Microsoft identified a nation state attacker - named Storm0508 as of China origin. Identified beginning 15 May 2023, Storm-0558 used "forged authentication tokens" to access user email belonging to government agencies and consumers.
Who is Storm-0558?
Pinned as China nation state group by Microsoft with moderate confidence, due to consistency to espionage objectives. It is also observed to be some minimal overlaps to other Chinese groups, Storm-0558 is slated as its own distinct group. One of the artifacts confirming this is the consistent working hours in China (GMT+0800) which coincides with a lot of other SEA countries.
Targets include US/EU diplomatic, economic and legislative groups including individuals connected to Taiwan and Uyghur geopolitical interests. They also exhibit interest to think-tanks, telecommunications equipment and service provider organizations. They have keen interest in OAUTH applications, token based attacks against Microsoft accounts.
Post access activities include LSASS process memory extraction and SAM registry hive access. Using the legitimate credentials, the TA then accesses the system through valid credentials.
From the humble start of using Outlook Web Access and Exchange Online, the group graduated to stealing Azure AD tokens (with the assumptions of using malware).
What was not mentioned clearly is how the Azure AD access token was able to break into multiple organizations, which indicates that the token obtained may be a token with much higher privilege, the kind that is specially issued to a special class of users, belonging to 3-letter agencies.
Post Account Authentication
The TA uses the legitimate user access to then access the OWA API to retrieve a token which is meant for Exchange Online. Microsoft admits this was a design flaw and has subsequently fixed it.
TA tooling
The TA uses a collection of PowerShell and Python scripts against OWA Exchange Store service (most likely due to extensive internal hack-testing). TA has the capability to use minted access tokens to extract email data in order to download emails, attachments, locate and download conversations and get email folder information. To hide its activities, the TA uses SOCKS5 web proxy and masks its User-Agent.
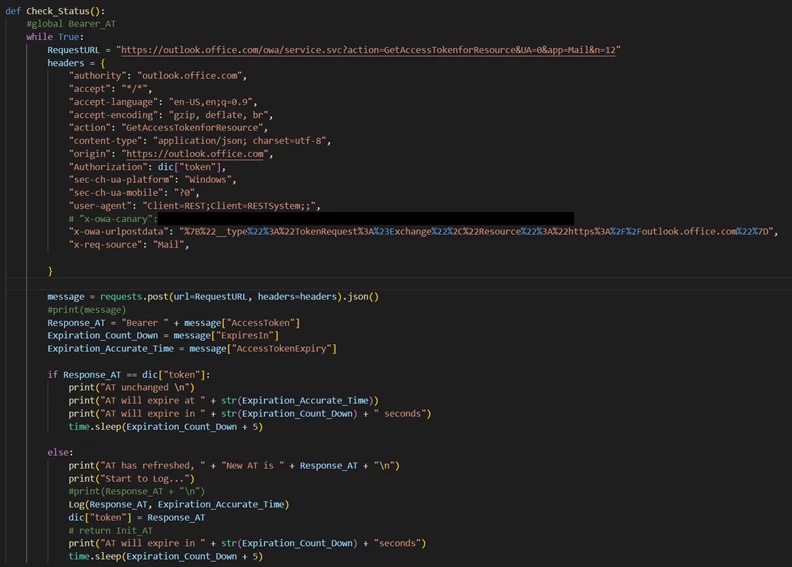
In order to execute the hack, the TA is found to be hosting dedicated infrastructure running the SoftEther proxy software. The Proxy masks the user origin, making it difficult to identify the actual source of the attack.
Independent news on the matter
As of July 14th, Micorosft was seen uncertain as to how the access was made so widespread (like what I mentioned earlier).
The incident was pinned to the stolen inactive Microsoft account (MSA) consumer signing key which is used to breach Exchange Online and OWA.
On June 27th, Microsoft also revoked all valid MSA signing keys to block all attempts to generate new access tokens and moved the newly generated ones to the key store that it uses for its enterprise systems.
"No key-related actor activity has been observed since Microsoft invalidated the actor-acquired MSA signing key," Microsoft said.
However, while Redmond has no longer detected any key-related Storm-0558 malicious activity after revoking all active MSA signing keys and mitigating the API flaw enabling, today's advisory says the attackers have now switched to other techniques.
"No key-related actor activity has been observed since Microsoft invalidated the actor-acquired MSA signing key. Further, we have seen Storm-0558 transition to other techniques, which indicates that the actor is not able to utilize or access any signing keys," Microsoft said.
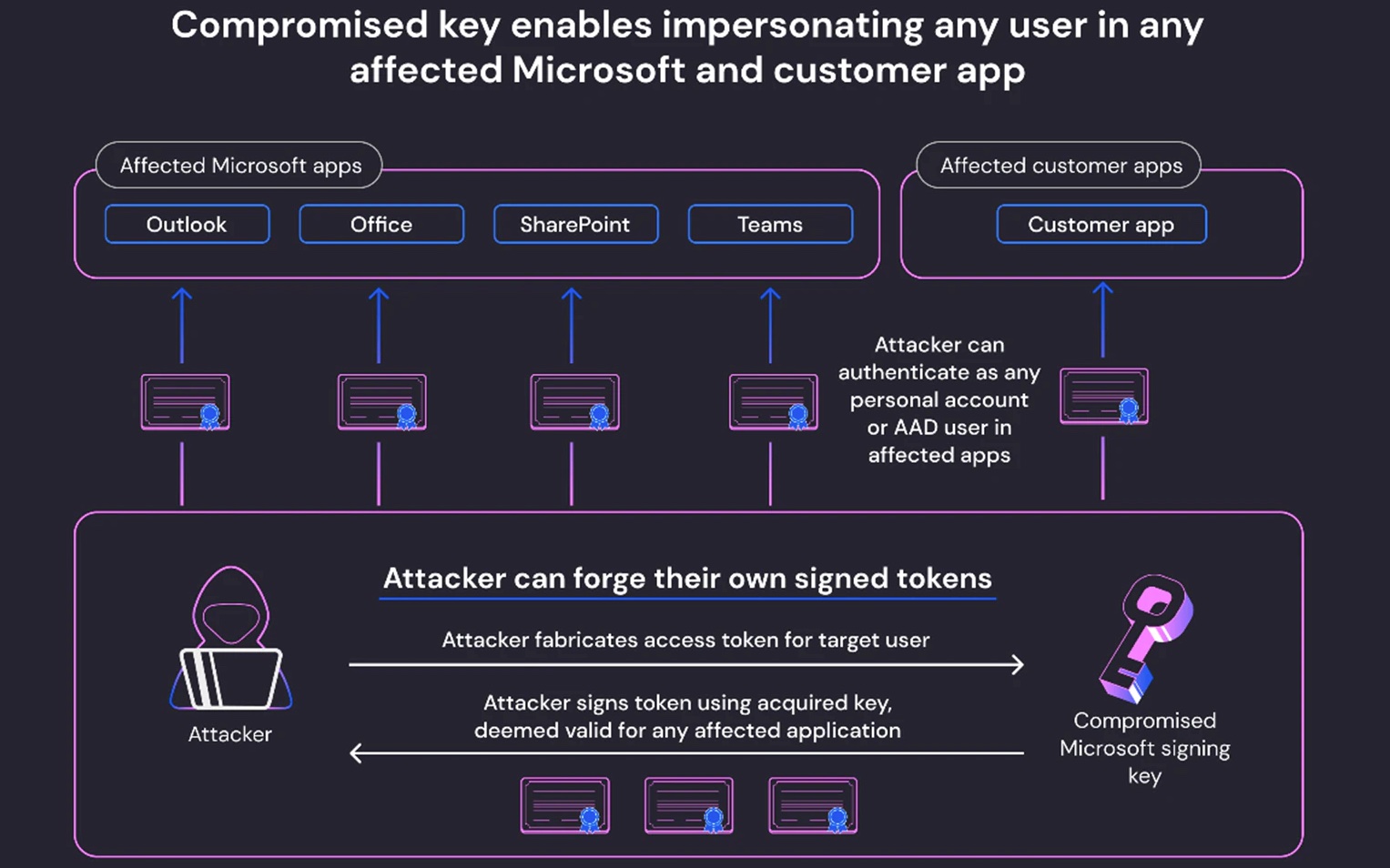
A third party vendor familiar with the matter, Wiz, mentioned that the MSA provided Storm0558 access far beyond Exchange Online and Outlook.com access.Simply put, using the key, the attacker can access ANY mailboxes on Microsoft platform.
Shir Tamari, the Wiz security researcher mentioned that the impact extended to all Azure AD applications using the Microsoft OpenID v2.0. This is due to the stolen key's capability to sign any OpenID v2.0 access token for personal and multi-tenant AAD applications.
"Everything in the world of Microsoft leverages Azure Active Directory auth tokens for access," Wiz CTO and Cofounder Ami Luttwak also told BleepingComputer.
"An attacker with an AAD signing key is the most powerful attacker you can imagine, because they can access almost any app – as any user. This is the ultimate cyber intelligence' shape shifter' superpower."
Glaring questions remain as to why such key was created and who uses it.
US Senator Ron Wyden took Microsoft to task, echoing other critics who blamed Microsoft for withholding key details about the incident. It was noted that Microsoft, in its articles used words such as "issues", "errors" and "flaws" at an attempt to PR manage the situation.
IOC
The following were the infrastructure seen being leveraged by the TA.
- 51.89.156[.]153
- 176.31.90[.]129
- 137.74.181[.]100
- 193.36.119[.]45
- 185.158.248[.]159
- 131.153.78[.]188
- 37.143.130[.]146
- 146.70.157[.]45
- 185.195.200[.]39
- 185.38.142[.]229
- 146.70.121[.]44
- 31.42.177[.]181
- 185.51.134[.]52
- 173.44.226[.]70
- 45.14.227[.]233
- 185.236.231[.]109
- 178.73.220[.]149
- 45.14.227[.]212
- 91.222.173[.]225
- 146.70.35[.]168
- 146.70.157[.]213
- 31.42.177[.]201
- 5.252.176[.]8
- 80.85.158[.]215
- 193.149.129[.]88
- 5.252.178[.]68
- 116.202.251[.]8
- 185.158.248[.]93
- 20.108.240[.]252
- 146.70.135[.]182
Here's an interesting part. The TA had developed analytics to proactively track dedicated infrastructure. Here are the infra identified.
- 195.26.87[.]219
- 185.236.228[.]183
- 85.239.63[.]160
- 193.105.134[.]58
- 146.0.74[.]16
- 91.231.186[.]226
- 91.222.174[.]41
- 185.38.142[.]249
References
[1] Compromised Microsoft Key: More Impactful Than We Thought | Wiz Blog. (2023). Retrieved 9 August 2023, from https://www.wiz.io/blog/storm-0558-compromised-microsoft-key-enables-authentication-of-countless-micr
[2] Goodin, D. (2023). US senator blasts Microsoft for “negligent cybersecurity practices”. Retrieved 9 August 2023, from https://arstechnica.com/security/2023/07/us-senator-blasts-microsoft-for-negligent-cybersecurity-practices/
[3] Gatlan, S. (2023). Microsoft still unsure how hackers stole Azure AD signing key. Retrieved 9 August 2023, from https://www.bleepingcomputer.com/news/microsoft/microsoft-still-unsure-how-hackers-stole-azure-ad-signing-key/
[4] Gatlan, S. (2023). Stolen Microsoft key offered widespread access to Microsoft cloud services. Retrieved 9 August 2023, from https://www.bleepingcomputer.com/news/security/stolen-microsoft-key-offered-widespread-access-to-microsoft-cloud-services/