Introduction
In the dynamic landscape of business operations, cybersecurity has been thrust into the limelight. As technology evolves and businesses become more digitally intertwined, cyber threats have concurrently increased, resulting in an exponential rise in cyber-attacks. In response to this growing threat, businesses have created a role dedicated to managing this risk — the Chief Information Security Officer (CISO).
The CISO’s primary responsibility is to protect an organization from cyber threats. They achieve this by developing and implementing an information security strategy, ensuring the confidentiality, integrity, and availability of data. This role necessitates a deep understanding of the technical aspects of information security, coupled with a keen ability to communicate complex concepts to non-technical stakeholders. But beyond that, a good CISO must also be a risk manager, understanding the organization's business needs, and aligning security controls accordingly.
Yet, despite the increasing importance of the role, there is ongoing debate about the exact place of a CISO in an organization's hierarchy. The question at hand is whether the CISO is a true C-level executive, holding the same authority and status as other executives like the CFO or CTO, or if the title is more cosmetic—a title-only chief role.
This article aims to delve into this debate, comparing and contrasting the role of the CISO with other C-level positions, and critically examining the arguments for and against the CISO being a true C-level executive. As we navigate through the discussion, we will take into consideration various factors including the evolution of the CISO role, its responsibilities and challenges, its impact and influence on strategic decision-making, and its future trajectory.
As we embark on this exploration, it is important to acknowledge that the debate is not merely academic; the outcome has real-world implications for how organizations manage cybersecurity risk and how they shape their strategic priorities. Whether the CISO is a true C-level role or a title-only chief role is a question that will significantly impact the effectiveness of cybersecurity initiatives in today's increasingly digital business environment.
In the following sections, we will explore this subject in detail, drawing from the latest research, expert opinions, and case studies to build a comprehensive understanding of the CISO's role in the modern business landscape.
Genesis of IT Security
In order to truly appreciate the becoming of the CISO role, it is imperative that we examine how cyber security became part of an organization.
I remember the days when there was no such thing as cyber security. The word cyber, did not exist. There was only IT. And IT's primarily role was support. Users used personal computers, often networked so that each machine could talk to each other. Advent of Novell Netware with IPX/SPX based network, coaxiable cables run through the floors. Virus came about to infect floppy disks and TSR (terminate and stay resident) (you probably are guessing my age by now).

I used to walk around, started with a 5.25" floppy and then to more newer and higher capacity disks (or diskette). Cleaning such nuisance was the role of the computer technician. Annoyance, mischief rather than anything more. It was when computers become a business staple is when organizations realised they needed someone to take care of such nuisance. An IT technician was assigned to handle such issues. That single person was the security department. Responsible for managing the menace of computer viruses. One more person could no longer handle the load. It became 2, and started growing. Eventually like any other section, IT Security (as how it was christened before) became a section in IT. Organizations were touted "mature" for having such setup.
How did I know all this? I was the one person before, that became department, which morphed into the function that is today. Though my personal path was somewhat different, focused more towards Internet and ISP.
The legacy of IT Security is very much evident today. Even in large organizations you see almost by default IT Security reports to CIO.
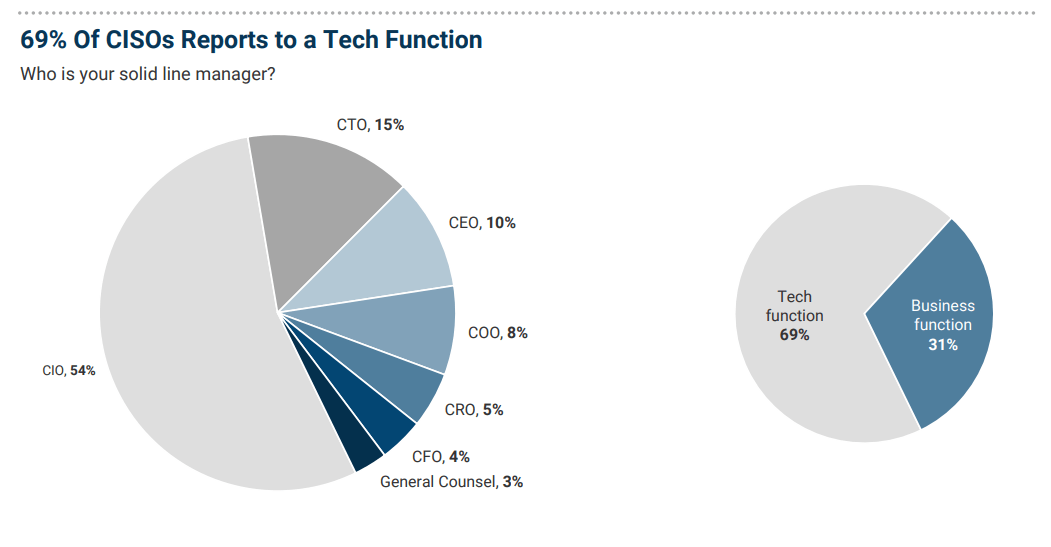
In a different article, I'll talk about who CISO should report to, although you'll see hints in this series.
Understanding the CISO Role
The CISO is a role that emerged out of necessity. As businesses began to digitize their operations, they realized the potential vulnerabilities that came with technology. Data breaches, cyber attacks, and operational disruptions due to technical failures became risks that businesses had to grapple with, leading to the creation of the CISO role. No more viruses (though there still are), but just like how technology evolves, so do threats.
A CISO's role revolves around developing and implementing a comprehensive information security program, which includes the creation of information security policies, procedures, and standards. Additionally, they are often tasked with incident response management, overseeing technology controls and recovery plans for any security breaches or interruptions.
I call it The single neck to choke when something cyber related happens!
On a more strategic level, CISOs are responsible for aligning the security strategy with business objectives. They are tasked with the duty of understanding the business's goals and ensuring that security measures do not hinder productivity or growth, while still mitigating risk. CISOs are changing to become business leaders rather than technical leaders, similar to CIO/CTO.
However, unlike other C-level executives, the role of a CISO is often more complex and multi-faceted. They have to balance between being a technical expert and a business strategist. They must navigate an ever-evolving landscape of cyber threats, regulatory requirements, and technological advancements while convincing the board of the need for substantial investments in security infrastructure, training, and staff. CISOs are tasked to make business design, taking cyber risk into consideration. To launch a product and not getting hacked.
A critical aspect that sets the CISO apart is the need for their role to be proactive rather than reactive. Unlike other roles, such as a CFO or a CTO, which can often rely on historical data and trends to make decisions, a CISO is tasked with predicting and preventing potential cyber threats before they occur. This requires not just a deep understanding of technology and security but also a keen understanding of the business and the unique threats it may face.
In the next section, we will compare the CISO role with other C-level executives, analyzing the similarities and differences, and exploring the debate on whether the CISO is a true or false C.
To be continued in Part 2...
Reference
[1] Who Does Your CISO Report To?. (2023). Retrieved 16 July 2023, from https://securityintelligence.com/articles/who-should-ciso-report-to/
[2] Who Should the CISO Report To?. (2023). Retrieved 16 July 2023, from https://www.iansresearch.com/resources/all-blogs/post/security-blog/2021/09/21/who-should-the-ciso-report-to