I didn't have any thoughts to write a part 2, but recent development warrants a follow up on this matter.
Further deep dive on the zero day
Huntress Lab, published by John Hammond did an excellent job dissecting the bug.
Huntress has fully recreated the attack chain exploiting MOVEit Transfer software. Huntress Lab were the only party able to do this.
Huntress Lab have uncovered that the initial phase of the attack, SQL injection, opens the door for even further compromise -- specifically, arbitrary code execution.
Any unauthenticated threat actor can trigger the exploit that instantly deploys the ransomware or perform any other malicious activity. The malicious code that runs under the MOVEit service using the user account moveitsvc (part of local administrators group). Further action on target would include disabling AV/EDR services or run malicious code.
It has been confirmed that a webshell named "human2.aspx" has been added to compromised system. The file may be renamed to avoid file name based detection. The webshell serves as a backdoor and means for persistence. Again, the filename isn't cast in stone and is quite trivial to be renamed.
Based on Huntress Lab research, it is confirmed that the patch is effective against this attack. Logging is also important to identify activities performed.
2023-05-30 17:05:50 192.168.###.### GET / - 443 - 5.252.190.181 user-agent - 200
2023-05-30 17:06:00 192.168.###.### POST /guestaccess.aspx - 443 - 5.252.191.14 user-agent - 200
2023-05-30 17:06:00 192.168.###.### POST /api/v1/token - 443 - 5.252.191.14 user-agent - 200
2023-05-30 17:06:02 192.168.###.### GET /api/v1/folders - 443 - 5.252.191.14 user-agent - 200
2023-05-30 17:06:02 192.168.###.### POST /api/v1/folders/605824912/files uploadType=resumable 443 - 5.252.191.14 user-agent - 200
2023-05-30 17:06:02 ::1 POST /machine2.aspx - 80 - ::1 CWinInetHTTPClient - 200
2023-05-30 17:06:02 192.168.###.### POST /moveitisapi/moveitisapi.dll action=m2 443 - 5.252.191.14 user-agent - 200
2023-05-30 17:06:04 192.168.###.### POST /guestaccess.aspx - 443 - 5.252.190.233 user-agent - 200
2023-05-30 17:06:08 192.168.###.### PUT /api/v1/folders/605824912/files uploadType=resumable&fileId=963061209 443 - 5.252.190.233 user-agent - 500
2023-05-30 17:06:08 ::1 POST /machine2.aspx - 80 - ::1 CWinInetHTTPClient - 200
2023-05-30 17:06:08 192.168.###.### POST /moveitisapi/moveitisapi.dll action=m2 443 - 5.252.190.233 user-agent - 200
2023-05-30 17:06:11 192.168.###.### POST /guestaccess.aspx - 443 - 5.252.190.116 user-agent - 200
2023-05-30 17:06:21 192.168.###.### GET /human2.aspx - 443 - 5.252.191.88 user-agent - 404
The log above was observed on the process of exploitation using this zero day.
@BushidoToken from Equinix Threat Analysis Center had published a Maltego diagram on this attack methodology.
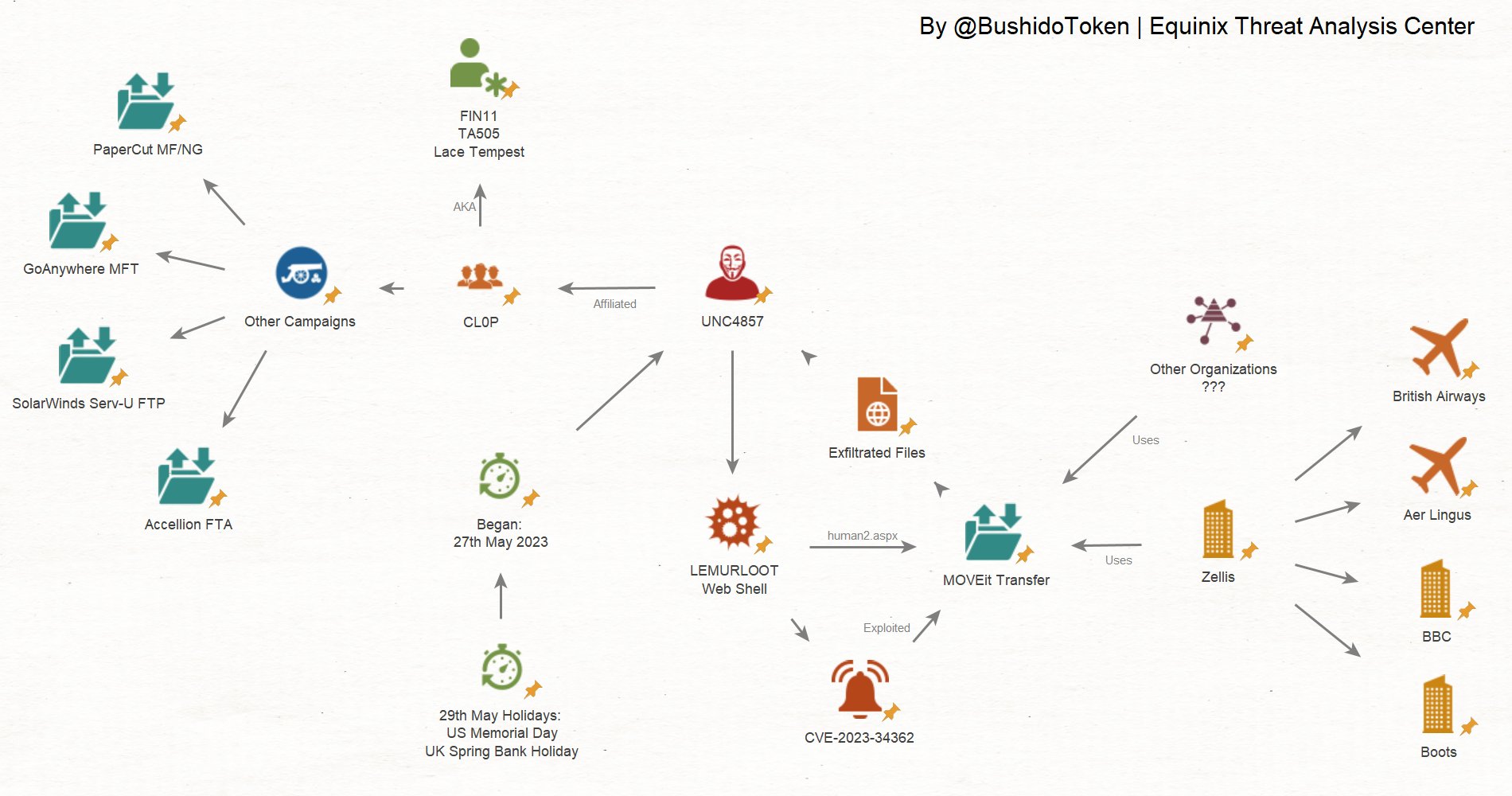
Attacker's Den
Cl0p confirmed the attribution made by Microsoft, which was confirmed by BleedingComputer. Cl0p ransomware group operates in Tor network. Cl0p was identified as a Russian speaking group by Microsoft.
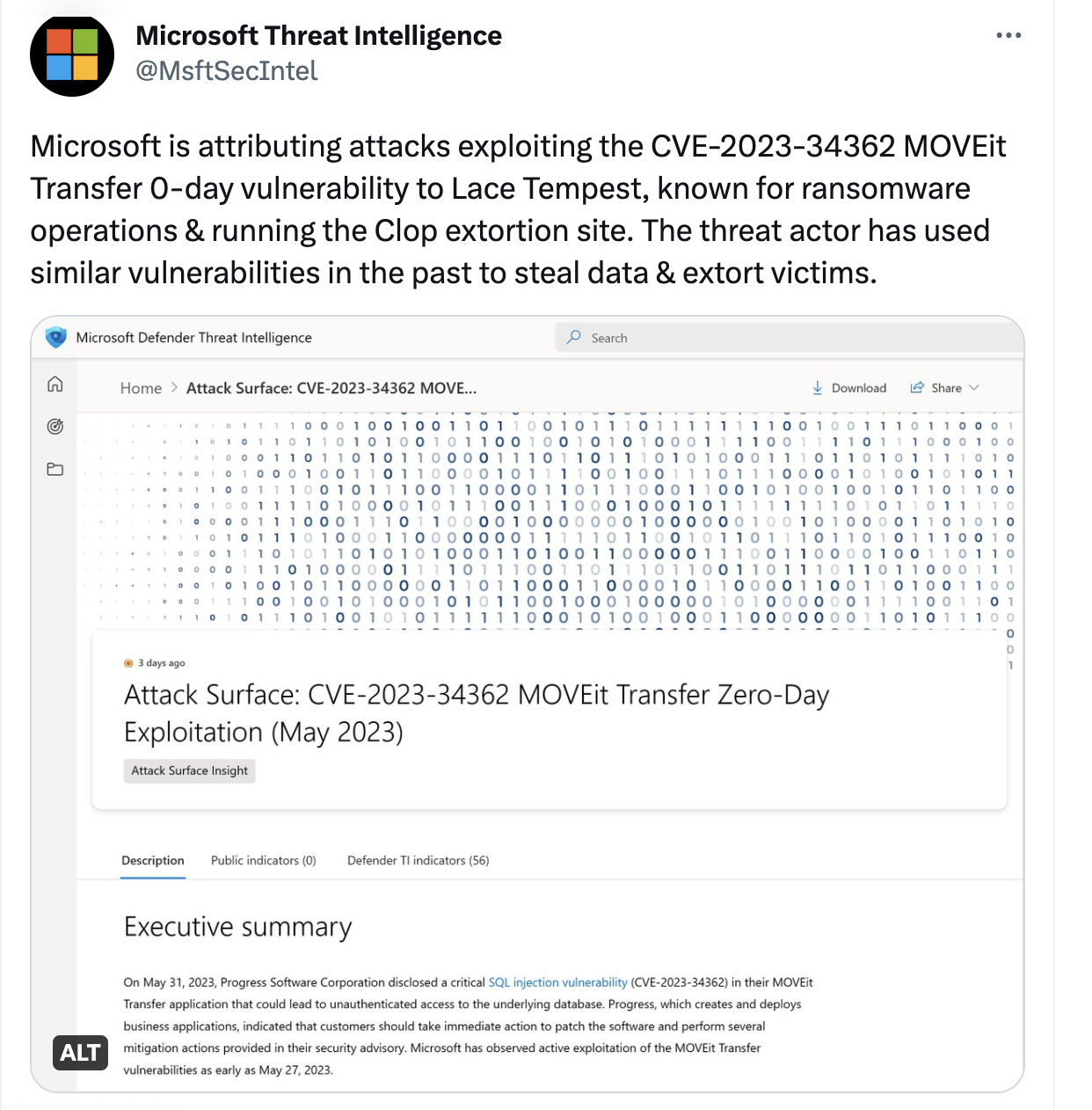
Cl0p ransomware has claimed responsibility for the MOVEit zero day vulnerability and has confirmed that the victims will be contacted in due time, and they were professional enough to publish whats expected.
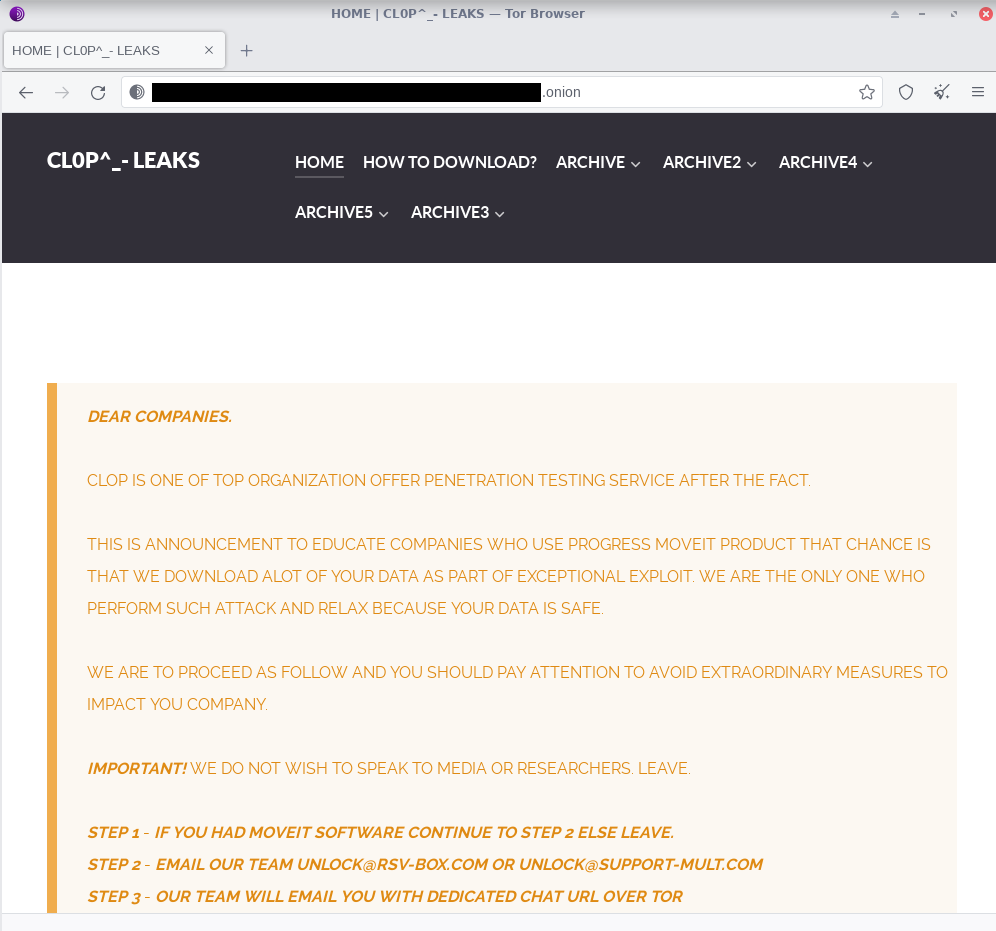
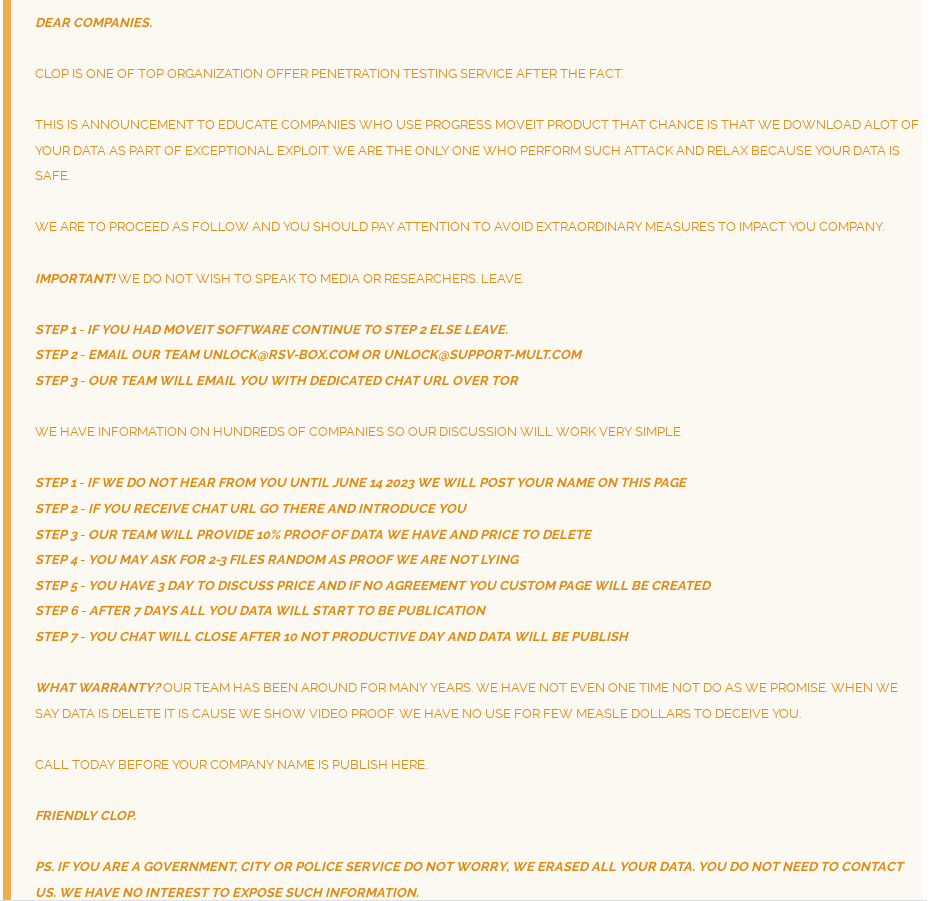
Due to the slow connection in Tor (32kb/s) coupled with dozens of zip files averaging 100GB++ in size, its impossible to download the leaked files within reasonable time. Question remains whether the hassle is worth the effort to download the leaked files, given the challenges above.
Quotable quote from the TA
"WE DO NOT WISH TO SPEAK TO MEDIA OR RESEARCHERS.
IF YOU HAD MOVEIT SOFTWARE EMAIL OUR TEAM UNLOCK[@]RSV-BOX[.]COM OR UNLOCK[@]SUPPORT-MULT[.]COM
OUR TEAM WILL EMAIL YOU WITH DEDICATED CHAT URL OVER TOR"
Victimology
The first companies that had announced being part of the breach was British Airways, BBC and Boots.
BA told Sky News: "We have been informed that we are one of the companies impacted by Zellis's cybersecurity incident which occurred via one of their third-party suppliers called MOVEit.
Reference
[1] Hammond, J. (2023). MOVEit Transfer Critical Vulnerability CVE-2023-34362 Rapid Response. Retrieved 7 June 2023, from https://www.huntress.com/blog/moveit-transfer-critical-vulnerability-rapid-response?utm_content=251219326&utm_medium=social&utm_source=linkedin&hss_channel=lcp-10172550
[2] Abrams, L. (2023). Clop ransomware claims responsibility for MOVEit extortion attacks. Retrieved 7 June 2023, from https://www.bleepingcomputer.com/news/security/clop-ransomware-claims-responsibility-for-moveit-extortion-attacks/
[3] BA, BBC and Boots hit by cyber security breach with contact and bank details exposed. (2023). Retrieved 7 June 2023, from https://news.sky.com/story/bas-uk-staff-exposed-to-global-data-theft-spree-12896900