Based on the description from Google, Dragos is the Industrial Cybersecurity expert on a relentless mission to safeguard civilization. In a world of rising cybersecurity threats, Dragos protects the most critical infrastructure — those that provide us with the tenets of modern civilization — from increasingly capable adversaries who wish to do it harm. They specialise in ICS/IOT security.
I am particularly familiar with Dragos because of Robert M Lee who had been teaching SANS classes.
So what happened?
According to Dragos, on May 8 2023, a known cyber criminal group attempted and failed at an extortion scheme against Dragos. Dragos confirmed that their systems are intact, and nothing was breached.
How did this group gain access, you ask? They compromised the personal email address of a soon-to-be sales employee, even before the poor soul started their first day at work! Talk about a bad start, eh?
Interesting point - how do we safeguard ourselves against new employee? More to that later.
But these crafty criminals didn't stop there; they used this personal information to impersonate the new recruit and got through the initial steps of the employee onboarding process.
With this impersonation, they managed to access resources usually used by a new sales employee. This includes systems like SharePoint and the Dragos contract management system. There was one instance when they managed to get their hands on a report with IP addresses associated with one of Dragos customers.
Luckily Dragos, like most properly setup organization had deployed SIEM which allows them to triage and investigate the issue. Using the information available, they proceeded to block the attack, and had engaged Crowdstrike and their Monitoring, Detection and Response (MDR) vendor.
It seems that the motive of the attackers were to launch a ransomware and eventually hold Dragos ransom for their information and infrastructure. Dragos confirmed that there were no lateral movement, privilege escalation nor any persistent access.
Rob M Lee clarified a few issues with the new staff. It was confirmed that the new staff's personal account was compromised prior to the attack towards Dragos. As part of staff onboarding, the multi factor authentication information as sent to the personal email. This gave the attackers access to the contract management and the sales sharepoint system. He confirmed that Dragos does not practice victim blaming.
Timeline
Honestly I am impressed (and this shouldn't be the case, knowing that the organization is choke full of cybersecurity experts).
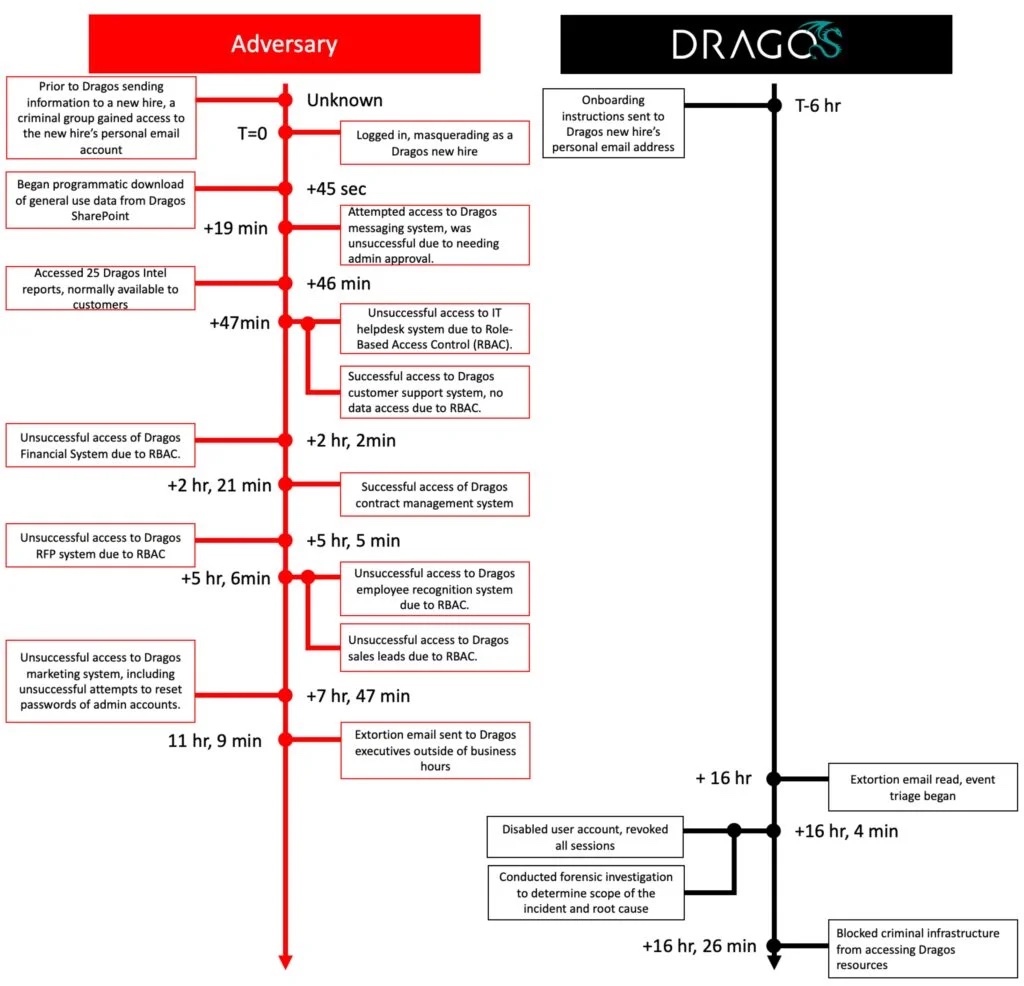
The cyber criminal group was earlier identified to deploy ransomware as per their TTP. However, seeing that they are unable to do so, they changed their tactics into extortion to disclose the breach.
They seem to have contacted Dragos management and attempted to strike a deal. For a start, that went to deaf ears.
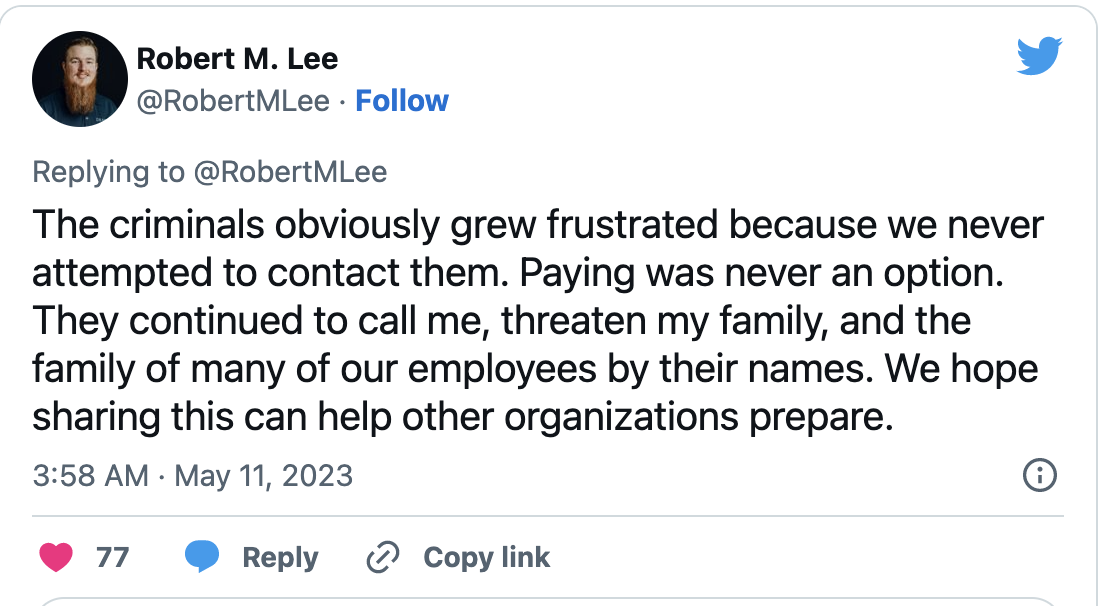
That pissed them off. The attackers then went to harass the common contacts and even family members! Wow, talk about desperation! To this, it was also dealt with a stone wall!
Then they went to publicly known Dragos contact to attempt to get attention to the matter.
While the attacker was focused on Dragos, it also shows that they used OSINT to get further information about the circle around Dragos in an attempt to get someone to buckle. However, they stretched the truth and got debunked for using fake email addresses.
Dragos maintained their stance to not engage with the attackers. They have taken the stance with the clear understanding that information is indeed lost and will surface on public domain at any time. I will put my assessment later on.
IOC involved
IP Addresses
- 144[.]202[.]42[.]216
- 162[.]33[.]179[.]126
The IPs seem to have been associated to Qakbot C2 and Black Basta. Chris Duggan used the reported IP and found more interesting information.
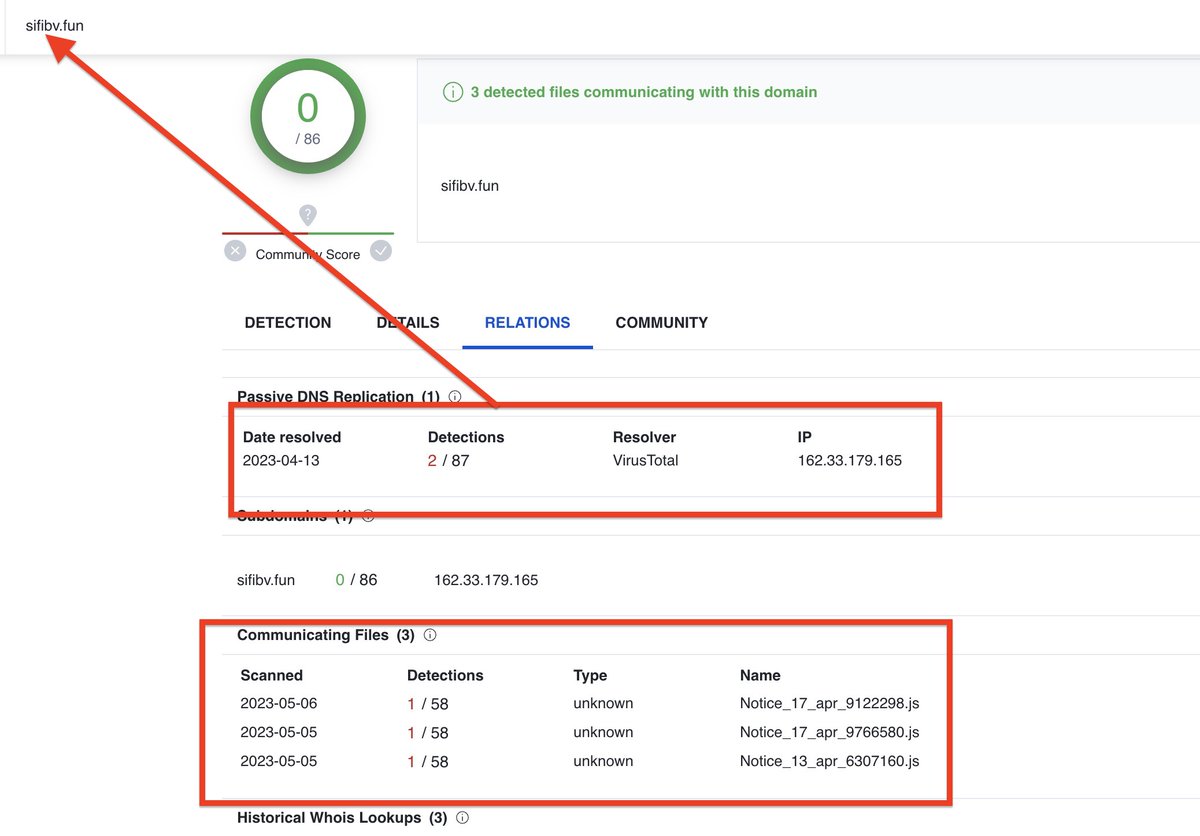
However that's not definitive as Will Thomas from Equinix mentioned that the IP had been used by multiple ransoware group, going from Conti, ViceSociety, BlackCat, Quantum to Zeppelin and Play.
What worked for Dragos?
Dragos identified that their onboarding process needs to be further hardened. I am genuinely interested on what other nechanism that they might put in place. Most likely a wall garden approach until staff is fully onboarded.
Dragos had extensively used multi-step access approval. This means that any access is approved at multiple levels to ensure that no one gets access willy-nilly. Prudent, but effective.
They had ample system log and SIEM properly configured.
Key Recommendation
- Harden Identity & Access Management infrastructure and processes
- Implement separation of duties across the enterprise
- Apply the principle of least privilege to all systems and services
- Implement multi-factor authentication everywhere feasible
- Apply explicit blocks for known bad IP addresses (like those shown above)
- Scrutinize incoming emails for typical phishing triggers, including the email address, URL, and spelling
- Ensure continuous security monitoring is in place, with tested incident response playbooks
My assessment
This would have been a nightmare for any other organization, but not Dragos. They have highly skilled cybersecurity personnel and it's evident that they practice what they preach.
Sad to say, I have encountered MANY and some are even well established organization that sells cyber security, who doesn't practice it.
I recall talking to one organization who wants to sell to us a security solution, who had been a long standing vendor. We turned then down for a new project because they wouldn't even issue a patch for an existing system. How to trust?
Dragos had gone head on with the attacker. Best way to thwart and extortionist is to go public. They lose the leverage they had on you. To me, Dragos had redeemed themselves, but have some work to do. It shows, even after incidents of Solarwinds, that cybersecurity vendors are equally, if not more, exposed to attackers.
To those having cybersecurity as your business, are you YOURSELF well protected? Are you practicing what you preach, or simply selling something to others but doesn't apply to you?
Dragos demonstrated that by doing things difficult like multi-step access approval, work can still be done and data security maintained. Is efficiency that much gain if you end up in a breach? Business, especially Board needs to debate on this.
Would things have gone different if the breach was much more catastrophic? Maybe. Dragos maintained that they will not engage nor pay ransom at any point. It's a hard stance to take, a lot of organization will buckle under the pressure. I can at this point only speculate what may happen as the path now differs.
Reference
[1] https://www.dragos.com/blog/deconstructing-a-cybersecurity-event/
[2] Gatlan, S. (2023). Cybersecurity firm Dragos discloses cybersecurity incident, extortion attempt. Retrieved 16 May 2023, from https://www.bleepingcomputer.com/news/security/cybersecurity-firm-dragos-discloses-cybersecurity-incident-extortion-attempt/