Barracuda is well known for its security appliances. A zero day vulnerability was discovered (CVE-2023-2868) which was found to be aggresively exploited, with suspected links to China.
Preamble
The zero day was announced by Barracuda on May 23, 2023 which affects the Email Security Gateway (I have used and procured this in the past for previous organizations). The vulnerability was exploited as far back as October 2022 (a good 7 months!). As a result of exploitation the boxes were then used for espionage and a wide range of activities to support People's Republic of China.
Steps of Exploitation
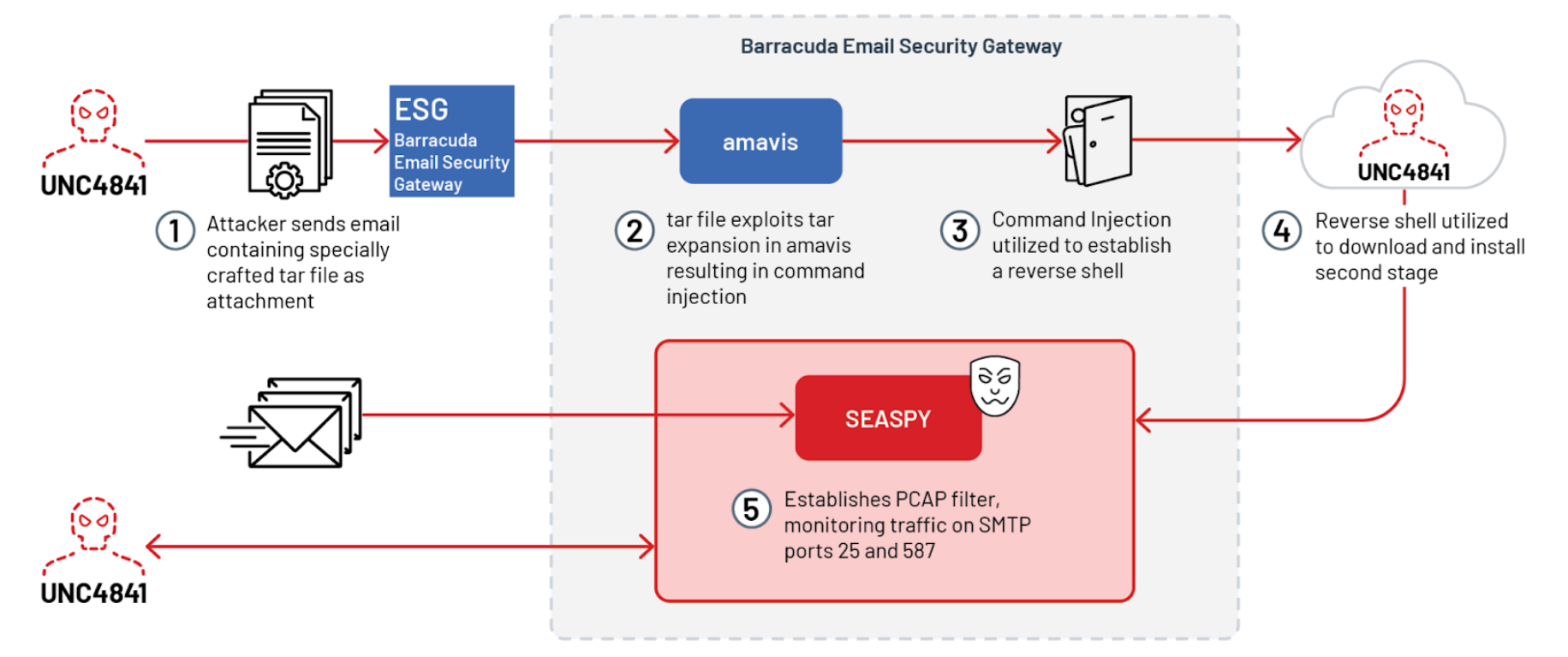
An email is sent to the target organization which uses the Barracuda ESG appliance. The email contained a malicious attachment. The CVE is described as a remote command injection vulnerability which affects screening of email attachments. Specifically, the command injection vulnerability affects TAR files.
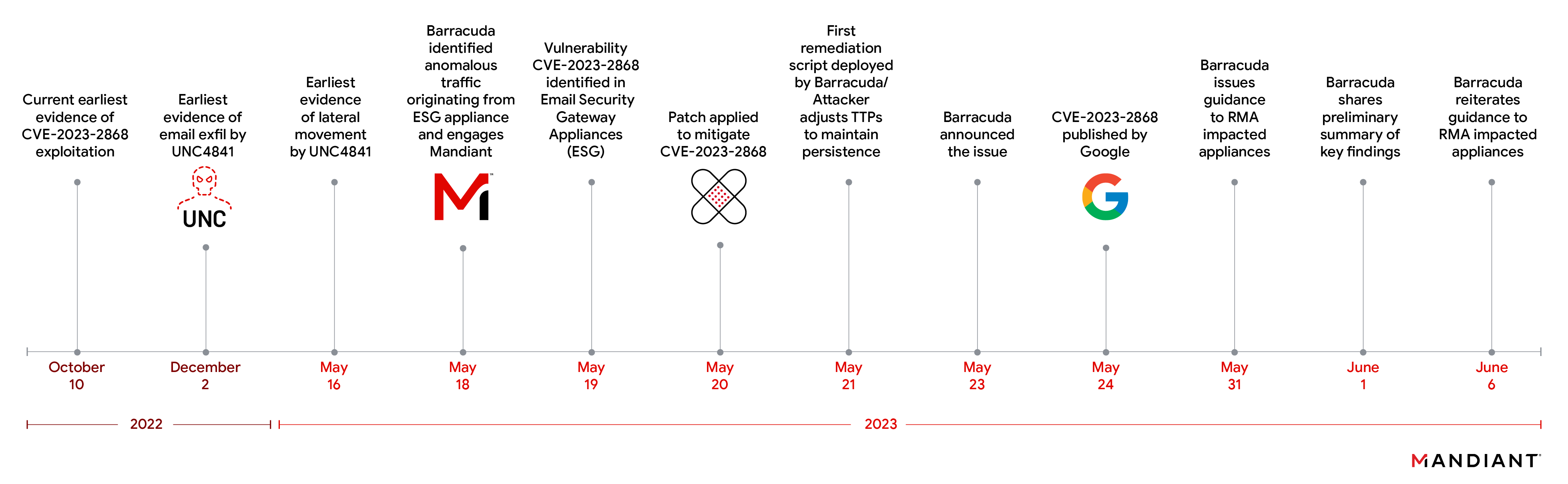
The vulnerability is triggered because there is an unsanitized and unfiltered user-controlled input which is executed using the systems Perl qx() routine. A malicious attachment, which is a TAR file is formatted to trigger the command injection which allows the attacker to remotely execute system commands.
The attacker intentionally makes the email look "spammy" by ensuring poor grammar and with placeholders in order to trigger the anti spam engine. This causes the ESG to perform a full investigation on the attachment, causing the malicious attachment to trigger the remote command injection vulnerability.
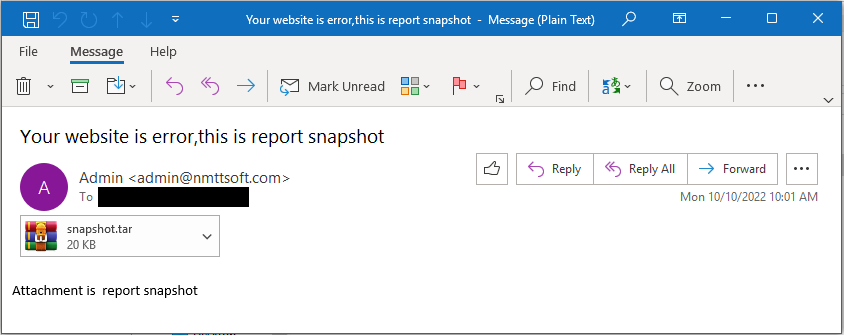
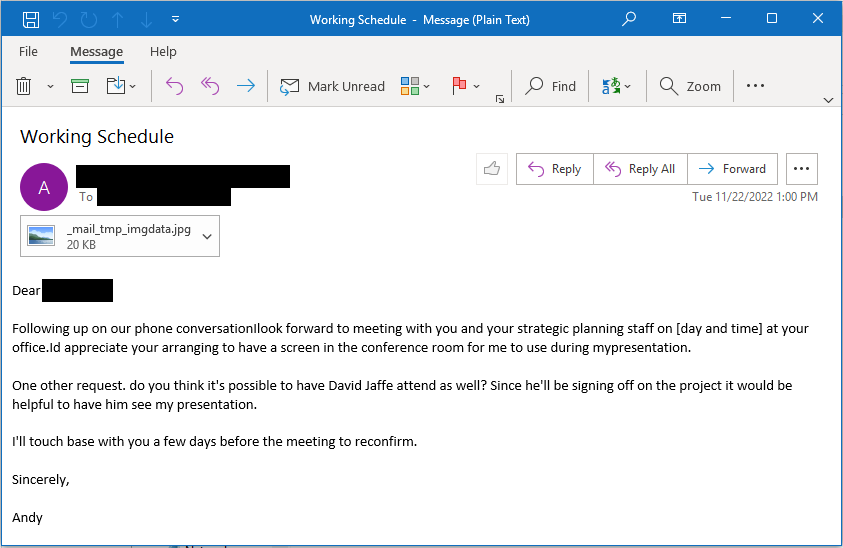
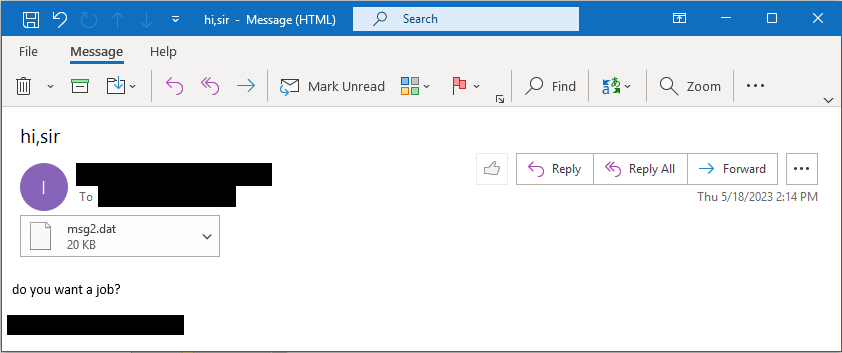
Mandiant also got emails that originated from organizations with vulnerable Barracuda ESG appliances.
To dive further, the threat actor spawned a reverse shell on certain ESG boxes. The paylod is obfuscated, and once reversed shows a call to the shell interpreter.
Using shell, the ayload then creates a temporary directory using mkfifo, uses openssl in ssl client mode to initiate the reverse shell connection.
In some instances the threat actor downloads a backdoor payload within TAR files which executes the SALTWATER payload.
Custom Payloads
There were 3 observed payloads, codenamed SEASPY, SALTWATER and SEASIDE.
SEASPY is the primary backdoor that was deployed, which is a passive backdoor which acts as a PCAP filter listening to a "magic packet".
Interestingly trojanised LUA modules were also deployed, codenamed SEASPRAY AND SKIPJACK. These lua modules are trojanised backdoor to the ESG appliance.
The Threat Actor is also observed to use self signed certificates mimicking Barracuda Network's certificate to mask traffic.
To achieve persistence, the threat actor uses cron. Files in /etc were modified which is responsible for cron execution. At the same time, the threat actor also added a script to /etc/init.d/rc to ensure that the malware starts back if and when the box is rebooted. (No wonder Barracuda had to recall the exploited boxes because the hooks are deep to the system).
IOC
The following IOC was observed with this attack.
- 101.229.146.218
- 103.146.179.101
- 103.27.108.62
- 103.77.192.13
- 103.77.192.88
- 103.93.78.142
- 104.156.229.226
- 104.223.20.222
- 107.148.149.156
- 107.148.219.227
- 107.148.219.53
- 107.148.219.54
- 107.148.219.55
- 107.148.223.196
- 107.173.62.158
- 137.175.19.25
- 137.175.28.251
- 137.175.30.36
- 137.175.30.86
- 137.175.51.147
- 137.175.53.17
- 137.175.53.170
- 137.175.53.218
- 137.175.60.252
- 137.175.60.253
- 137.175.78.66
- 139.84.227.9
- 155.94.160.72
- 182.239.114.135
- 182.239.114.254
- 192.74.226.142
- 192.74.254.229
- 198.2.254.219
- 198.2.254.220
- 198.2.254.221
- 198.2.254.222
- 198.2.254.223
- 199.247.23.80
- 213.156.153.34
- 216.238.112.82
- 23.224.42.29
- 23.224.78.130
- 23.224.78.131
- 23.224.78.132
- 23.224.78.133
- 23.224.78.134
- 37.9.35.217
- 38.54.113.205
- 38.54.1.82 (Kaopo Cloud HK Limited, MALAYSIA)
- 38.60.254.165
- 45.63.76.67
- 52.23.241.105
- 64.176.4.234
- 64.176.7.59
Domains
- bestfindthetruth[.]com
- fessionalwork[.]com
- gesturefavour[.]com
- goldenunder[.]com
- singamofing[.]com
- singnode[.]com
- togetheroffway[.]com
- troublendsef[.]com
Hashes
- 0d67f50a0bf7a3a017784146ac41ada0
- 42722b7d04f58dcb8bd80fe41c7ea09e
- 5392fb400bd671d4b185fb35a9b23fd3
- ac4fb6d0bfc871be6f68bfa647fc0125
- 878cf1de91f3ae543fd290c31adcbda4
- b601fce4181b275954e3f35b18996c92
- 827d507aa3bde0ef903ca5dec60cdec8
- c56d7b86e59c5c737ee7537d7cf13df1
- 6f79ef58b354fd33824c96625590c244
- 349ca242bc6d2652d84146f5f91c3dbb
- 1fea55b7c9d13d822a64b2370d015da7
- 64c690f175a2d2fe38d3d7c0d0ddbb6e
- 4cd0f3219e98ac2e9021b06af70ed643
- 3b93b524db66f8bb3df8279a141734bb
- 8fdf3b7dc6d88594b8b5173c1aa2bc82
- 4ec4ceda84c580054f191caa09916c68
- 1b1830abaf95bd5a44aa3873df901f28
- 4ca4f582418b2cc0626700511a6315c0
- c528b6398c86f8bdcfa3f9de7837ebfe
- 2d841cb153bebcfdee5c54472b017af2
- c979e8651c1f40d685be2f66e8c2c610
- 1c042d39ca093b0e7f1412453b132076
- ba7af4f98d85e5847c08cf6cefdf35dc
- 82eaf69de710abdc5dea7cd5cb56cf04
- e80a85250263d58cc1a1dc39d6cf3942
- 5d6cba7909980a7b424b133fbac634ac
- 1bbb32610599d70397adfdaf56109ff3
- 4b511567cfa8dbaa32e11baf3268f074
- a08a99e5224e1baf569fda816c991045
- 19ebfe05040a8508467f9415c8378f32
- 831d41ba2a0036540536c2f884d089f9
- db4c48921537d67635bb210a9cb5bb52
- 694cdb49879f1321abb4605adf634935
- 5fdee67c82f5480edfa54afc5a9dc834
- 8fc03800c1179a18fbd58d746596fa7d
- 17696a438387248a12cc911fbae8620e
- 4c1c2db989e0e881232c7748593d291e
- 3e3f72f99062255d6320d5e686f0e212
- 7d7fd05b262342a9e8237ce14ec41c3b
- 2e30520f8536a27dd59eabbcb8e3532a
- 0245e7f9105253ecb30de301842e28e4
- 0c227990210e7e9d704c165abd76ebe2
- c7a89a215e74104682880def469d4758
- 1bc5212a856f028747c062b66c3a722a
- a45ca19435c2976a29300128dc410fd4
- 132a342273cd469a34938044e8f62482
- 23f4f604f1a05c4abf2ac02f976b746b
- 45b79949276c9cb9cf5dc72597dc1006
- bef722484288e24258dd33922b1a7148
- 0805b523120cc2da3f71e5606255d29c
- 69ef9a9e8d0506d957248e983d22b0d5
- 3c20617f089fe5cc9ba12c43c6c072f5
- 76811232ede58de2faf6aca8395f8427
- f6857841a255b3b4e4eded7a66438696
- 2ccb9759800154de817bf779a52d48f8
- cd2813f0260d63ad5adf0446253c2172
- 177add288b289d43236d2dba33e65956
- 87847445f9524671022d70f2a812728f
- 35cf6faf442d325961935f660e2ab5a0
- ce67bb99bc1e26f6cb1f968bc1b1ec21
- e4e86c273a2b67a605f5d4686783e0cc
- ad1dc51a66201689d442499f70b78dea
- 9033dc5bac76542b9b752064a56c6ee4
- e52871d82de01b7e7f134c776703f696
- 446f3d71591afa37bbd604e2e400ae8b
- 666da297066a2596cacb13b3da9572bf
- 436587bad5e061a7e594f9971d89c468
- 85c5b6c408e4bdb87da6764a75008adf
- 407738e565b4e9dafb07b782ebcf46b0
- cb0f7f216e8965f40a724bc15db7510b
- 19e373b13297de1783cecf856dc48eb0
Reference
[1] (2023). Retrieved 20 June 2023, from https://www.barracuda.com/company/legal/esg-vulnerability
[2] Barracuda ESG Zero-Day Vulnerability (CVE-2023-2868) Exploited Globally by Aggressive and Skilled Actor, Suspected Links to China | Mandiant. (2023). Retrieved 20 June 2023, from https://www.mandiant.com/resources/blog/barracuda-esg-exploited-globally
[3] Barracuda Networks Releases Update to Address ESG Vulnerability | CISA. (2023). Retrieved 20 June 2023, from https://www.cisa.gov/news-events/alerts/2023/06/15/barracuda-networks-releases-update-address-esg-vulnerability
[4] Barracuda: Replace vulnerable ESG devices 'immediately' | TechTarget. (2023). Retrieved 20 June 2023, from https://www.techtarget.com/searchsecurity/news/366539605/Barracuda-Replace-vulnerable-ESG-devices-immediately