One of the things that always gets to me, which seems to be constantly propagated by the industry whose addicted to fear, uncertainty and doubt is outdated security controls/advice. I covered at length some of these issues in my previous articles.
Bane of existence
Ask anyone, one of the most serious problems everyone has is passwords.
If someone banishes regular password changes, wouldn't you cheer for that person? Well, the Microsoft CISO did and he was applauded for that.
Microsoft qualified that move by ensuring that MFA is applied corporate and environment wide. Having MFA eliminates the need for regular password changes.
Microsoft updated its password policy in stages. In January 2019, it moved to one-year expiry, using telemetry to validate effectiveness. In January, 2020 it moved to unlimited expiry based on the results.
Microsoft also stopped recommending to customers to implement a 60-day password expiration policy in 2019 because people tend to make small alterations to existing passwords or forget new good ones.
Protecting accounts with MFA won't stop attackers completely, but it does make their lives harder by shielding an organization from the inherent weaknesses in usernames and passwords to protect accounts, which can be phished or compromised through password-spraying attacks.
The latter technique, which relies on password re-use, was one way the SolarWinds attackers breached targets besides breaking into the firm's software build systems to spread a tainted software update.
Microsoft's CISO said "Everyone has brownfield apps that can't support modern authentication, such as biometrics, and so I think what a lot of people should and need to do is take a risk-based approach: first get MFA enforced for high-risk/value groups like admins, HR, legal group and so on, and then move to all users. It can be a multi-year journey, depending how quickly you want to do something"
Let's be clear, Microsoft did have their fair share of being breached. But their breaches (aka Solarwinds) had nothing to do with passwords, but a supply-chain attack, abusing trust.
My experience
Unfortunately, during my previous tenure, I was responsible in increasing character length of passwords, to almost double of the character size previously used.
Initially it was met with disgrunts, grumbling and unhappiness. And suddenly it all stopped. I was curious to know what happened.
I asked one of the staff on how they manage this "migration". His answer made me think even harder.
"Boss, very easy. Last time, we only change the last 2 digit for every password change. Now, we repeat the same password twice and keep the 2 digits at the back! The old password is "nasilemak21", then the new password will be "nasilemaknasilemak21"!
**Did security actually improve? **
I was beginning to think that the user creativity in managing and circumventing security controls is limitless!
Towards password-less
Just like wireless, its not about no-wires, but less wires, actually!
To move towards this, requires a serious push using MFA everywhere.
In my view, I foresee passwords to be default control for most systems for the next 1-2 decades, before we get better at authentication. This is despite Google is leaning heavy towards FIDO2 and recently integrated Quantum Resistant algorithms in their FIDO2 keys.
My advice, get a FIDO2 key and start protecting your own kingdom!
What do other say?
At times, the security boffins often refer to PCI-DSS, being the payment card standard. In this case, Microsoft is PCI-DSS compliant, while maintaining the stance of not changing passwords.
Here's what PCI-DSS say about passwords.
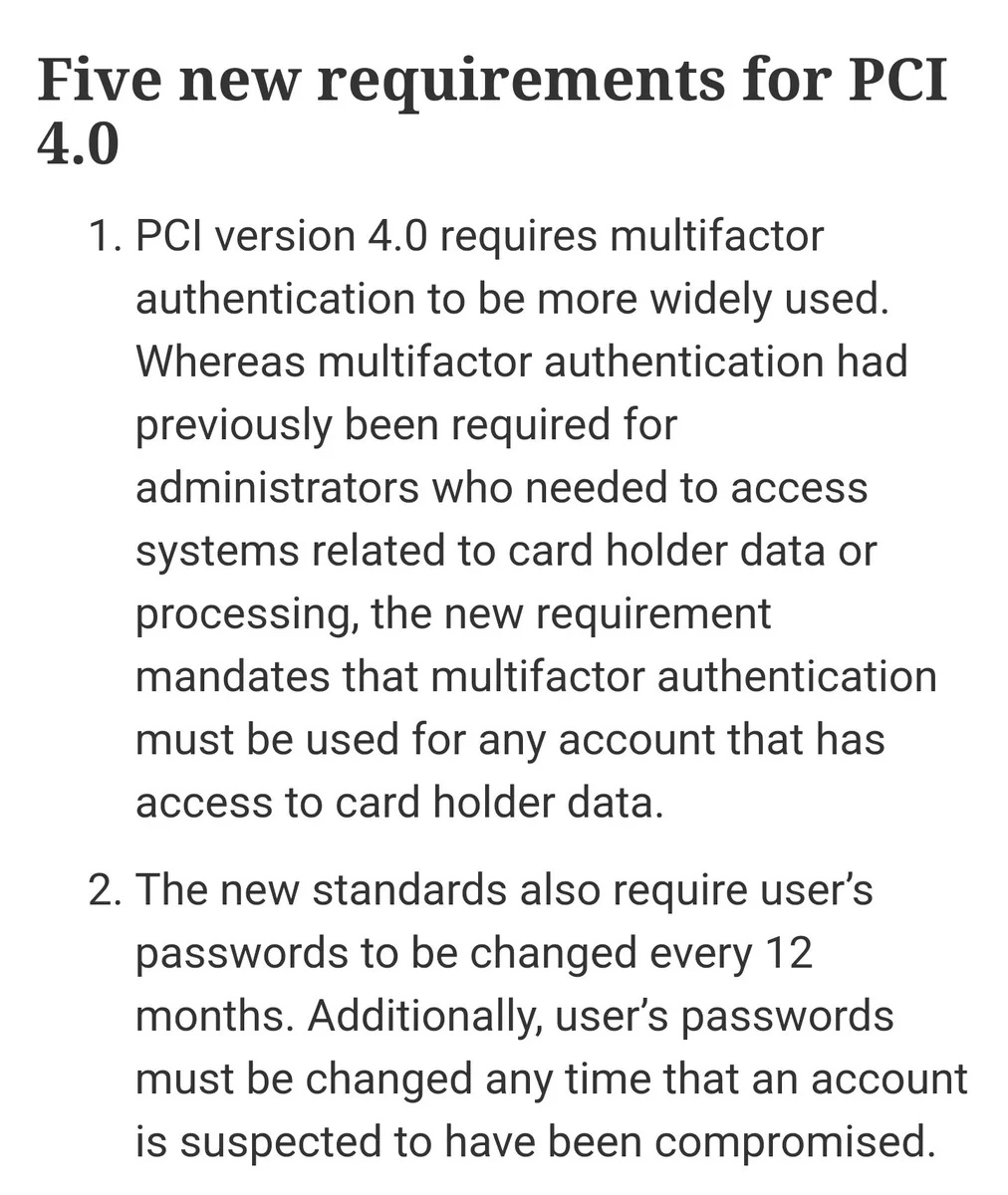
One more thing, PCI-DSS only applies to system that handles credit card payment information. Your average worker most lkely isn't part of the equation.
What about Malaysia?
I made references to BNM RMIT, and first thing I found is the document has 16 references to the word "password",
10.57 talks about secure password generation and checking password strength (indirectly length and complexity). Still nothing about moving into passwordless environment.
In my opinion, there may be 2 reasons for this. First, BNM is probably in the opinion that MFA/2FA will still take a longer time before its environment wide implementation. Secondly, passwords are the only minimal friction control, looking at a number of legacy systems that financial institutions deploy.
So, if you're a progressive and forward thinking CISO, you're most likely not meet BNM's RMIT requirements. Imagine you are required to ensure sufficient password strength (long length password), even if you have MFA configured.
Reference:
[1] Microsoft's CISO: Why we're trying to banish passwords forever. (2023). Retrieved 21 August 2023, from https://www.zdnet.com/article/microsofts-ciso-why-were-trying-to-banish-passwords-forever/
[2] Microsoft (2023), Using risk detection for user sign-ins to trigger Azure AD MFA. Retrieved from https://learn.microsoft.com/en-us/azure/active-directory/authentication/tutorial-risk-based-sspr-mfa
[3] Bank Negara Malaysia (2023), Risk Management in IT. Retreived from https://www.bnm.gov.my/documents/20124/963937/Risk+Management+in+Technology+(RMiT).pdf/810b088e-6f4f-aa35-b603-1208ace33619?t=1592866162078