Recent "leaked" announcement from Ledger had raised furore from the cryptocurrency and security commumity on the security of it's hardware wallet. I'll run through this, as many people rely on the sanctity of the hardware wallet to protect their investments.
What is the Ledger Hardware Wallet?
The Ledger hardware wallet is a popular and highly secure device designed to store and manage cryptocurrencies. It provides an offline, tamper-proof environment for securely generating and storing private keys, which are essential for accessing and managing cryptocurrency assets. Here's a detailed explanation of how a Ledger hardware wallet works:
- Secure Chip: The Ledger hardware wallet incorporates a specialized secure chip (Secure Element) that is designed to store sensitive information and perform cryptographic operations. This chip is resistant to physical attacks and has been certified against various security standards.
- Private Key Generation: When setting up a Ledger wallet, the device generates a random seed phrase (usually 24 words) known as the "recovery phrase" or "seed." This phrase acts as a master key from which all the private keys for various cryptocurrencies are derived. It is crucial to securely store this phrase since it is the ultimate backup for accessing the wallet.
- Offline Operation: The Ledger wallet is an offline device, meaning it does not directly connect to the internet. This offline operation ensures that the private keys never leave the device, reducing the risk of exposure to online threats and malware.
- Wallet Software: To interact with the Ledger hardware wallet, users install the Ledger Live software on their computer or mobile device. This software acts as a bridge between the hardware wallet and the blockchain networks. It allows users to manage their cryptocurrency assets, check balances, send and receive transactions, and install compatible wallet applications.
- Transaction Signing: When initiating a transaction, the wallet software prepares the transaction details, such as the recipient address, amount, and network fees. This information is then sent securely to the Ledger hardware wallet for signing. The private key stored within the secure chip signs the transaction, ensuring its integrity and authenticity.
- Display and Verification: The Ledger hardware wallet has a small built-in display that shows transaction details, including the recipient address and transaction amount. This display allows users to review and verify the transaction details before approving and signing the transaction.
- Physical Button Confirmation: The Ledger hardware wallet typically has physical buttons that users press to confirm or reject transactions. This manual confirmation ensures that users have complete control over authorizing transactions and prevents malicious software from initiating unauthorized transactions.
- Pin Code Protection: To access the Ledger hardware wallet, users are required to set up a PIN code. This PIN code adds an extra layer of security by preventing unauthorized access to the device in case of physical theft or loss. The PIN code is entered using the wallet's buttons, and several failed attempts will trigger a device wipe to protect against brute-force attacks.
- Firmware Updates: Ledger regularly releases firmware updates for its hardware wallets to address security vulnerabilities, improve functionality, and support new cryptocurrencies. Users are encouraged to keep their devices up to date by installing these updates through the Ledger Live software.
Reasoning for Hardware Wallet
Hardware wallets are physical devices that store your private keys offline, making them highly secure and resistant to hacking and cyber-attacks. They typically come with additional security features, such as a PIN code or biometric authentication, and can support multiple cryptocurrencies. However, hardware wallets can be more expensive than software wallets. They can also be more cumbersome to use, as they require you to connect the device to your computer or smartphone whenever you want to make a transaction.
The appeal for hardware wallets has always been security. The keys inside the hardware wallet are non-exportable, meaning that you will need that wallet to access your account. If you lose the hardware wallet, it's like you lose your real wallet. Not getting it back.
New Ledger Recover service
The core premise of the offering is the ability to (supposedly) encrypt parts of your seed phrase into 3 pieces, give over your identity + a selfie recording, and then trust 3 custodians to secure those shards for you.
Here's why that's problematic as @sethforprivacy explains it.
To own a wallet, you do not have to disclose your identity. Meaning that a random long string represents your wallets and has no distinguishable property.
In order to use the system at all, you have to connect your identity to your Ledger account, giving yet another KYC pain-point for data leaks, hacks, and government censorship or surveillance.
Now you're trusting a third party with info on your ID and info on all your crypto.
Not only can leaks or hacks occur, the sales of data on users of Ledger would be extremely valuable now and in the future, and any of the "authorized third parties" could decide to leverage your data as an income stream at any moment.
Most Ledger users use Ledger Live, software that uses Ledger's nodes for all wallet sync, revealing every detail of your cryptocurrency activity and making it trivial for Ledger to link this to your ID itself. For those privacy conscious people, you may not want this at all!
The KYC bit is handled by OnFido. They keep your ID, pictures/videos/sounds from your selfie video, and a holistic picture of your device and current activity when you upload/verify identity.Onfido has a complete picture of your identity and the fact that you are a Ledger user, and thus that you hold a reasonably large amount of cryptocurrency. Think about targetted phishing when there is a data breach!
They also have a holistic picture of the device you use for auth:

Ledger Architecture
This will be important for the following discussion in this article.
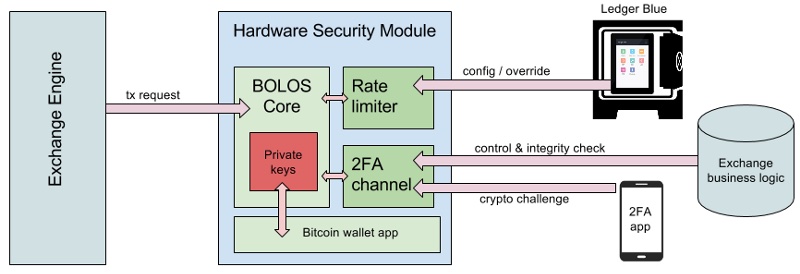
So now not only are you trusting Ledger and "authorized third parties" with your identity data, you're trusting Onfido with that and much more along with the knowledge that you hold and use large amounts of cryptocurrency.
This said, when you buy the Ledger product, you explicitly trust Ledger 100%. You trust that their firmware update is to ensure that your devices stay secure and supports updated blockchain requirements.
If all works as said, in theory your seed never leaves your device in an unencrypted state. We cannot verify this and be sure it's done securely or encrypted properly, however.
But this does mean there is now code running on your Ledger designed to send your seed over USB/BT.Not only does this mean that the wallet you thought made sure your seed never left the device can now become "hot" with a few key presses.
That also opens up massive new attack vectors for phishing and malware that can prompt you accidentally send your seed phrase to attackers.
At this point, it is unclear that the parts of the seed secured by the 3 parties can only be decrypted by the user themselves. What's completely unclear is how this decryption process during restore actually works.
You have to login and verify your ID, but if decryption can only happen on your device, how does your new device get the decryption key?
Normally in E2EE schemes you need a way to approve a new device and send it the decryption key, but in the case of losing your Ledger you cannot do that, so someone else must have a copy of the decryption key they send to your Ledger when you recover. (THIS SHOULD NEVER BE THE CASE!!!)
Who in the world has this decryption key? Is it Ledger? Is it somehow encrypted behind your Ledger Recover login + ID verification?
If so, how is it stored, what encryption is used, and how can we verify any of this?
The key risk is if anyone were to know that you used Ledger Recover and get your identity (Ledger isn't exactly known for their cybersecurity practices) they can now theoretically steal all of your cryptocurrency despite your Ledger sitting safe and sound in a drawer somewhere.
Lastly, this opens up massive government/LE seizure risks, as at least one custodian (CoinCover) and the identity provider (Onfido) are UK-based.The third custodian is not named in the official docs but was previously revealed to be EscrowTech.
If EscrowTech is still the third custodian they are US-based, which would put 2/3 companies within 5-eyes jurisdiction (UK and the US). The government can easily come knocking and request all holders ID information and then seize funds at will.
Seizing money is already as easy as freezing bank account. Now freezing crypto-assets will be as easy as taking over the decryption key!
Why this service?
I am inclined to think that the motivation for this move by Ledger is service monetization (without downplaying governmental pressure).
Selling a wallet is a one time thing. A USD20 hardware sold for USD100 is just a one time revenue. Tying it to a recurring service gets recurring income.
Most recent update
Not too long ago, Ledger emphasized that their key store ie secure.
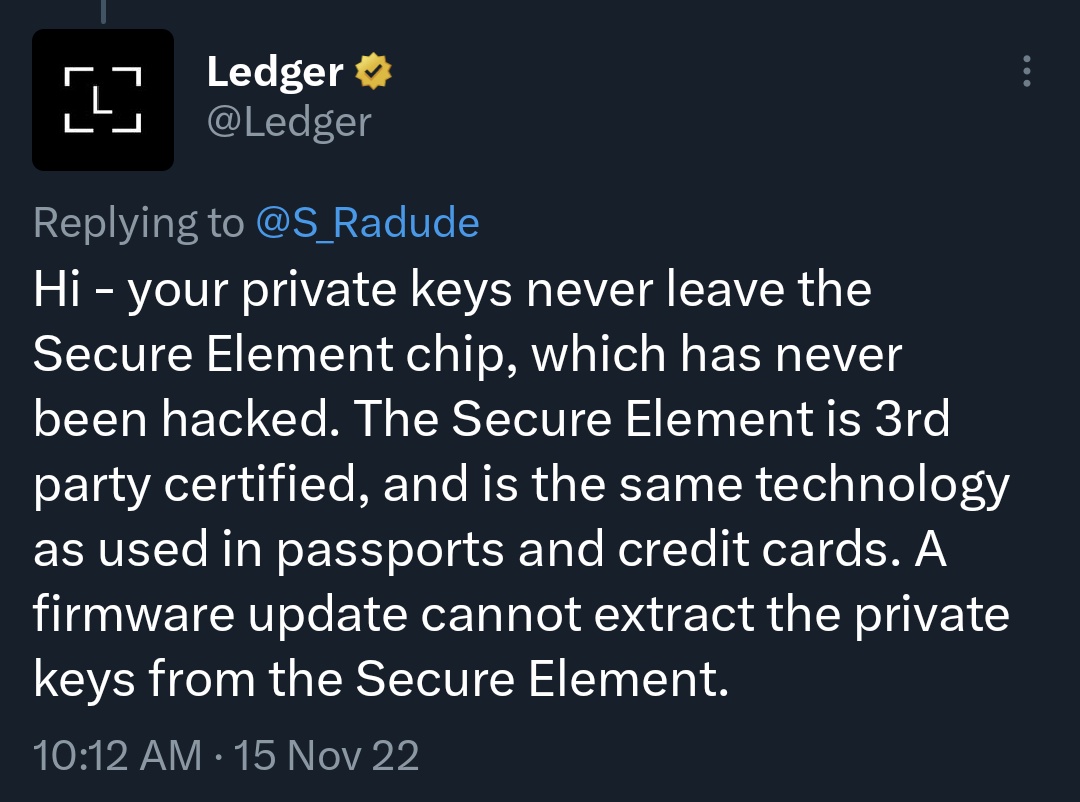
It seems that Ledger had removed the firmware 2.21, only leaving the 2.10 firmware on the update site. My guess is that the backlash from the community has set their plans in a halt.
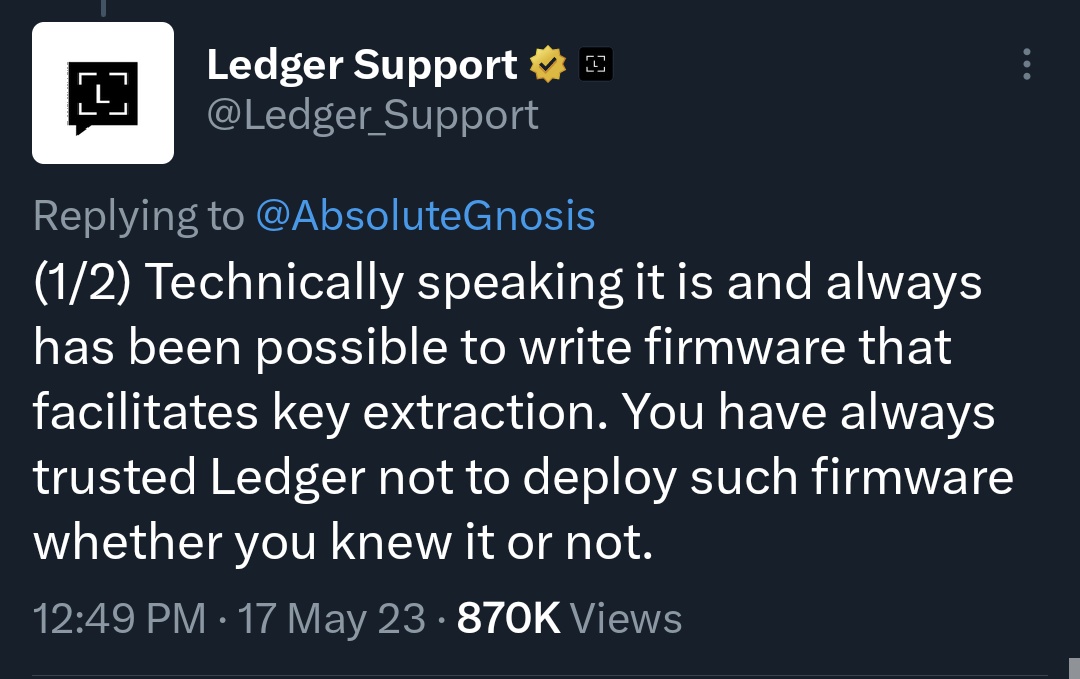
It does bring into perspective the fact that whether Ledger is a hardware wallet, or a firmware wallet.With today's technology, most devices are firmware driven with the underlying hardware.
My opinion
This has serioudly affected my trust on Ledger. At no point do I want anyone (i mean anyone) having access to my cryto-assets. There are other hardware wallets worth exploring, and I cannot recommend any at this point (I used to preach Ledger).