Introduction
In the ever-evolving landscape of cybersecurity, SIEM (Security Information and Event Management) systems are pivotal in safeguarding enterprise networks. Yet, these systems confront a formidable adversary: the cunning evasion tactics of cyber attackers. These strategies are expertly crafted to exploit the inherent limitations and vulnerabilities in SIEM rules, enabling malicious activities to remain undetected. A profound understanding of these evasion techniques is indispensable for reinforcing SIEM defenses and ensuring comprehensive network security.
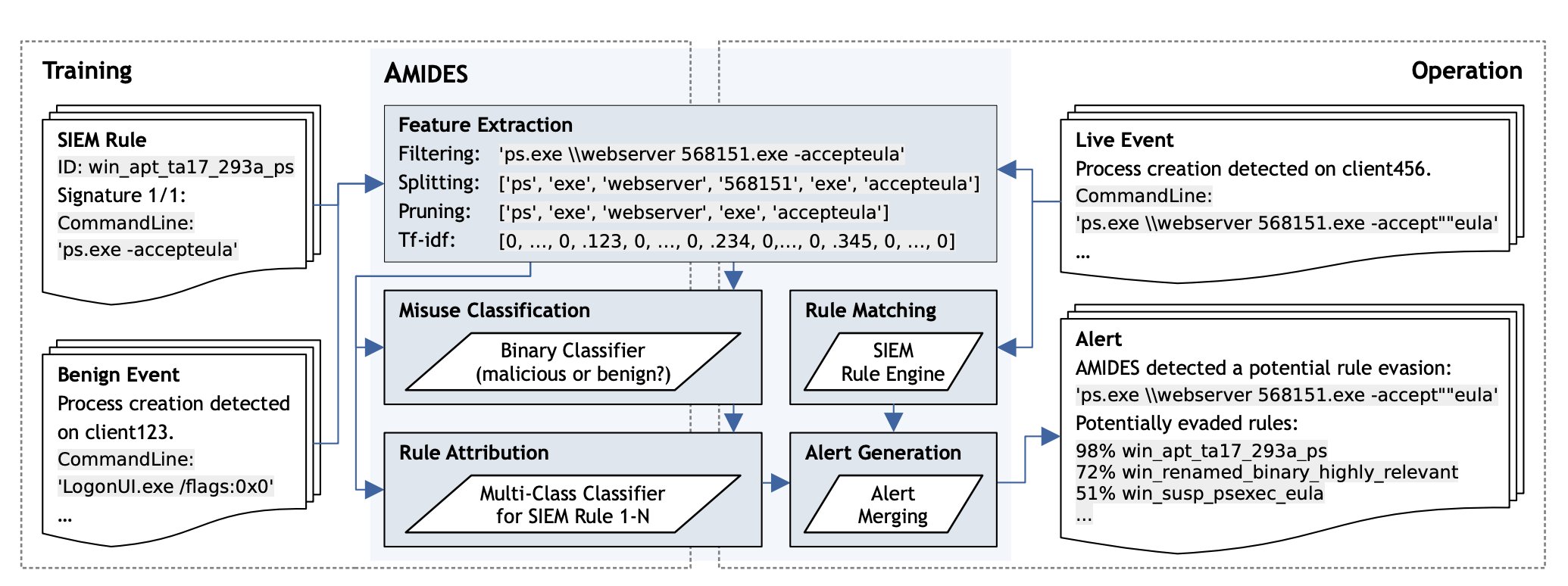
Stealth through Complexity
Attackers employ sophisticated methods to conceal their activities, effectively bypassing SIEM detection. Advanced encryption, for instance, obscures network traffic content, challenging SIEM systems' interpretative capabilities. Polymorphic malware, with its ever-changing code or behavior, further complicates consistent detection. Attackers also utilize sophisticated command and control (C&C) channels that mimic legitimate network traffic, blending malicious activities seamlessly. An example is the use of encrypted tunnels for communication with compromised systems, disguising the traffic as typical encrypted web traffic.
Log Manipulation
Log manipulation is a prevalent evasion tactic. Logs, the vital records of network events, are fundamental to SIEM systems for anomaly detection. By altering or deleting these logs, attackers effectively erase their digital footprints, rendering themselves invisible to the SIEM system. This tactic not only impedes initial breach detection but also complicates post-incident forensic analysis.
Exploiting Rule Limitations
SIEM systems depend on predefined rules for threat identification. Attackers meticulously analyze these rules, devising strategies to operate just below the detection threshold. For instance, if a SIEM rule triggers an alert after a specific number of failed login attempts, attackers might limit their attempts to stay undetected, probing the network without triggering alarms.
Key Findings from the USENIX Paper: Analyzing Evasion Techniques
The USENIX paper offers an in-depth examination of evasion strategies, underscoring the adaptability of cyber attackers. This analysis is vital for cybersecurity professionals to comprehend and counter these evolving threats.
Obfuscation Tactics
The paper elucidates how attackers employ obfuscation to mask their activities. In cyber attacks, this involves using heavily obfuscated code, challenging security tools and analysts in deciphering its purpose. Attackers may also generate numerous false positives to divert security teams, allowing real attacks to slip through unnoticed.
Rule-Specific Exploits
The paper highlights how attackers target specific weaknesses in SIEM rules. Each rule, designed to detect certain malicious activities, can have exploitable blind spots. Attackers leverage these by understanding the rule parameters and tailoring their attacks to avoid detection.
Adaptive Evasion Methods
The paper discusses the continuous adaptation of attackers in response to SIEM system updates. This ongoing adaptation signifies the dynamic nature of cyber threats, with attackers persistently developing methods to circumvent new detection techniques.
Proposed Solutions: Bolstering SIEM Effectiveness
The paper suggests several advanced solutions to counter sophisticated evasion techniques, thereby enhancing SIEM system effectiveness.
Dynamic Rule Creation
Adaptive SIEM rules, developed using machine learning algorithms, can anticipate and counter changing attack patterns. For example, a model trained on past network traffic data could identify new attack patterns, enabling dynamic rule creation for these threats.
Anomaly Detection through Machine Learning
Integrating machine learning for anomaly detection can significantly improve SIEM systems' detection capabilities. Machine learning algorithms can detect unusual network traffic patterns, indicating potential threats beyond the scope of static rules.
Regular System Updates and Audits
Frequent updates and audits of SIEM systems are crucial for addressing new vulnerabilities and ensuring optimal performance. Regular audits can identify configuration gaps or areas needing additional rules.
Collaborative Defense Strategies
Collaboration within the cybersecurity community can foster a more robust defense strategy. Sharing information about emerging threats and evasion techniques can aid in developing stronger SIEM rules and strategies.
Conclusion:
The USENIX paper provides invaluable insights into the challenges SIEM systems face in detecting evasion tactics. By understanding these challenges and implementing the suggested solutions, organizations can significantly enhance their cybersecurity posture, safeguarding their networks against sophisticated cyber threats.
Reference
[1] Uetz, R., & Schmid, M. (2023). Detecting Evasions of SIEM Rules in Enterprise Networks. USENIX. Retrieved from https://www.usenix.org/system/files/sec23winter-prepub-112-uetz.pdf