
- 7939f67375e6b14dfa45ec70356e91823d12f28bbd84278992b99e0d2c12ace5
- 389a497f27e1dd7484325e8e02bbdf656d53d5cf2601514e9b8d8974befddf61
- c4b185dbca490a7f93bc96eefb9a597684fdf532d5a04aa4d9b4d4b1552c283b
- e453e6efc5a002709057d8648dbe9998a49b9a12291dee390bb61c98a58b6e95
- 6036390a2c81301a23c9452288e39cb34e577483d121711b6ba6230b29a3c9ff
- cd69e8a25a07318b153e01bba74a1ae60f8fc28eb3d56078f448461400baa984
- 17506c2246551d401c43726bdaec800f8d41595d01311cf38a19140ad32da2f4
- 8fa3e8fdbaa6ab5a9c44720de4514f19182adc0c9c6001c19cf159b79c0ae9c2
- d17317e1d5716b09cee904b8463a203dc6900d78ee2053276cc948e4f41c8295
- 472ccfb865c81704562ea95870f60c08ef00bcd2ca1d7f09352398c05be5d05d
- 3e9fc13fab3f8d8120bd01604ee50ff65a40121955a4150a6d2c007d34807642
Refererence:
[1] https://www.microsoft.com/en-us/security/blog/2023/05/24/volt-typhoon-targets-us-critical-infrastructure-with-living-off-the-land-techniques/
[2] https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-144a