In early 2023, Unit 42 researchers began investigating a series of espionage attacks that targeted a government in Southeast Asia. These attacks focused on different governmental entities in the same country, including critical infrastructure, public healthcare institutions, public financial administrators and ministries.
This appeared at first glance to be the activity of a single threat actor. Careful analysis, however, revealed the attacks to have been carried out by separate threat actors whose activities group into three distinct clusters. While this activity occurred around the same time and in some instances even simultaneously on the same victims’ machines, each cluster is characterized by distinct tools, modus operandi and infrastructure.
The techniques and tools observed during the attacks, along with the persistent long-term surveillance efforts made by the different attackers, suggest the work of advanced persistent threats (APTs). In their analysis, they were able to attribute the three clusters to known APT groups with different levels of confidence.
The Unit 42 system for defining and tracking threat adversaries provides a framework for grouping similar behaviors, tools, infrastructure and tradecraft, and then assigning names to the resulting clusters. When Unit 42 applied this framework to the attacks that was observed, they broke the clusters down as follows:
- The activity observed in the first cluster (tracked as CL-STA-0044) is attributed with moderate-high confidence to the well-known Stately Taurus group (aka Mustang Panda), a group believed by the security community to be affiliated with Chinese interests.
- The activity observed in the second cluster (tracked as CL-STA-0045) is attributed with a moderate level of confidence to the Alloy Taurus group (aka GALLIUM). This group is also believed to be operating on behalf of Chinese state interests.
- Lastly, the activity observed in the third cluster (tracked as CL-STA-0046) is attributed with a moderate level of confidence to the Gelsemium group, which so far has not been formally attributed to any specific state.
This research offers a glimpse into the intricate and clandestine world of nation-state cyberespionage, in which multiple critical government entities of one country were compromised.
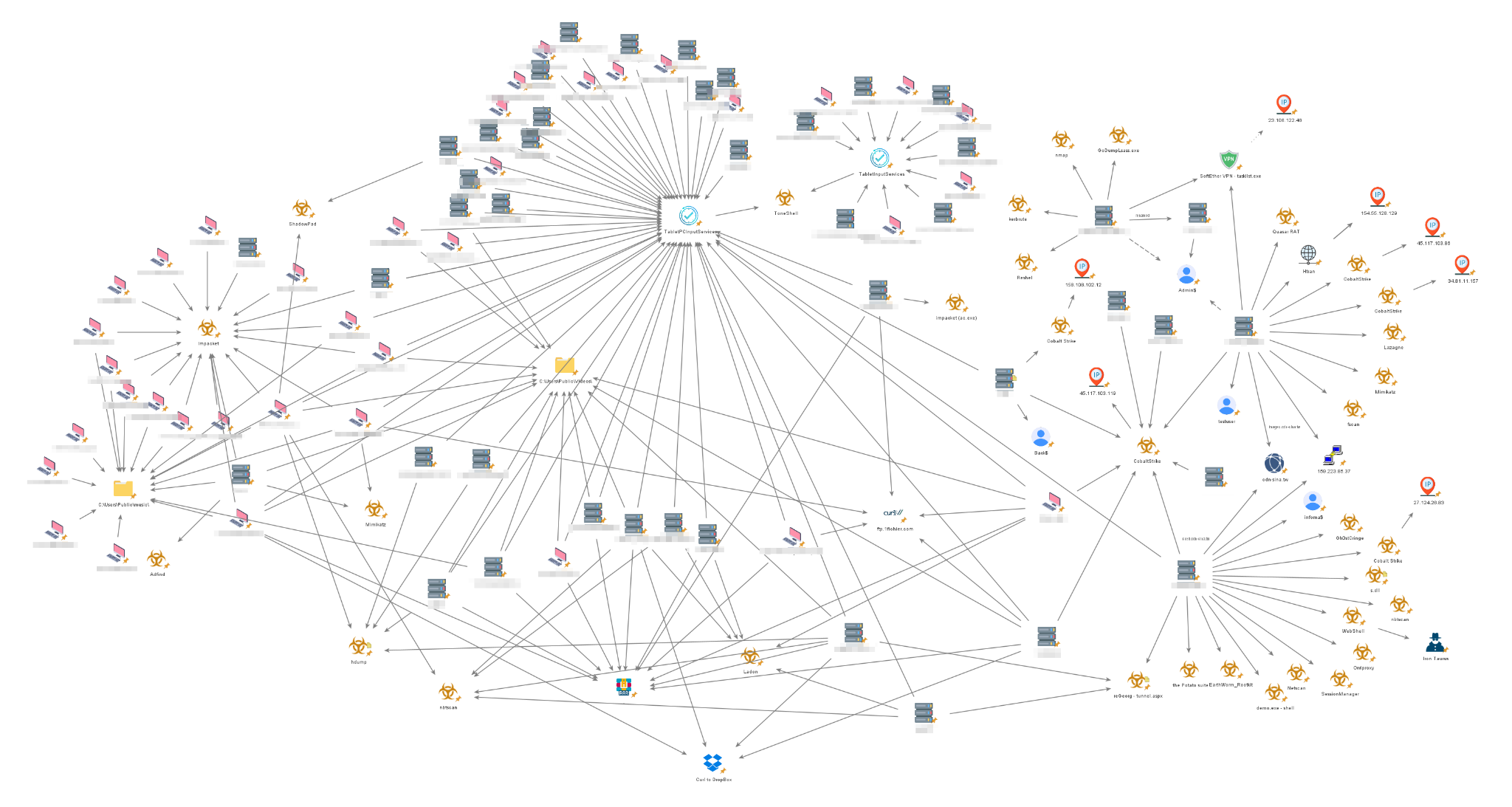
The diagram above provides a comprehensive visual overview of the overall observed activities, prior to the breakdown by clusters of activity. It includes the TTPs employed by the threat actors and the affected machines within the environment.
Each cluster had its own unique characteristics, which allowed Unit 42 to define each one separately. The clustering and attribution process Unit 42 used was based on the Diamond model of attribution, allowing for a comprehensive understanding of the threat landscape.
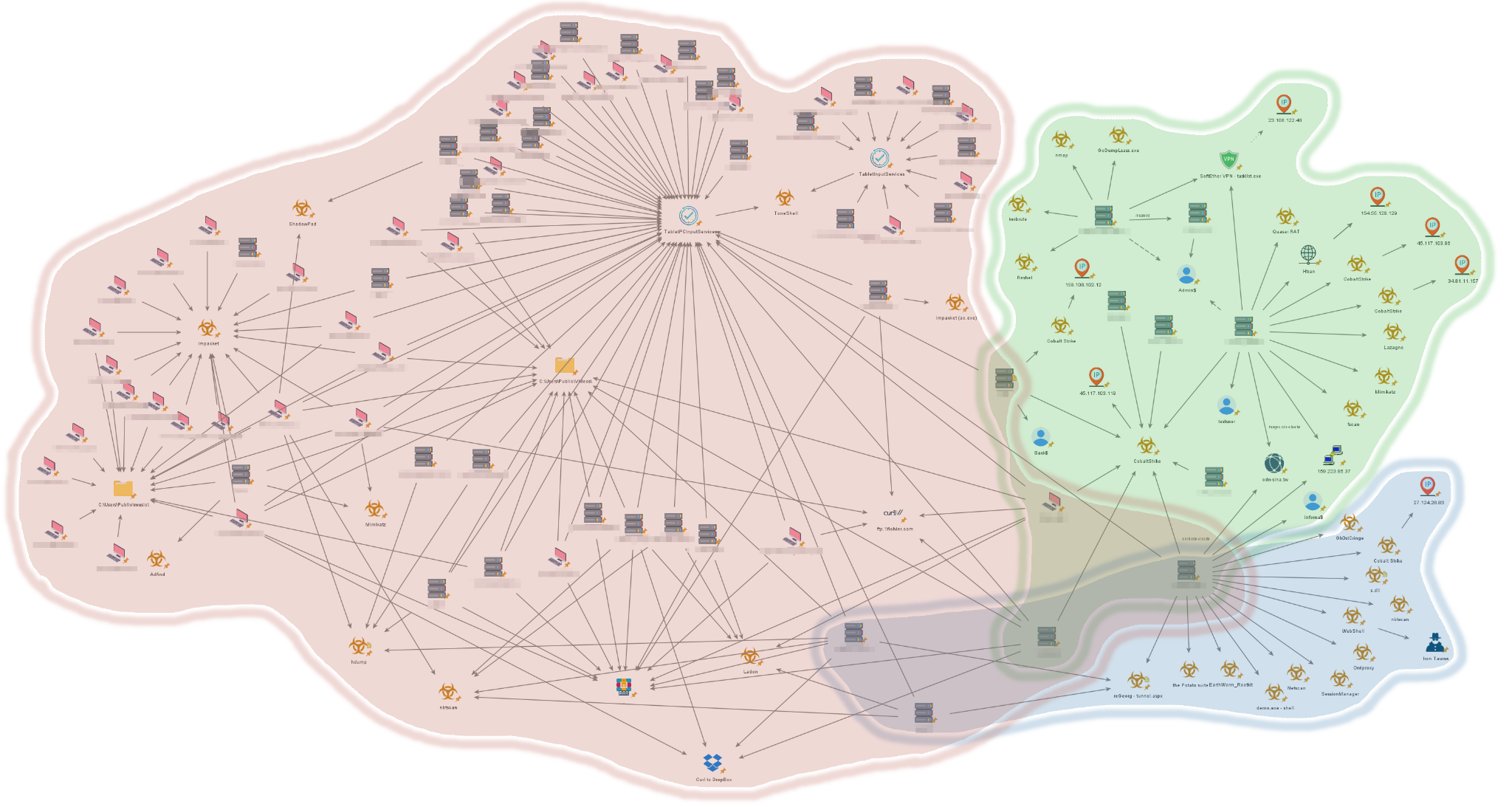
Understanding each cluster
CL-STA-0044 (Approximately Q1 2021-Q3 2023)
The activity observed in this cluster is attributed with moderate-high confidence to the APT group Stately Taurus. Analysis of the activity suggests that the attackers conducted a cyberespionage operation that focused on gathering intelligence as well as stealing sensitive documents and information, while maintaining a persistent and clandestine foothold.
The attackers used two main backdoors. The first one was an undocumented variant of the ToneShell backdoor. The second backdoor was ShadowPad, a complex and modular backdoor known to be exclusively used by Chinese APT groups.
The attackers also used a range of known hacking tools, such as the following:
- LadonGo
- Impacket
- China Chopper web shells
- Scanning and credential dumping tools
CL-STA-0045 (Q1 2022-Q3 2023) The activity observed in this cluster is attributed with a moderate level of confidence to the Alloy Taurus APT group. Analysis of the activity shows that the attackers were mainly focused on the following activities:
- Establishing long-term persistence
- Reconnaissance missions
- Obtaining and maintaining access through a variety of activities
- Various backdoors
- Web shells
Prolific credential-gathering activities The attackers attempted to remain under the radar by using uncommon techniques and by circumventing several security products.
The main tools observed in this cluster included two previously unknown backdoors, Zapoa and ReShell, first identified by Unit 42 researchers. Moreover, the attackers also used known malware and hacking tools such as the following:
- GhostCringe remote access Trojan (RAT)
- Quasar RAT
- Cobalt Strike
- Kerbrute brute forcing tool
- China Chopper web shell
CL-STA-0046 (Q3 2022-Q4 2022)
The activity observed in this cluster is attributed with a moderate level of confidence to the Gelsemium APT group. Analysis of the activity shows that the attackers mainly focused on reconnaissance and maintaining access activities, specifically targeting vulnerable IIS servers.
The two main, unique types of malware used in this cluster were OwlProxy and SessionManager. The combination of these distinct tools has only been observed in past attacks that other researchers have attributed to Gelsemium.
In addition, the attackers used more common tools such as the following:
- Cobalt Strike
- Meterpreter
- Earthworm
- Spoolfool
My analysis
If you look purely at tooling, the attackers used a combination of bespoke/private customized tooling in combination with publicly available tools. This makes the factor of attribution harder. Tools such as CobaltStrike continues to be a favorite amongst attackers.
Defensive strategies for organizations and governments for a start, is to invest on capabilities and skillset in improving detection against publicly available tools. Coupled with deep packet inspection, incorporating IOC feeds into block lists and vigilant traffic monitoring, both North-South and East-West with cyber land mines in the form of honeynets, honey tokens would make it more difficult for attackers to penetrate through. As I always mention, moving from noise to high fidelity alerts would be key in detecting and mitigating such attacks.
Reference
[1] Lior Rochberger, T. F. (2023). Unit 42 Researchers Discover Multiple Espionage Operations Targeting Southeast Asian Government. Retrieved from https://unit42.paloaltonetworks.com/analysis-of-three-attack-clusters-in-se-asia/
[2] Lior Rochberger, T. F. (2023). Rare Backdoors Suspected to be Tied to Gelsemium APT Found in Targeted Attack in Southeast Asian Government. Retrieved from https://unit42.paloaltonetworks.com/rare-possible-gelsemium-attack-targets-se-asia/
[3] Sergio Caltagirone. Diamond Model of Intrusion. Retrieved from https://www.threatintel.academy/wp-content/uploads/2020/07/diamond_summary.pdf