*The inspiration of this articles comes from @xanda who shares the reference to this article. *
Precursor
The UK Foreign, Commonwealth & Development Office (FCDO) recently funded ShadowServer to provide a detailed report on cyber threat insights affecting ASEAN countries, namely Malaysia, Singapore, Thailand and Philippines.
These activities included obtaining a better understanding of the device makeup of the exposed attack surface in those countries, vulnerability exposure (especially relating to emerging threats) and observed attacks/infected devices – coming both from and directed at the region.
The intention is to enrich Shadowserver’s free daily threat feeds and public benefit services to the region, providing National CSIRTs and other system defender entities (organizations that are network owners) with a better awareness of their threat and vulnerability landscape, thus helping them to improve their cybersecurity posture.
Methodology
Shadowserver performs detection fingerprinting for devices in the region, as part of their daily Internet scanning. Your home router would have been fingerprinted as you read this article. Fingerprinting means the abilit to identify vendor, type and model of the publicly exposed devices, such as home routers.
Why are home routers exposed to the Internet? The ISP usually dishes out public IP address, either single or a subnet (especially for IPv6). When your home router connects and authenticates to the ISP, your home router gets a public IP address, making it reachable from the internet.
Then how about devices connected to the home router? For IPV4 which is the current default for routers, you will receive a private IP address, namely 192.168.x.x range. For more information about private IP address, refer to RFC 1918 document from IETF. To understand how internally connected devices can share a single IP address, read further on Network Address Translation, read RFC 1631 and RFC 2663.
Lets look at the data
We look for Malaysian data first.
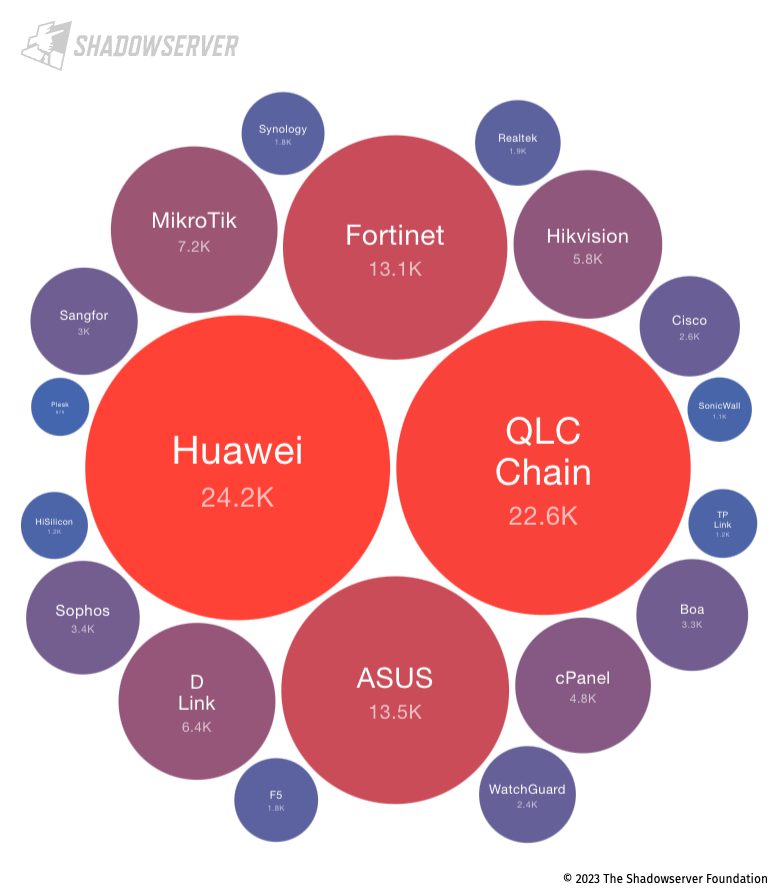
Malaysia has large penetration of Huawei, QLC Chain, Asus, Mikrotic and Hikvision.
Huawei is prevalent in MY due to the usage of home routers distributed by the respective ISP. Fiberhome is a router that is provided by the key fiber instructucture ISP, namely Telekom Malaysia Unifi and Time Telekom.
The use of Fortinet is prevalent in corporate sectore as a device of choice as the front line of defense.
Consumer brands such as Asus, D-Link forms the next big cluster of devices. An interesting brand that appears is Hikvision, which is prevalent brand in Malaysia for CCTV. Most likely the Hikvision device is used as both router and CCTV recording (not a good idea to me, while users may want to be able to access their CCTV from the public internet).
QLC Chain is a “next generation public chain for Network-as-a-Service (NaaS)”, which now appears to be unmaintained (meaning no further firmware update and likely candidate for exploitation). QLC Chain device detections are mostly the result of CoAP exposure. Constrained Application Protocol (CoAP) is a specialized web transfer protocol for use with constrained nodes and constrained networks such as in the Internet of Things (IoT). QLC Chain is also seen as number 1 most devices in Philippines.
Vulnerable devices
It is worth noting that a relatively high number of likely vulnerable devices remain publicly exposed in the region. These include Fortinet devices vulnerable to CVE-2022-42475, a FortiOS SSL-VPN heap based buffer overflow vulnerability, with nearly 900 Fortinet installations across the region (with almost half of those in Thailand):
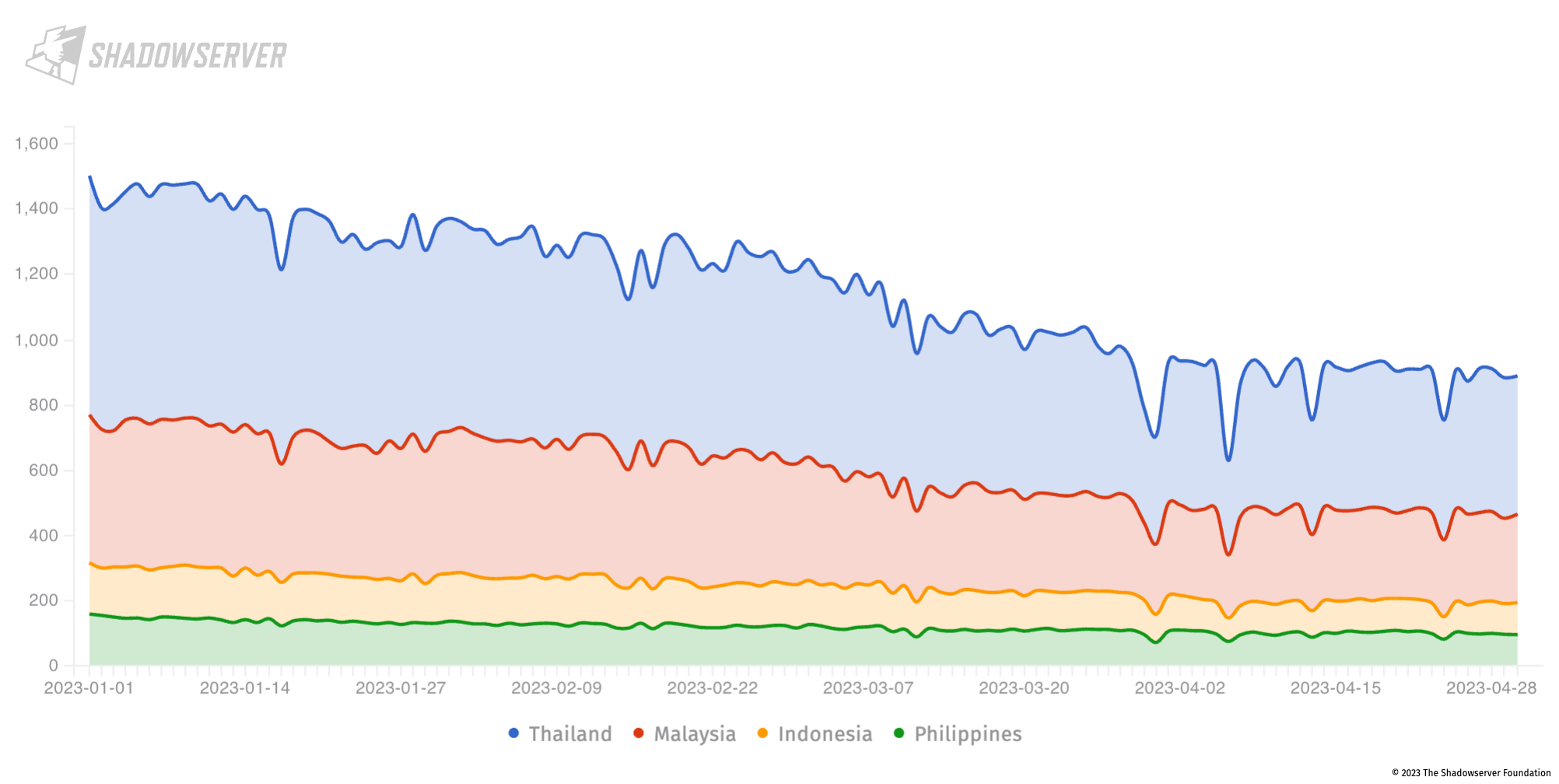
Many Microsoft Exchange servers remain infected with cryptominers, such as DLTminer (around a 1000), particularly in Malaysia and Indonesia.
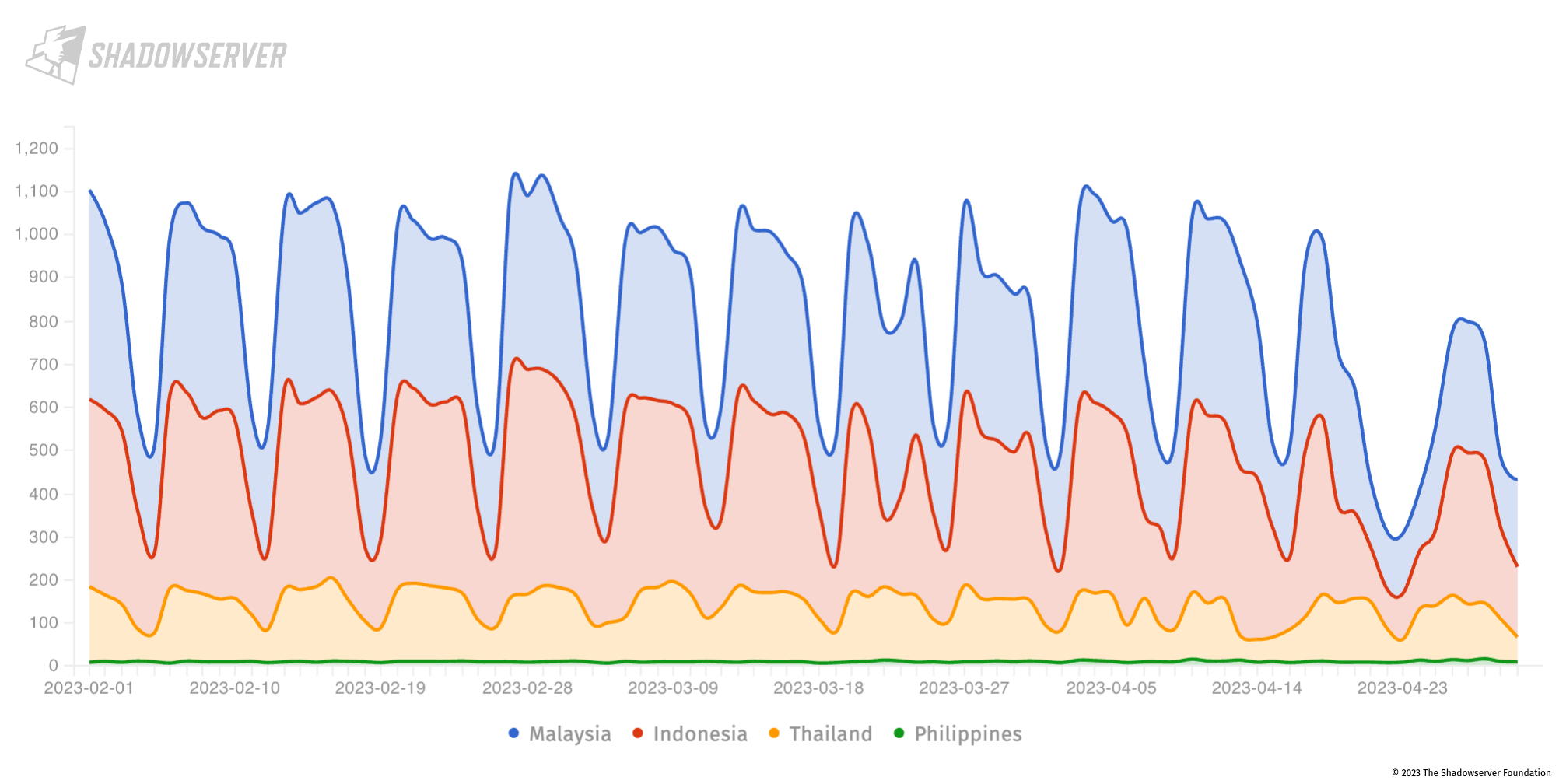
On 2021-03-02, Microsoft released out-of-band patches for Microsoft Exchange Server 2013, 2016 and 2019. These security updates fixed a pre-authentication remote code execution (RCE) vulnerability chain (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065) that allows an attacker to take over any reachable Exchange server, without even knowing any valid account credentials.
These vulnerabilities were first discovered by Orange Tsai, a well-known vulnerability researcher, who reported them to Microsoft on 2021-01-05. However, according to a blogpost by Volexity, in-the-wild exploitation had already started on 2021-01-03. Thus, if these dates are correct, the vulnerabilities were either independently discovered by two different vulnerability research teams or that information about the vulnerabilities was somehow obtained by a malicious entity. Microsoft also published a blogpost about the early activity of Hafnium.
On 2021-02-28, it was noticed that the vulnerabilities were used by other threat actors, starting with Tick and quickly joined by LuckyMouse, Calypso and the Winnti Group. This suggests that multiple threat actors gained access to the details of the vulnerabilities before the release of the patch, which means we can discard the possibility that they built an exploit by reverse engineering Microsoft updates.
(Is your exchange server infected?)
Devices on attack mode!
Shadowserver attempts to identify devices detected attacking its honeypot sensors (and attempting to utilize the sensor to perform Distributed Denial of Service (DDoS) attacks).
In Malaysia, MikroTik are the most commonly observed infected devices, followed by embedded Boa devices and FiberHome devices. Seems like ISP distributed devices isn't being maintained properly!
For Thailand, attacking infected devices are MikroTik and also devices running the Boa webserver (these may actually be multiple vendors). Development of Boa webserver was discontinued in 2005(!), but the unsupported software continues to be used by multiple manufacturers. For more background on Boa related attacks, see the Microsoft article “Vulnerable SDK components lead to supply chain risks in IoT and OT environments”.
For Indonesia, MikroTik infections are unsurprisingly prevalent due to the high concentration of those devices in the country. We also see a significant number of Fortinet infections.
In addition, we see Ubiquiti Unifi controllers and Zimbra servers used for DDoS attacks (note the vulnerable population of Zimbra servers in Indonesia compared to other countries discussed earlier).
If you are using Ubiquiti Unifi infrastrucutre, best to keep them in the internal network and update the stack as soon as possible.
The Philippines is the only country that breaks the daily majority MikroTik pattern, with FiberHome and Huawei Home Gateway devices typically occupying the top classifications of infected devices.
Note, however, that for DDoS attacks originating in this region, ShadowServer predominantly observe MikroTik devices attacking from the Philippines.
Finally, it is worth noting that Hikvision and HiSilicon based DVRs are the most commonly infected video system devices in the region.
Next steps
For most people, this wouldn't be a concern. In reality, home internet infrastructure is as critical as an organization, as it becomes a convenient and easy target to be zombie botnets and launch proxies for malicious activities. Threat Actors are seen using these infrastructure to hide their activities.
ISP distributed devices need to be properly maintained and updated to avoid having any vulnerabilities. Assuming a user will go in and manage the router is rather unreasonable for an average user. The more prosumer type of users will be able to manage their devices, plus the newer version of device also comes with auto-update features (Yes I know there are some manufacturers who b0rked their auto update features, which was promptly fixed.
National CSIRT and relevant agencies need to pick up their pace and ensures that devices sold needs to have updates to prevent user devices from not being secure. This can be from an administrative stance, having necessary regulations for devices that are internet connected to be use-worthy.
Reference
[1] Observations on cyber threat activity and vulnerabilities in Indonesia, Malaysia, Philippines and Thailand | The Shadowserver Foundation. (2023). Retrieved 6 June 2023, from https://www.shadowserver.org/news/observations-on-cyber-threat-activity-and-vulnerabilities-in-indonesia-malaysia-philippines-and-thailand/
[2] https://www.welivesecurity.com/2021/03/10/exchange-servers-under-siege-10-apt-groups/