Trigger Warning: Explosive and Casualties
Shocking news came out of Lebanon on reports of people experiencing explosion on pager devices simultanously all over the city. The cause seems to be a pager carried out by the person affected which detonated after receiving a message.
 A meme showing a pager being dropped as a bomb
A meme showing a pager being dropped as a bomb
Victimology
Some context into the section. Hezbullah is a political party which governs Lebanon. As such, besides its militant arm, the government sector is also run by Hezbullah. The pagers were purchased for government use and carried by civilians which runs institutions such as schools, hospitals and even media. The attack seems to be more opportunhistic, hitting anyone and everyone who carried the device. The impact seem to be far reaching, affecting people who are not carrying the device (e.g. a car driver who had the pager may have died from the explosion, hitting other people in its way.
@inteldoge reports that over 2800+ injured and at least 8 dead.
Hezbullah had previously warned and banned the use of mobile phone and moved to pagers. Pagers are receive only device with minimal footprint, and detection is difficult.
The pagers that exploded in Lebanon were not solely used by resistance fighters; employees of Hezbollah's institutions, which include civilians, also used them. It's important to note that Hezbollah is a political party (part of the Lebanese government) and it operates various civilian institutions, such as schools, hospitals, and media outlets. Consequently, this attack did not target soldiers exclusively, but civilians as well. Moreover, there are reports that some individuals purchased and used these pagers from the market, further highlighting that this was an indiscriminate attack, not limited to military personnel.
At 3:30PM earlier today, the Pagers received a message that appeared to be coming from Senior Hezbollah Leadership, which then activated the explosive within the Device; with the pagers being programmed to “Beep” several times before exploding near the head or abdomen of the Victim; with the explosion believed now to have originated from within the Lithium Battery of the Pager.
One of the noted persons who seems to have been injured in this mass scale attack was Mojtaba Amani, the Iranian ambassador Lebanon. Questions raised as to why the ambassador carrying a pager supplied by the Hezbullah.

Supply Chain compromise
The device manufacturer is a company named Gold Apollo who is from Taiwan. According to an update from the company, Gold Apollo has stated that the production the of 5,000 Pagers that were imported to Lebanon and eventually provided to Hezbollah, mainly the AP924 model pager, were subcontracted to a company in Europe.
The complexity of this attack starts from the point of supply chain compromise. The devices, before landing in the hands of Hezbullah, have been tampered extensively. Upon modification, the device then is handed over and carried by the victims, while its normal operations as a pager is not affected.
Device Analysis
Manufacturer
The pager device in question is manufactured by Apollo from Taiwan.

Explosive
The hiss and burning of li-ion produce a hot fire and lots of smoke. Videos available show concussion and little smoke.
Checking with ChatGPT reveals that the energy density of a lithium-ion battery is 0.54-0.9 MJ/kg. C4 is ~4.184 MJ/kg, which gives rise to the conclusion that it's most likely an explosive.
 Sample explosion due to the pager
Sample explosion due to the pager
This further leads to a potential theory that the actual explosive deployed is most likely PETN (Pentaerythritol Tetranitrate). Alternative theory suggests C4, which is more stable. Until a device is found intact, conclusive evidence is still lacking.

According to Sky News Arabia; Mossad was able to inject a compound of Pentaerythritol Tetranitrate (PETN) into the batteries of the pagers that Hezbollah began using around February, before they even arrived in the hands of Hezbollah recipients, allowing them to remotely overheat and detonate the Lithium Battery within the Device.
PETN needs a trigger to cause an explosion, which most lilely acts as a secondary explosive. The initial trigger point creates sufficient amount of force to cascase down to the secondary explosive which causes the actual damage.
Firmware
In this particular incident, a message originating from Hezbullah to a particular group of pagers was the trigger point. At this juncture, its difficult to say if it only affected a subset of device holders, as there may be same device that is not part of the Hebullah procurement that may be effected.
Let's assume that it is a message, to a group of pagers associated with Hezbullah, matching the procurement and distribution of that particular device.

This raises the question, if the pager network has been compromised. Another potential source of attack was revealed to be the USAF EC-130H Compass Call flight. The EC-130H is carrying equipments that can hack wireless devices/networks.
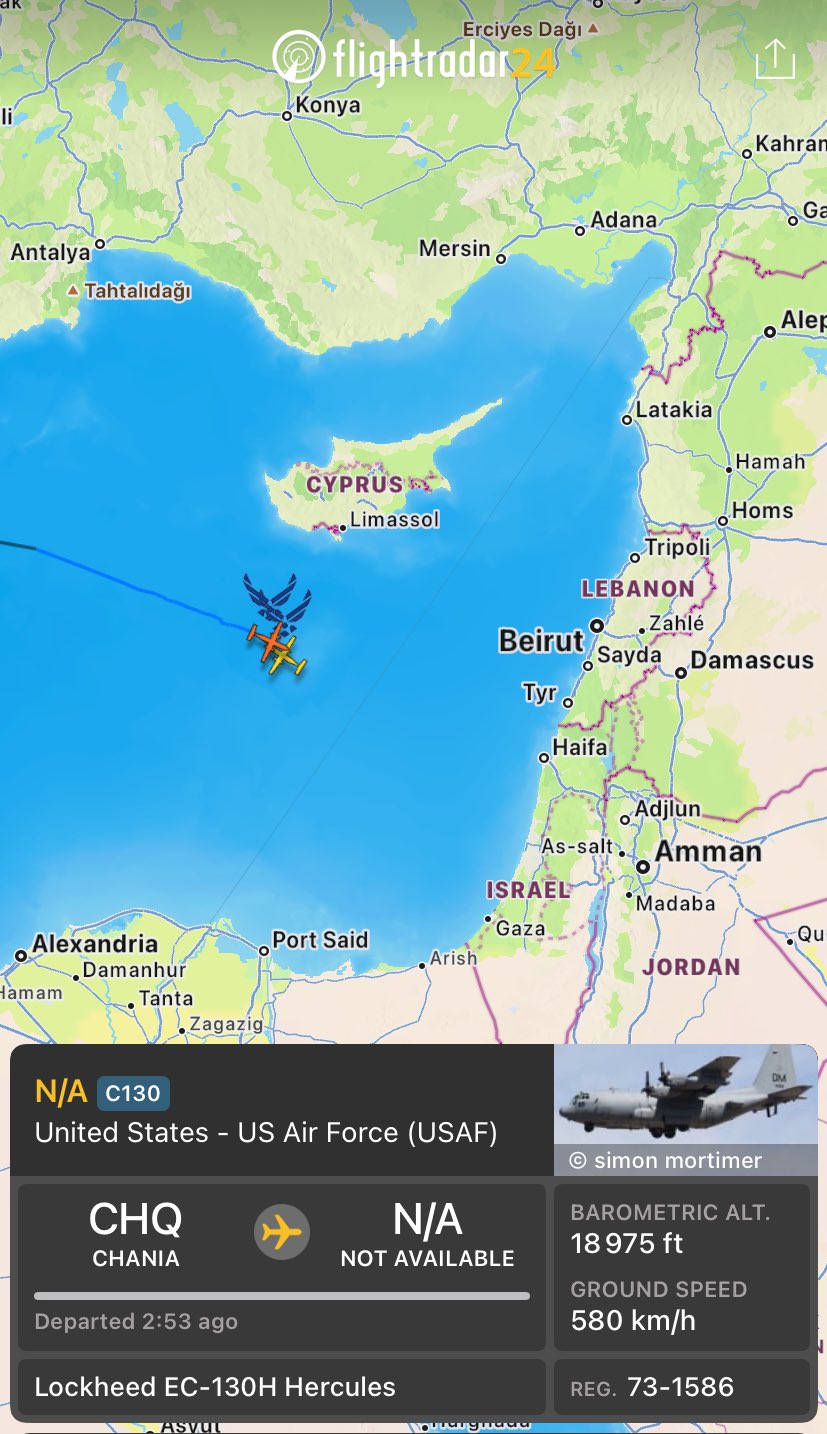
EC-130H was spotted active near eastern Mediterranean seas.
Perpetrators
Interestingly the following news was buried within the feeds.
Israel's Shin Bet is said to have thwarted a Hezbollah assassination attempt on the former IDF Chief of Staff, Aviv Kohavi, which was reported hours before the pager explosion attack happened.
Hezbullah also reported to have hacked into Israeli drones and was able to capture images of Israeli forces.
Warfare and mundane life impact
If pagers can be affected, can it spill over to mobile phones? The unfortunate answer is YES. The risks associated to mobile phones are much higher, as they store a bigger battery. Do remember that mobile phones also carry GPS capabilities and the baseband firmware is often closed source, which enables undocumented capabilties being performed while the user isn't aware. Similar to a malware that creates a layer of screen to prevent users from identifying potential warning boxes from being displayed.
Prevention, if possible?
The supply chain attack isn't new. Cisco had incidents where shipments of their networking gear was intercepted and fitted with malware and compromised firnware to create persistent backdoor access into the gear.
To avoid such issues, a 2 step approach needs to be taken.
First, hardware validation. A complete hardware diagnostics needs to be done to ensure that the hardware inside the device is not compromised. This includes being able to measure capacity and sanctity of components in the device.
Secondly, firmware are to be validated and loaded into the device after hardware validation is complete. This ensures that software is based on a verified version and subsequent software updates are cryptographically signed.
What's next?
We foresee that the attack vector and sophistication will continue to increase. Like Tom and Jerry, the chase continues, and modern life presents with even higher risk of modern problems.
This interestingly opens up new opportunities to create a robust control of what devices can, and cannot do, using manual intervention to enable or disable capabilities.
References
[1] https://en.wikipedia.org/wiki/Detonation [2] https://osmre.gov/sites/default/files/inline-files/Module1.pdf [3] https://en.wikipedia.org/wiki/Explosive [4] https://patents.google.com/patent/US20120210898A1/en [5] https://cdc.gov/niosh/mining%5C/UserFiles/works/pdfs/madea.pdf [6] https://nnss.gov/mission/sdrd/homogenous-detonation-of-high-explosive-by-high-intensity-non-coherent-radiation/ [7] https://en.wikipedia.org/wiki/Pentaerythritol_tetranitrate [8] X - coolierewind, inteldoge [9] https://breakingdefense.com/2015/09/wireless-hacking-in-flight-air-force-demos-cyber-ec-130/