MSI (Micro-Star International) is a well known hardware manufacturer. In the region that I'm in, its known as the "student's computer", due to its cost effective solutions with decent reliability. This article looks into recent news about breach that affected MSI and how the Intel Boot Guard is affected.
What is Intel BootGuard?
Intel Boot Guard is a security technology developed by Intel to protect the boot process of a computer system from unauthorized tampering and malware attacks. It is designed to ensure the integrity of the system's firmware, including the Unified Extensible Firmware Interface (UEFI) firmware and the boot loader. Boot Guard aims to prevent unauthorized firmware modification, such as the insertion of malicious code or unauthorized firmware updates, which could compromise the security and stability of the system.
Here's a detailed explanation of how Intel Boot Guard works:
- Verified Boot Process: Boot Guard operates during the early stages of the boot process, starting from the moment power is applied to the system. It ensures the integrity of the firmware and the boot loader before transferring control to the operating system. This process relies on digital signatures and platform configuration registers (PCRs) to establish a chain of trust. The diagram below gives you a clearer picture.
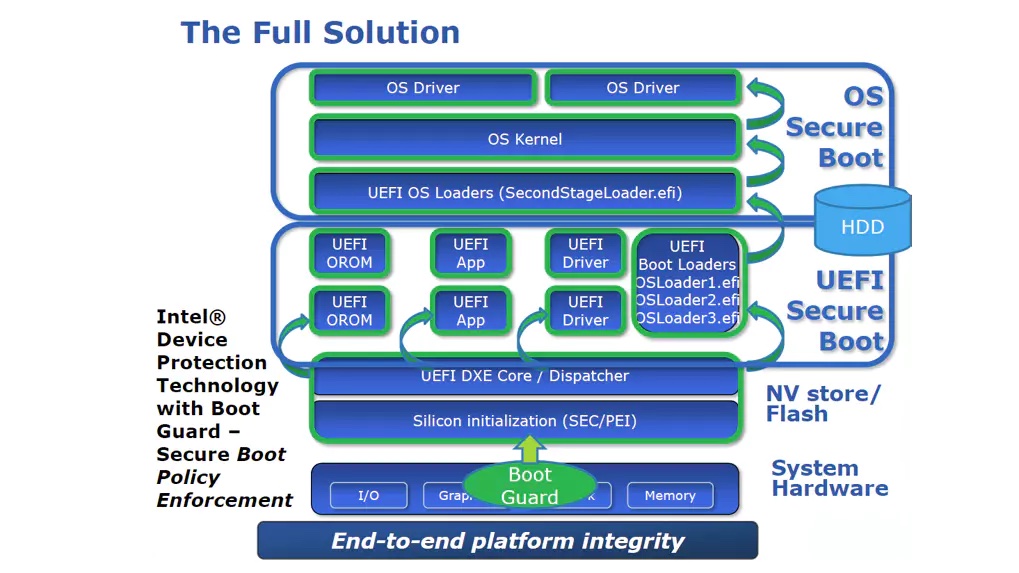
- Boot Guard Capable Platform: A system needs to have Boot Guard capabilities built into its hardware to utilize this technology. This includes a Boot Guard capable processor and chipset. When the system starts, the processor verifies the integrity of the platform firmware using a series of measurements and comparisons.
- Boot Guard Measurements: The firmware of a Boot Guard-capable system is divided into multiple regions, including the firmware volume, boot loader, and firmware configuration settings. Each region is measured using a cryptographic hash function (such as SHA-256) to generate a unique hash value called a measurement.
- Boot Guard Verified Launch: The processor compares the measurements obtained during the boot process with a set of pre-calculated expected values stored in the chipset. These expected values are securely fused into the chipset during the manufacturing process and cannot be altered. If the measurements match the expected values, the boot process continues; otherwise, an error is triggered, indicating that the firmware has been tampered with.
- Secure Boot and Trusted Platform Module (TPM): Boot Guard is often used in conjunction with other security features, such as Secure Boot and a TPM. Secure Boot ensures that only digitally signed bootloaders and operating systems are allowed to execute, preventing the loading of unauthorized or malicious code. The TPM provides additional hardware-based security by securely storing cryptographic keys and measurements, which further strengthens the chain of trust.
- Customization and Manufacturing: Boot Guard allows system manufacturers to customize the platform-specific configuration. They can specify their own policies, such as which firmware updates are allowed, to enhance security and prevent unauthorized modifications. These policies are stored in the platform-specific Boot Guard policy register (BGUP).
- Enhanced Platform Trust Technology (EPTT): Boot Guard is part of Intel's Enhanced Platform Trust Technology, which includes other security features like Intel Trusted Execution Technology (TXT) and Intel Software Guard Extensions (SGX). EPTT provides a comprehensive set of hardware-based security features to protect the entire computing platform.
About the hack
Intel Boot Guard was not well documented. Researchers from Binarly in Black Hat 2017 had identified and shared details about this feature.
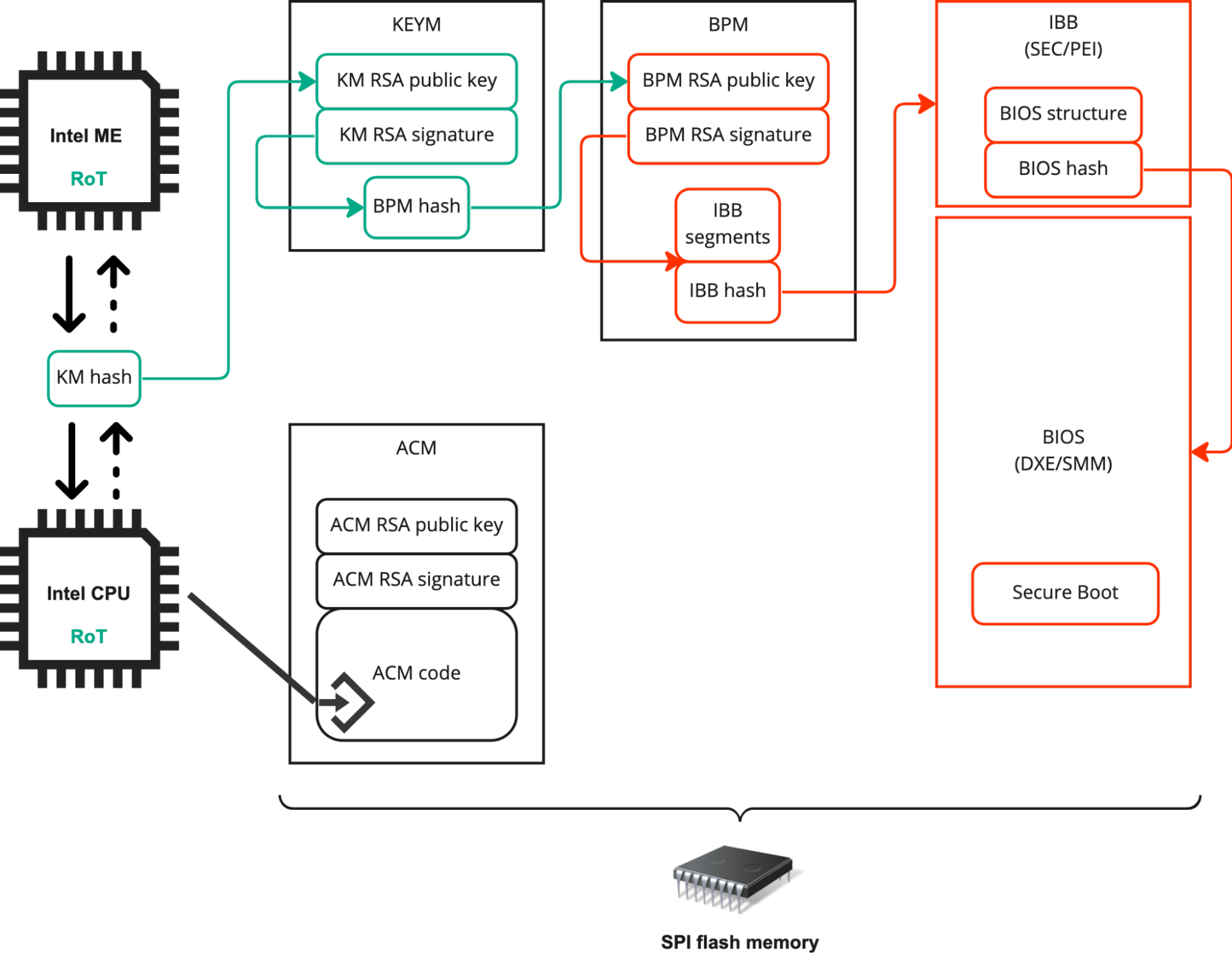
Intel Boot Guard is a hardware-based technology intended to protect PCs against executing non-genuine UEFI Firmware, which could happen in case a possible attacker has bypassed protection against modification of BIOS.
Boot Guard started off with a key sise of 2048, but from Boot Guard 2.0 the key size has been increased to 3072.
This issue started off with MSI had a data breach and the ransomware gang had asked for USD4million. The attackers proceeded to leak information about firmware source code for the motherboard.
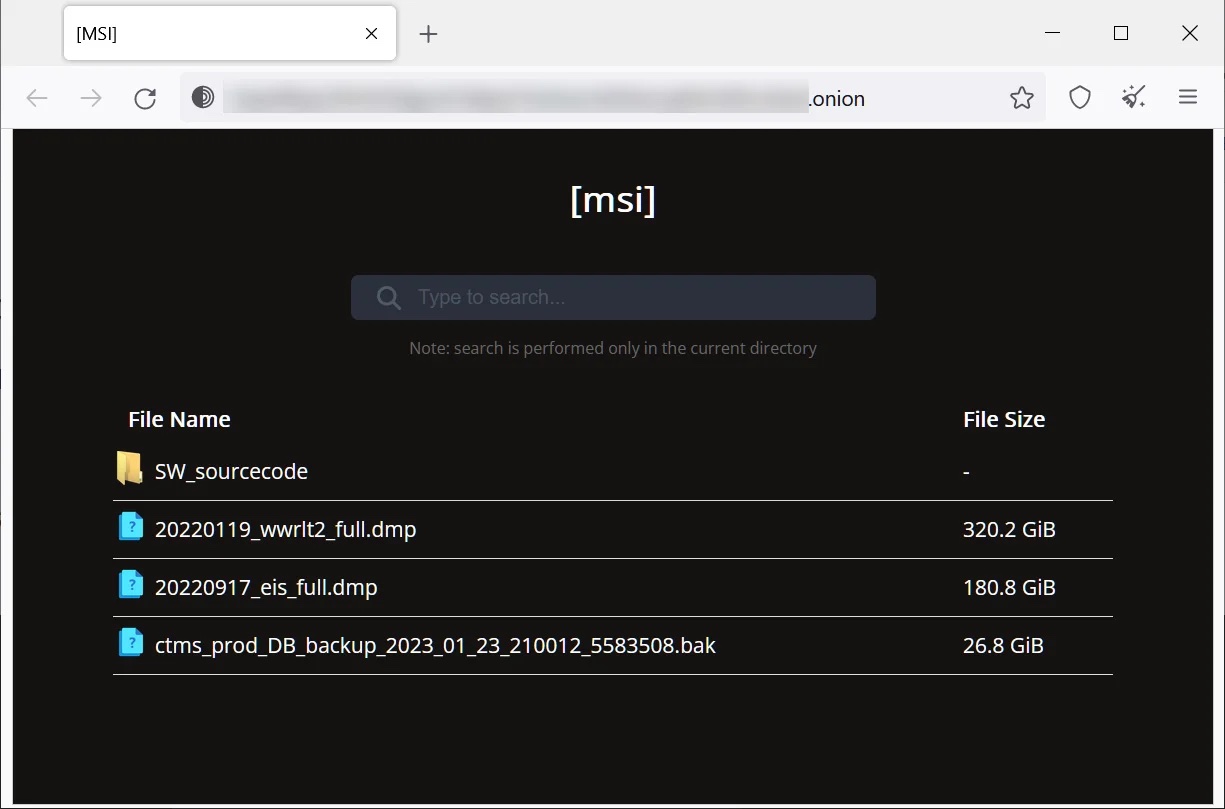
Alex Matrosov, the CEO of firmware supply chain security platform Binarly, warned that the leaked source code contains the image signing private keys for 57 MSI products and Intel Boot Guard private keys for 116 MSI products.
The leak affects 11th/12th/13th gen Intel chipsets. Note worthy point is that Intel Signing keys were not affected, only the system manufacturer keys that were leaked.
Based on this, it can be concluded that Intel "The signing keys for firmware image allows the attacker to craft malicious firmware updates and it can be delivered through a normal bios update process with MSI update tools."
The leak has far reaching impact as the Intel Boot Guard key leak impacts not just MSI but the whole ecosystem which renders the security feature useless.
Intel Boot Guard is a security feature built into modern Intel hardware designed to prevent the loading of malicious firmware, known as UEFI bootkits. It is a critical feature used to meet Windows UEFI Secure Boot requirements.
This is because malicious firmware loads before the operating system, allowing it to hide its activities from the kernel and security software, persist even after an operating system is reinstalled, and help install malware on compromised devices.
Malicious firmware will load before the operating system (I call it Ring -1). Operating system only loads after that, so any kernel/security function is rendered useless and malware becomes persistent even after the operating system is reinstalled.
To prevent this, Intel Boot Guard will verify if a firmware image is signed using a legitimate private signing key using an embedded public key built into the Intel hardware.
If the firmware can be verified as legitimately signed, Intel Boot Guard will allow it to be loaded on the device. However, if the signature fails, the firmware will not be allowed to load.
Moving forward
This leak is very costly for MSI, even though the news was downplayed. Looking at this list provided by Binarly[4], it affects quite a number of hardware. These hardware is now susceptible to a firmware level attack, which is the wet dream of attackers due to its persistent nature.
Hardware/OEM manufacturers are critical part of computing supply chain. Would anyone now trust MSI, that this incident has occured that the company has been silent about? Has the company reached out to it's customers and informed them on next steps? Hardware level attacks will become more and more prevalent due to its complexity and that there is no "EDR" for hardware (no I am NOT implying a new business case here).
Reference:
[1] Leaked Intel Boot Guard keys:What happened? How does it affect the software supply chain?. (2022). Retrieved 18 May 2023, from https://binarly.io/posts/Leaked_Intel_Boot_Guard_keys_What_happened_How_does_it_affect_the_software_supply_chain/index.html
[2] Toulas, B. (2023). Money Message ransomware gang claims MSI breach, demands $4 million. Retrieved 18 May 2023, from https://www.bleepingcomputer.com/news/security/money-message-ransomware-gang-claims-msi-breach-demands-4-million/
[3] Abrams, L. (2023). Intel investigating leak of Intel Boot Guard private keys after MSI breach. Retrieved 18 May 2023, from https://www.bleepingcomputer.com/news/security/intel-investigating-leak-of-intel-boot-guard-private-keys-after-msi-breach/
[4] binarly-io. (2023). SupplyChainAttacks/MsiImpactedDevices.md at main · binarly-io/SupplyChainAttacks. Retrieved 18 May 2023, from https://github.com/binarly-io/SupplyChainAttacks/blob/main/MSI/MsiImpactedDevices.md